Links to all articles included in this series:
- The Beginning: Opening introduction to the series
- Browsers: What are they? How to make them a safer door to Web.
- Search Engines: The Good, Bad and Ugly. Understanding search results.
- Malware and Virus: What is Malware? – What is a Virus? What is the difference in their types? How to avoid them. How to know if you are infected. How to remove them.
- Phishing: Signs of phishing, phishing emails, phishing sites (you are here)
- Computer Optimization: Why is my computer slow? What can I do about it?
- Improving Your Email Experience
- Enjoying Your Computer: Social Media. Entertaining Activities. Educational Activities.
What Is Phishing?
Phishing is when “fraudsters”, who are basically just thieves and hackers, send fake emails or set up fake web sites that mimic the sign-in pages of trusted companies, such as eBay, your bank, your email page, Amazon, PayPal. Actually, the sites you trust the most are some of the best targets  for fraudsters because you believe them to be trustworthy, and they are, they would NEVER ask you to disclose your user name and password or any personal information. So if they do, there is an excellent chance you are not on a real site.
for fraudsters because you believe them to be trustworthy, and they are, they would NEVER ask you to disclose your user name and password or any personal information. So if they do, there is an excellent chance you are not on a real site.
This practice, sometimes referred to as “phishing” — is a play on the word “fishing” — because the fraudster is fishing for your private account information. Typically, fraudsters try to trick you into providing your user name and password so that they can gain access to an online account. Once they gain access, they can use your personal information to commit identity theft, charge your credit cards, empty your bank accounts, read your email, and lock you out of your online account by changing your password.
If you receive an email (or instant message) from anyone you don’t know directing you to sign in to a website, be careful! You may have received a phishing email with links to a phishing website. A phishing website (sometimes called a “spoofed” site) tries to steal your account password or other confidential information by tricking you into believing you’re on a legitimate website. You could even land on a phishing site by mistyping a URL (web address). Trust is what this is all about, and they know that. If they infect someone’s email the first thing they will do is send out an email to everyone listed in their contacts from the hacked site knowing you won’t hesitate to click and open a site from your best friend. Always be cautious, just because it has your mom’s address does not mean it is from her.
 Is that website legitimate? Don’t be fooled by a website that looks real. It’s easy for phishers to create websites that look like the genuine article, complete with the correct logo and other graphics of a trusted website. Important: If you’re at all unsure about a website, do not sign in. The safest thing to do is to close and then reopen your browser, and then type the URL into your browser’s URL bar. Typing the correct URL is the best way to be sure you’re not redirected to a spoofed site.
Is that website legitimate? Don’t be fooled by a website that looks real. It’s easy for phishers to create websites that look like the genuine article, complete with the correct logo and other graphics of a trusted website. Important: If you’re at all unsure about a website, do not sign in. The safest thing to do is to close and then reopen your browser, and then type the URL into your browser’s URL bar. Typing the correct URL is the best way to be sure you’re not redirected to a spoofed site.
Signs you May have Received a Phishing Email:
If you receive an email from a website or company urging you to provide confidential information, such as a password or Social Security number, you might be the target of a phishing scam. Phishing emails and phishing sites are only in action for a very short time, they continually develop new versions and reintroduce old versions. One place to see some great examples is the Consumer Fraud Reporting Site.
Unofficial “From” address. Look out for a sender’s email address that is similar to, but not the same as, a company’s official email address. Fraudsters often sign up for free email accounts with company names in them (such as “smallbusiness@yahoo.com”). These email addresses are meant to fool you. Official email from Yahoo! always comes from an “@yahoo-inc.com” email address.
Urgent action required. Fraudsters often include urgent “calls to action” to try to get you to react immediately. Be wary of emails containing phrases like “your account will be closed,” “your account has been compromised,” or “urgent action required.” The fraudster is taking advantage of your concern to trick you into providing confidential information.
Generic greeting. Fraudsters often send thousands of phishing emails at one time. They may have your email address, but they seldom have your name. Be skeptical of an email sent with a generic greeting such as “Dear Customer” or “Dear Member”.
Link to a fake web site. To trick you into disclosing your user name and password, fraudsters often include a link to a fake web site that looks like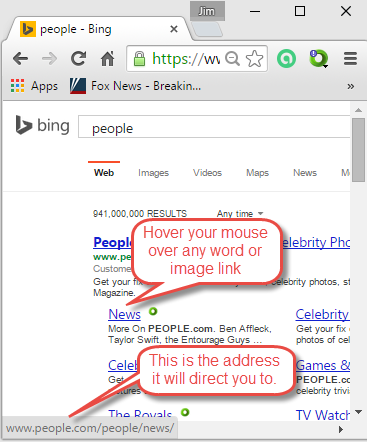 (sometimes exactly like) the sign-in page of a legitimate web site. Just because a site includes a company’s logo or looks like the real page doesn’t mean it is! Logos and the appearance of legitimate web sites are easy to copy.
