Security is a number one topic these days. Heck, it has been for decades now. Adding any new layer of security to your computer system seems like a good idea. Enter Controlled Folder Access. Introduced in Windows 1709, you can enable this security feature to help protect your files from ransomware and any other malware that the scumbags of the earth would try to foist upon you. And there are a lot of scumbags out there. If you use a 10% rule of bad guys versus good guys ratio (I’m being generous), that means there are ~800,000,000 scumbags surrounding us. That’s quite a few. Controlled Folder Access isn’t enabled by default so this Quick Tips article will show you how to turn this feature on in Windows 10.
- Check out all Windows 10 Quick Tips articles
Getting To The Setting
First off, if you are using a third-party antivirus program, then Windows Defender should not be running. Without it running, I would say that Controlled Folder Access will not be available to you. You don’t want to have two AV programs running at the same time– they conflict with each other and can cause instability and poor responsiveness of your system. In other words, slow-downs.
Moving on…
- Use Windows key + I to open the Settings App
- Choose Update & Security
- In the left pane, choose Windows Security
- Choose Virus & threat protection
- In the window that opens, scroll down and choose Manage ransomware protection (it’s a link in the Ransomware protection section)
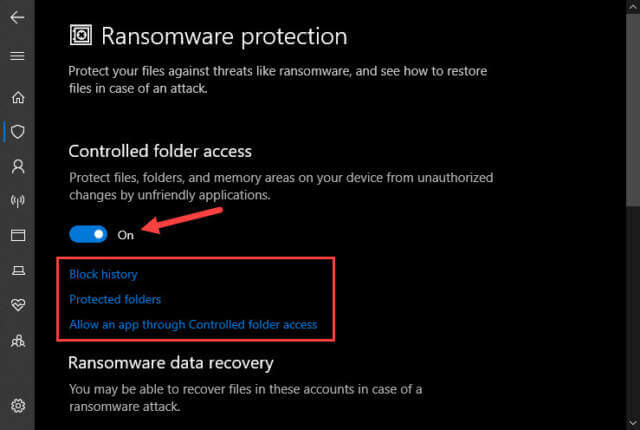
That should bring you here:
Once you enable the Controlled Folder Access feature, the effects are immediate. Windows Defender will start monitoring changes in real-time to the default protected folders and will block any disallowed programs that try to change them. This can be unpleasant for those who have never used a firewall before, and even for those of us who have.
Note: Windows chooses some software that will have access to these folders by default. If it didn’t, you would become a basket case in no time and in need of immediate psychiatric care.
Incessant Blocks
Here’s what happens. A piece of software that you’ve been using for years suddenly can’t access the Pictures folder. Windows Defender will notify you that a program has tried to alter and/or access this protected folder. Your only recourse is to add it to a list of software that is allowed to access this particular folder. If you don’t, then it won’t work anymore in the way you are accustomed to. This can be a real pain in the neck in the beginning (thank you a large pile, scumbags) but it is a necessary evil if you want to add this extra protection to your system.
Thankfully, you only have to tell Windows one time and it will “remember” your choices. The notifications will become less frequent as time goes on as Windows “learns” which programs you want to allow. After a time, you will forget you ever enabled this feature and things should return to near normal. I say “near” normal because if you install new programs then, well…
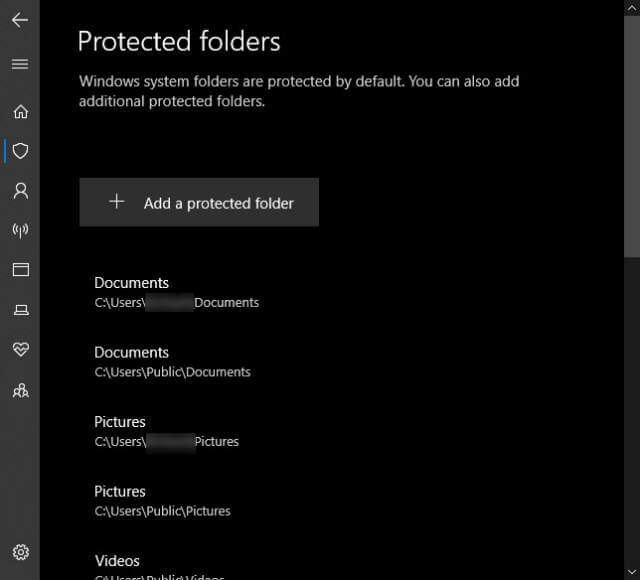
Protected Folders
Windows Defender protects some folders by default. You can see which ones by clicking the Protected folders link shown in the previous image. That will bring you here:
You can click on a folder to remove it from the list and you can Add a protected folder, too. This gives you some control over the control.
