Overview
Many DCT readers use the open-source Bitwarden to manage their passwords. I have been using the premium version of Bitwarden for years, while Jim Hillier recommends the free version of Bitwarden if you do not need the premium features. Bitwarden is a secure password manager by default, but in a few minutes, we can increase Bitwarden’s security with a settings change.
What Is A KDF?
The most important factor in a password manager’s security is the master password. To learn how to properly create a password for a password manager, see the Ultimate Guide To Create A Master Password – Part 1 and Part 2
Another important factor in cloud-based password managers is the KDF. All cloud-based password managers hash your data before uploading it to their servers. This process is called the Key Derivation Function or KDF. The number of times the hashing is done is called iterations. The more iterations, the stronger the security because it slows down potential hackers.
In December 2022, I reported on the LastPass breach. LastPass had (and still has) many issues, but one issue was allowing low iterations (1 or 500) on their KDF. LastPass uses the standard PBKDF2 (Password-Based Key Derivation Function 2). Bitwarden also uses the PBKDF2 KDF, but as of this writing, with a more secure minimum of 600,000 iterations.
Earlier this year, Bitwarden added the option to use the newer and stronger Argon2 KDF. In 2015, the Argon2 KDF won the Password Hashing Competition. There are three versions. Argon2d maximizes resistance to GPU cracking attacks. Argon2i is optimized to resist side-channel attacks. While Argon2id is a hybrid version used in Bitwarden. It follows the Argon2i approach for the first half of the memory pass and the Argon2d approach for subsequent passes.
I will show you how to upgrade Bitwarden to the Argon2id KDF.
Precaution
As a precaution before making any changes to the KDF settings, you should make a copy of your Bitwarden vault. After logging into your Bitwarden.com account, select Tools then Export vault, and select a file format (I recommend selecting either JSON or JSON encrypted format since these will save everything while a CSV format will not). Now, select Confirm Format (Bitwarden will ask for your password again) and save the file to your computer.
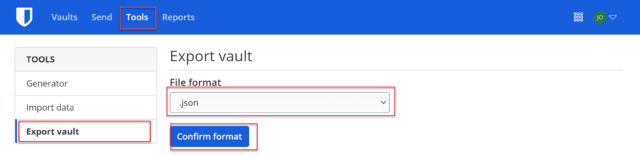
(Ed note: I made these changes a while back on an older version of Bitwarden and would have lost all my passwords if I had not made a backup as John points out. I implore you all to make a backup before trying this. You will need the latest version of Bitwarden.)
Change KDF Setting
To change the KDF setting, we need to go to the Profile button in the upper right corner and select Account settings.
Default – OK
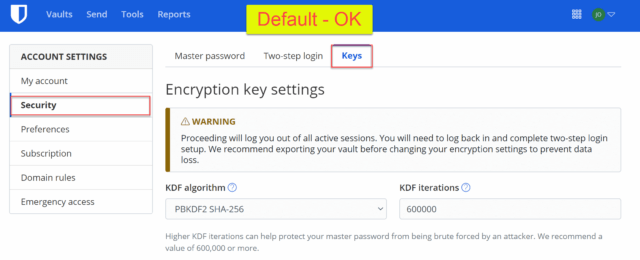
In the left column, under ACCOUNT SETTINGS, select Security. In the right pane, select Keys. The default KDF algorithm is PBKDF2 SHA-256 with an iteration of 600,000. These KDF settings are OK. But we can do better.