(sometimes exactly like) the sign-in page of a legitimate web site. Just because a site includes a company’s logo or looks like the real page doesn’t mean it is! Logos and the appearance of legitimate web sites are easy to copy.
One tip is to check out the actual address prior to clicking on any link. Most browsers have a status bar on the bottom of the screen. As you move your mouse over the page, any links will appear in the status bar showing you the actual address you will reach. In the image to the right, I moved my mouse over the blue underlined News and you can see that I am actually going to go to www.people.com/people/news/ which is good, that is where I wanted to go. However, if you hover your mouse on the link below you will see that just because something is named one thing does not mean that is where you are going. <http://freemoney.com>
In the email, look out for: Links containing an official company name, but in the wrong location. For example: “https://www.yahoo.com is a fake address that doesn’t go to a real Yahoo! web site. A real Yahoo! web address has a forward slash (“/”) after “yahoo.com” — for example, “https://www.yahoo.com/” or “https://login.yahoo.com/.”
Legitimate links mixed with fake links. Fraudsters sometimes include authentic links in their spoof pages, such as to the genuine privacy policy and terms of service pages for the site they’re mimicking. These authentic links are mixed in with links to a fake phishing web site in order to make the spoof site appear more realistic.
- And look for these other indicators that an email might not be trustworthy:
- Spelling errors, poor grammar, or inferior graphics.
- Requests for personal information such as your password, Social Security number, or bank account or credit card number. Legitimate companies will never ask you to verify or provide confidential information in an unsolicited email.
- Attachments (which might contain viruses or keystroke loggers, which record what you type).
Signs you May be on a Phishing Site:
Phishers are becoming more and more sophisticated in designing their phony websites, follow these steps if you think you’ve been phished. There’s no surefire way to know if you’re on a phishing site, but here are some hints that can help you distinguish a real website from a phishing site:
Check the Web address. Just because the address looks OK, don’t assume you’re on a legitimate site. Look in your browser’s URL bar for these signs that you may be on a phishing site:
- Incorrect company name. Often the web address of a phishing site looks correct but actually contains a common misspelling of the company name or a character or symbol before or after the company name. Look for tricks such as substituting the number “1” for the letter “l” in a Web address (for example, www.paypa1.com instead of www.paypal.com).
- http;// vs https://. “http://” at the start of the address on sign-in pages. Secure pages must have the “S: after http. Even if you type in http://yahoo.com it should automatically change to https://. If it does not you are not on a secure page.
- A missing forward slash. To verify that you’re on a legitimate Yahoo site, make sure a forward slash ( / ) appears after “yahoo.com” in the URL bar, for example, “https://www.yahoo.com” is a fake website address. https://www.yahoo.com/ is a real address.
- Be leery of pop-ups. Be careful if you’re sent to a website that immediately displays a pop-up window asking you to enter your username and password. Phishing scams may direct you to a legitimate website and then use a pop-up to gain your account information.
Great Safety TIP
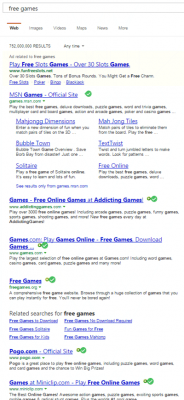
Use a Web browser with antiphishing detection. Internet Explorer, Mozilla Firefox, Web browsers have free add-ons (or “plugins”) that can help you detect phishing sites before you even click on them. Plugins like WOT mentioned in an earlier post. Many antivirus or anti-malware programs have a web security feature that will scan webpages for trustworthiness prior to you clicking on them. In the image to the left, I performed a search for free games. In the adjacent image, you can see that several of the sites have the green doughnut from the WOT program and the green circle with a check mark for the Avast program. The first item on the list does not and I would not click on that link.
In an upcoming post, we will discuss many aspects of Email. How to make your Hotmail, Gmail, or your IPP email and others come right to your computer without having to visit their site. How to set rules to organize your mail into folders and reduce spam.
Terminology
Spoofing On webpages it is when someone or a program successfully masquerades as the real webpage. In E-mail addressing, it is when the email you receive is not actually from the person you believe it to be.
HTTPS Stands for "HyperText Transport Protocol Secure" It is the same as http but uses SSL (secure socket layer) to ensure security over the web.
[Credits: https://safety.yahoo.com/Security/PHISHING-SITE.html]
