A recent analysis of Chrome browser extensions performed by USENIX, The Advanced Computer Systems Association, has revealed a relatively high number of malicious and suspicious extensions, many of which have been downloaded by millions of users.
In a PDF document issued by USENIX detailing their findings, the researchers noted:
The amount of critical and private data that web browsers mediate continues to increase, and naturally this data has become a target for criminals. In addition, the web’s advertising ecosystem offers opportunities to profit by manipulating a user’s everyday browsing behavior. As a result, malicious browser extensions have become a new threat, as criminals realize the potential to monetize a victim’s web browsing session and readily access web-related content and private data.
USENIX utilized a dynamic analysis system of their own creation called Hulk (which flushes out an extensions’ malicious behavior) to analyze 48,332 Chrome extensions.
“First, Hulk leverages HoneyPages, which are dynamic pages that adapt to an extension’s expectations in web page structure and content,” USENIX explains. “Second, Hulk employs a fuzzer to drive the numerous event handlers that modern extensions heavily rely upon.”
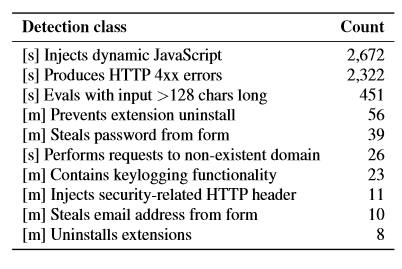
Of the 48,332 extensions analyzed, 130 were found to be outright malicious while a further 4712 were found to be “suspicious”. Among the 130 malicious extensions, USENIX identified behavior which included; ad manipulation, affiliate fraud, information theft, and social network abuse. Here is USENIX’s breakdown of both malicious and suspicious extensions by detection types:
*An extension might have more than one detection.
*[m] denotes malicious detections, [s] denotes suspicious detections.
The researchers also include a number of recommendations in the paper which, hopefully, Google will heed.
- The USENIX paper can be downloaded in full here: Hulk: Eliciting Malicious Behavior in Browser Extensions

Hello Dave, I know there are alot of browser out there, However I was hoping you can recommend the best one to use. I currently use the Windows 7 operating system.
Hi Karla – Most people have a favorite browser and different opinions on which browser is best… choice is entirely subjective.
There are 3 main browsers; Internet Explorer (which comes from Microsoft as part of the operating system), Firefox ( which is renowned for its variety of extensions), and Chrome (which comes from Google and is reputed to be the fastest of the three).
My own favorite is Firefox but, honestly, there isn’t much to pick between them. For ‘average’ users who just tend to browse around the usual sites, Internet Explorer is fine and doesn’t require any further download or installation.
Cheers… Jim
Hi Karla: Jim is of course right (I have to say that because he’s the Editor) – but I think there is no contest here, and I use four browsers (including Opera) regularly. The right answer is – Firefox. Why?
1) It’s the fastest (actually, in tests, Firefox and Chrome often alternate between first and second place);
2) It has a really good bookmarking system and editor, and good synchronisation of the bookmarks, tabs, passwords, history and add-ons. You just sign up to a free Firefox account, and then you can automatically sync across your other devices, like Firefox on Android, or any other PCs or tablets you have. If you have to reinstall Firefox, say on a new machine, you just set up sync and all your stuff comes back pretty much automatically;
3) You can easily set up AdBlock Plus so you don’t get held up or distracted by unwanted page ads;
4) It’s easy to set up LastPass to control all your passwords (basic LastPass is free, but it’s well worth a few dollars a year to get the premium version, which I have);
5) You can personalise it to a high degree, with different coloured theme-addons and styles.
6) Mozilla Firefox is a great open-source community if you want to get involved.
The only drawback to watch out for is that new users tend to over-enthusiastically install too many add-ons, which may produce a slow and cluttered result, but fortunately that’s very easy to correct. Here’s my guide to my own minimalist Firefox configuration from my post on the Mozilla support forum: https://support.mozilla.org/en-US/questions/1010957.
I think the most logical answer is Internet Explorer, I have never had an issue with Internet Explorer. Correct me if I am wrong but will Windows Update download through any other browser except IE? Daniel.
Daniel – Windows Update has not relied on Internet Explorer since XP. In Vista, Windows 7. and Windows 8, Windows Updates is a completely independent process, not reliant on any browser.
Cheers… Jim
Is there a way to scan my currently installed Chrome extensions for these vulnerabilities?
Is there a published list of the malicious (or suspicious) extensions?
I did not see that information in the USENIX report.
Unfortunately the study paper does not name the suspect installations. I thought it was a rather strange omission myself Bob, maybe something to do with legal repercussions.
As far as scanning existing extensions is concerned, have a look here: http://lifehacker.com/extension-defender-roots-out-adware-extensions-in-chrom-1508612000
Seems a tad incongruous, installing an extension to check on extensions. Anyway, the developer of the software mentioned in the article also maintains a website that lists all of the extensions included in the software’s database: https://www.extensiondefender.com/database-chrome.php
Karla,
You are getting answers that are out of date. Internet Explorer is so bad that, for Windows 10, Microsoft is using its new browser called Edge. It’s so backwards compatible that it covers two decades of stuff slowing it down enormously. It also uses Active-X controls which are an invitation for disaster. Edge doesn’t have either of those flaws. I have always loved Firefox (by Mozilla) BUT Microsoft is going to stop allowing the use of Firefox’s extensions on Windows PCs. In addition Firefox’s market share has been plummeting and I don’t know how much longer they can keep it going. They have already gotten rid of Thunderbird which was its wonderful email system and absolutely everything else and are hoping to hang on for dear life. That makes it close to useless. That leaves Opera and Chrome. Opera has a tiny market share despite everything its developers can do to make it more popular.
In the United States and across the world Google’s browser, Chrome, is the overwhelming favorite. Once you have the password for Chrome, that password works for its email system Gmail which is by far the best email system in existence. That password also works for YouTube since Google owns YouTube. I have been using Firefox and Chrome but with the passage of time I have gradually been using Chrome alone. I highly recommend you do the same. NO – I don’t work for Google. I’m a retired mathematician.