Good
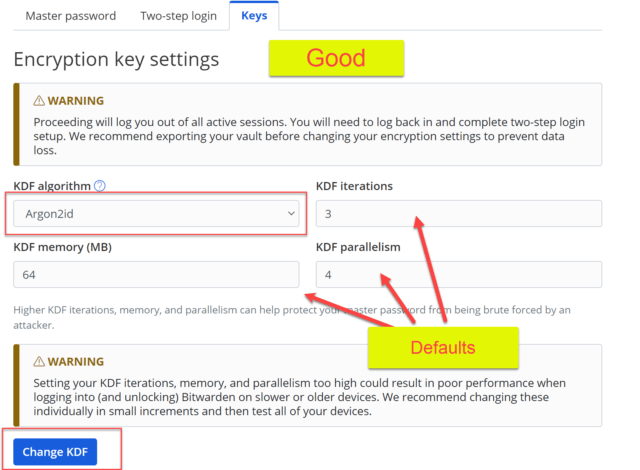
To select the superior Argon2id KDF, select Argon2id from the KDF algorithm drop-down box and select the Change KDF button to save the settings. A warning appears that we will be logged out and will need to log back in. Enter your password and select Change KDF. These are the default settings and will improve our security to Good. The following will be set:
- KDF algorithm = Argon2id
- KDF memory (MB) = 64
- KDF iterations = 3
- KDF parallelism = 4
When logging back in, note how long it takes.
Better
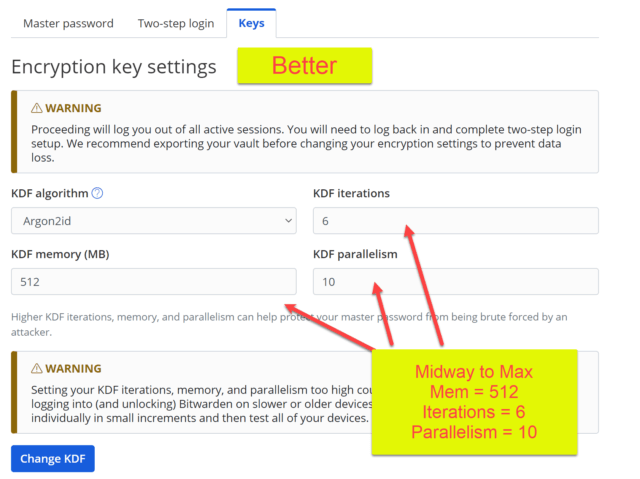
To improve on the default Argon2id KDF settings, we will repeat the steps above, but change the settings to those listed below. We will choose settings midway to the maximum settings. This will provide better security than the default settings above.
- KDF algorithm = Argon2id
- KDF memory (MB) = 512
- KDF iterations = 6
- KDF parallelism = 10
When logging back in, note how long it takes.
Best
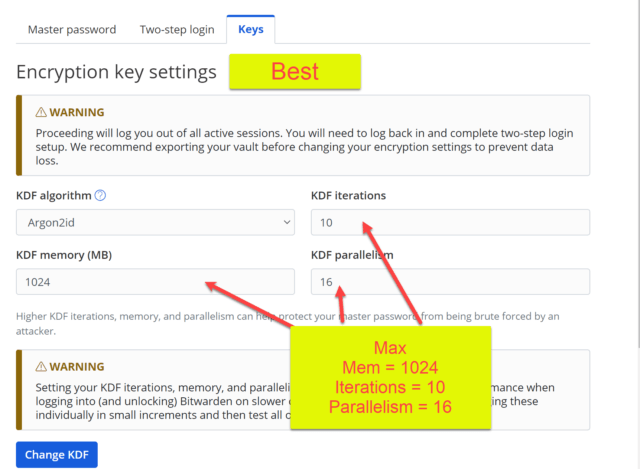
Finally, to give us the best Argon2id KDF security, we will repeat the steps above, but increase the settings to the maximums listed below.
- KDF algorithm = Argon2id
- KDF memory (MB) = 1024
- KDF iterations = 10
- KDF parallelism = 16
When logging back in, note how long it takes.
Login Time
KDF is computationally intensive by design. The time it takes to log in is directly related to the performance of the hardware we are using to log in. Older, less powerful hardware will take longer than newer, more powerful hardware. You should test this on the least powerful device you regularly use to log in to Bitwarden. Choose the settings that give you the best balance between security and speed.
The computer I tested this on is a relatively new 13th-generation Intel i7. My login speeds were as follows:
- Good = 1.5 seconds.
- Better = 5 seconds.
- Best = 10 seconds.
If this was the only hardware I was using to log in to Bitwarden, I would choose the Best option. However, if I was using a slow computer or phone and it took many minutes to log in with the Best settings, I would choose one of the lower settings.
—
