This is Part 2 of a 2-Part article. Please be sure to read Part 1 first:
At the end of Part 1, I posed the questions: How do you create a strong password? How do you measure password strength? How strong is strong enough? Please read on to discover how.
Create A Strong Password
You could use a random password generator, but it will produce a password like MYc^DHxWif*wjKq!EyHDSt3b which, while strong, is too complex to memorize and enter. The solution is to use a randomly generated passphrase. A passphrase is a password that uses a string of words. A passphrase is easier to type and remember than a password.
In Part 1, I gave an example of how human weakness results in lower password entropy. The same is true for phrases. Research shows that “users aren’t able to choose phrases made of completely random words, but are influenced by the probability of a phrase occurring in natural language.” In other words, human-chosen passphrases don’t contain that much entropy. Your brain uses common idioms, grammar rules, and thought patterns that reduce randomness and entropy.
Diceware
Diceware is a method to create passphrases using dice. For each word in the passphrase, five dice rolls are required. The numbers that come up in the rolls are combined into a five-digit number, e.g. 43146. This number is then used to look up a word in a 7,776-word list such as the EFF long word list.
Online Passphrase Generators
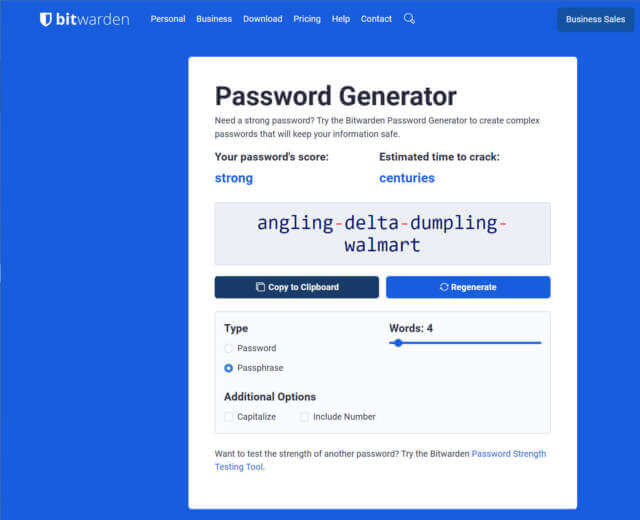
Bitwarden’s passphrase generator uses this method with a 7,766-word list. Each word will give approximately 13 bits of entropy (1 * log2(7766) = 12.922 ).
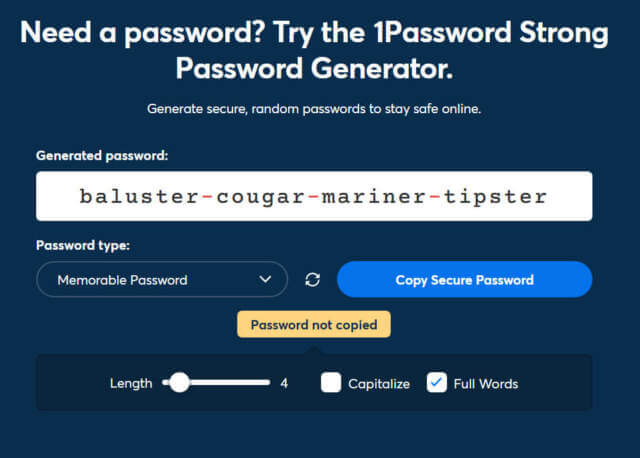
1Password’s passphrase generator uses an 18,000-word list. Each word will give 14.135 bits of entropy.
The Passphrase-generator.com generator is based on a 51,924-word list (15.664 bits of entropy per word).
Modifications
A four-word randomly generated passphrase is considered strong. Five or six words are even stronger. Once you have your passphrase as a base, you can optionally modify it to make it stronger, while keeping it easy to remember and quick to type.
hungrily shrine froth unopened
Add random numbers:
- hungrily shrine froth 54362 unopened
- hungrily5shrine5froth5unopened
- hungrily shrine froth unopened54362
Add special characters:
- hungrily–shrine–froth–unopened
- hungrily#shrine#froth#unopened
- hungrily shrine froth unopened,.?$%
Capitalize letters. Avoid adding capitalization to the first letter of a word since this is a common pattern and does not add much entropy:
- hunGrily shriNe frOth unoPened
- hungrily SHRINE froth unopened
- huNGrily shrine froth unopenED
Add padding. Padding is one, two, or three characters repeated a few times to add 10-20 characters. By itself, it is a very weak technique, but adding to an already strong passphrase increases the length and is quick to type – significantly increasing entropy if a hacker is forced into a brute-force search.
- ………. hungrily shrine froth unopened
- hungrily shrine froth nmnmnmnmnmnm unopened
- hungrily shrine froth unopened a;’a;’a;’a;’a;’a;’
These modifications can be combined. For example, add numbers and special characters in your padding. As you develop your modifications, design them so that they can be entered quickly.