Note: I’ve read that some folders cannot be removed. So much for all that control… bliss can sometimes die quickly.
Conclusions
This is a great way to further protect yourself from the aforementioned slimy, despicable, waste-of-human-flesh, scumbags. At first, it can be a truly cumbersome nuisance but rest assured, in the end, you will have secured your system one bit more. And that’s a good thing.
As always, if you have any helpful suggestions, comments or questions, please share them with us,
Richard
—

I like this, but it is just a start. I would like to see you drill down on ‘Total Trust’ and things like SaaS. At least give you take. Here is the latest Zero Trust report.
https://clouddamcdnprodep.azureedge.net/gdc/gdcm1YCHx/original?ocid=eml_pg273872_gdc_comm_mw&mkt_tok=MTU3LUdRRS0zODIAAAF9TR–pNPk1kxJCJ-dsJ-upmZJxLFGd3VaAO5_brItzOHC3reePVJrqF5AtlVg-J_KYbvSZhy4723zU5kdrhBEoZGrMKTScHM2lWcmMHbUp6Q4Yx4Ei6glyjRJ
(Ed Note: The above link will download a PDF file.)
Hi Charles,
I will have to take a look at this a little later but thank you for the link.
I’ll get back to you,
Richard
Hi Charles,
Just my thoughts:
An old saying is that no matter how tall a wall you build, someone is going to find a way to scale it. (Mexico?) And that’s also true when it comes to computer security measures. So far, what we’ve been doing is playing a game of whack-a-mole. And we’re losing.
Someone finds a way to breach a system, and everyone scrambles to plug the hole. This game is played ad infinitum and based on current observations, this method does not work. The good guys are always behind. Think of poor Hans Brinker, except with many holes to plug all at once.
Despite the ability to add layer upon layer of protection, the bad guys are still sneaking into our computers and disrupting important health care and infrastructure systems on a massive scale. Just like Mother Nature, they have no conscience. Infecting these systems is tantamount to kidnapping and murder and should be punished as such.
I’ve been preaching for decades to set up and maintain a solid backup regimen. If done properly, one’s computer can be bulletproof. Let’s use a recent example with that Colonial Pipeline company. They got hit with ransomware. Then they paid the kidnappers 4.5 billion dollars. Then they realized that using their backups would be quicker than waiting for the decryption of their files. There go four and a half billion dollars right out the window. Poof! Why did they bother to make backups if they weren’t going to use them? Did they really believe that a decryption key was going to magically restore their system to standard operating normalcy in the blink of an eye? It probably took many hours upon hours to encrypt it all in the first place.
Backups can protect you from all sorts of malware but there is one form that they can’t protect you from. Phishing.
The weakest link in any security system is the users themselves. There is no protection against that other than to be an educated user who doesn’t click on everything they see.
The Zero Trust report you linked to seems to be trying to tackle this problem by limiting access with roles/permissions. This is a proactive approach and that’s certainly better than the reactive methods we are using today. Many if not most users today need protection from themselves. I personally know people who haven’t backed up their systems in decades. Glory be! I wouldn’t be able to sleep. Then, of course, there would be the inevitable phone call with a distressed voice on the other end of the line. “Richard! I can’t access my Word documents!”
I could go on for a long time on this subject but the Comment section is not the right place for it.
I hope I shared something useful,
Richard
100%
I’m very old school. Multiple incremented Back-Ups. Also, a lot of time is wasted on preaching to poor dolts like me who don’t have much to steal. Those who might lock you out of your own data don’t target this user and most of them are targeted. SO, other Virus issues are more pertinent in such cases.
Incremental backups are not my first choice.
Don’t have much to steal? How many accounts do you have online? Is it OK to have those compromised?
With apologies to Richard for jumping in…
This is nothing new. While the PDF report is quite complex and more geared toward the corporate side, the basic tenet… “trust no-one, verify everything” is something I’ve been advocating for years.
If every home PC user were to follow this basic principle it would inevitably save them a lot of grief.
Don’t ever think you will offend me by jumping in. I love other people’s opinions. Just be aware I am likely to respond! On this one, I am a total paranoid freak when it comes to Electronics Security. Too many innocent people have had their whole lives destroyed and even knowing what I know, I have fallen to the guile of these criminals more than once. And about this PDF being VERY deep and corp oriented, that is why I thought that this might be a good place to explain it for the common user and for personal usage.