Estimate A Password’s Real Entropy
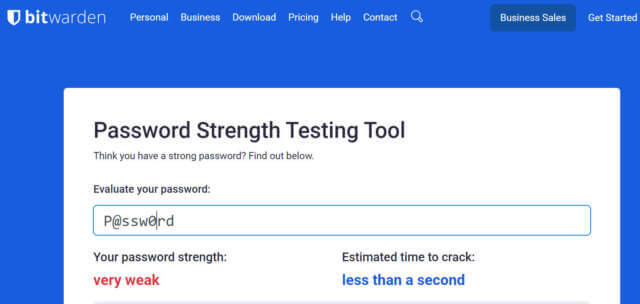
Many password strength calculators only measure the password based on its length and whether it contains elements from the character pools. In the example from Part 1, UK^aR2$b and P@ssw0rd both have the same entropy but P@ssw0rd would be cracked in milliseconds. To get around this, many companies, including Bitwarden and Dropbox, use the open-source zxcvbn, a password strength estimator inspired by password crackers. It estimates password strength through pattern matching, recognizing common passwords, common first and last names, popular English words from Wikipedia and US television and movies, and other common patterns like dates, repeats (aaa), sequences (abcd), keyboard patterns (qwertyuiop), and l33t speak.
Many companies run zxcvbn and give a password strength.
Although good, these companies don’t provide a numeric entropy number. Since we do not know the criteria they use, they might consider a password strong that we do not. For example, based on my tests, Bitwarden considers a password strong at around 30 bits of entropy.
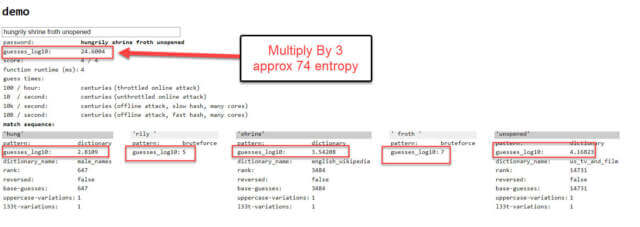
There is a test version of zxcvbn that does provide a score.
The total guesses_log10 value in the result can give an approximation of a password’s real entropy in bits by multiplying by 3. In the example above, 24.6004 would indicate a password entropy of approximately 74 bits (24.6004 x 3 = 73.8012). Note that the test site was written in 2016 and is not maintained. Hackers will use more recent dictionaries and better patterns than those loaded in the test version, so the entropy value may be a little high.
How Strong
A password manager’s master password’s entropy for the average person should be above 60 bits. A high-target individual should have a password entropy above 70 bits, and a nation-state target (a politician, dissident, etc.) should have a password entropy above 80 bits.
| Bits of Entropy | Strength | Suitability |
| < 28 bits | Very Weak | Might keep out family members |
| 28 – 35 bits | Weak | Should keep out most people, suitable for desktop login passwords |
| 35 – 59 bits | Reasonable | Fairly secure password suitable for network and company passwords |
| 60 – 127 bits | Strong | Suitable for a password manager’s Master Password |
| 128+ bits | Very Strong | Probably overkill |
Conclusion
Learning a passphrase may seem difficult, but it is not. It may take a few days or a week of practice, but it is the only password you need to remember. Write your password down on a piece of paper, refer to it as necessary until you have memorized it, and then destroy or securely store the piece of paper.
My passphrase-based password has an entropy of around 80 bits and is easy to enter taking me less than 10 seconds. I have used the same password for over five years. It protects over 400 unique and secure passwords in my password manager. Let me know in the comments if you have any questions.
- Ultimate Guide To Create A Master Password – Part 1
- Ultimate Guide To Create A Master Password – Part 2 ⬅ You are here


I came across another zxcvbn site that offers a demo version. It is a rewrite of zxcvbn in TypeScript. zxcvbn-ts. It states it has:
– updated dictionaries (generally more words and dictionaries that are up-to-date)
– bug fixes
– more keyboard layouts
– more matchers
https://zxcvbn-ts.github.io/zxcvbn/demo/
John, I deal with people everyday who have problems with passwords. They are not good managers. So, they may set a good password for some site and even write it down somewhere. But when they need it, they cannot readily find it.
I steer these people to one of two directions. 1st I encourage them to use a password manager (I start them with Keepass because it is free. If they want something more sophisticated, they can seek it later.).
If that is too much for them to manage, I show them a simple, but effective technique of using “one” password for everything. I definitely discourage this with sites involving personal information or finance.
The method goes like this, create a relatively strong password like “9H5gex7#5qP8″ and place it on a card they can carry with them. When they are setting up a login for a site add the 1st letter of the site name to the beginning of the password and add the last letter of the site name to the end of the password. As long as they know the base password they should be able to guess the site password.
For example. to set up a password for DavesComputerTips, they would enter their email address as the ID and the password would be”D9H5gex7#5qP8s”.
Hi Tom L, thanks for the comment.
Yes, this post on how to create a strong password for a password manager is specifically geared toward that first group. Unfortunately, many do not take their security seriously. They take the view that a data breach can not affect them. It is similar to views on data backup. Many do not take backing up their data seriously until they have suffered a data loss, due for example, to a dead hard drive. But, with breaches happening every day taking one’s security is important.
Concerning that second group that uses the formula method, I went over some of the pros and cons of that method in a reply to a comment from “Been There” to Part 1 of this post and why it is not really that “effective”. At least, in your example, it looks like the base formula has some randomness in it. Research shows that most people will not choose randomness. They will use pets’ names, family members’ DOB, words associated with their work, old addresses or schools attended, vacation destinations they have posted to social sites, or what they think is random like something associated with them in a public database (car license or registration number, etc.). With techniques like spidering and those mentioned in this post, this is not a good strategy.
We can only offer good advice, but people have the choice not to follow it. Many don’t follow it because they do not have the knowledge of why the advice is good. Maybe, with some of the details I’ve addressed in this article, you can convince more of those inclined to be in that second group to be in the first group.