What is TOR?
Tor is a free software browser that is designed to defend against traffic analysis. Traffic analysis is a fancy way of saying that there are individuals and organizations who monitor your internet traffic and use that information in many ways. By knowing where the traffic originates and where it ends up, others can track your behavior and your interests.
Traffic analysis is a fancy way of saying that there are individuals and organizations who monitor your internet traffic and use that information in many ways. By knowing where the traffic originates and where it ends up, others can track your behavior and your interests.
When you use the internet you generate data packets that have two parts. The first part is the data payload and the second is the header that is used for routing. Basically, the data payload is the actual data being transmitted. For example, the message in your email, the webpage you view or the video you receive or send. Most of this data information may be encrypted but the header may still reveal what you’re doing. Sometimes even what you are saying. That is because traffic analysis uses the header part. The header contains the source of the transmission, where the data is being sent, how large the file is and many other interesting aspects that may help someone determine who you are and what you are actually doing.
If you are one of those growing number of individuals that are worried about your online privacy or safety this could be a problem because many ISPs monitor every site, you visit and every email you send. They then sell that data to interested parties that help them market more efficiently. However, there are others that monitor internet traffic for more nefarious reasons. Censorship, criminal activity and spying are some reasons that can potentially threaten your personal safety and in some countries even your freedom.
Hiding your identity on the internet is never a bad idea but using the Tor browser is one step in the right directions. I say one step because by itself, it is not flawless. Serious attempts to track relay activity can lead, over time, to a hacker, ISP (Internet Service Provider) or government agency knowing the sender. That is why experienced users use several layers of protections like proxies and VPNs. See my follow up post on VPNs.
Downloading TOR
To get Tor visit their website and download directly from there. Not a third party website. After downloading the install Program, select the destination directory and click install. Once the install wizard is completed the Tor start screen will appear.
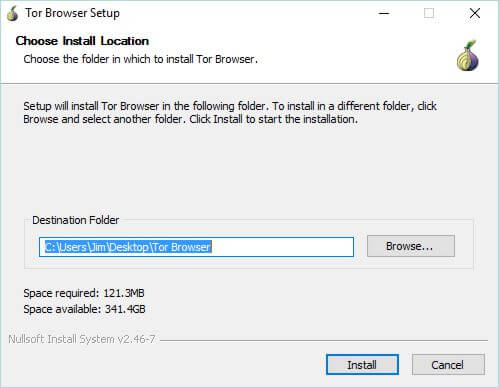
What you ultimately use depends on your reasons for using the internet. If you are discussing topics that you do not want to share with the world, having a safe and anonymous way to communicate can keep your private life private and Tor will most likely fill that bill. In the following examples I believe using the Tor browser or Tor coupled with a free proxy is all you would need.
How TOR Works
 Tor stands for “The Onion Router” in reference to hiding behind layers like the layers of an Onion. Tor bounces your internet traffic off of several relays so it is very difficult for anyone to know where the original signal started or learn your internet habits.
Tor stands for “The Onion Router” in reference to hiding behind layers like the layers of an Onion. Tor bounces your internet traffic off of several relays so it is very difficult for anyone to know where the original signal started or learn your internet habits.
Tor is a free software browser and an open network of volunteer operated servers that allows people to use the internet privately. Once you open Tor it will connect to the internet through a series of tunnels instead of making a direct connection to your ISP like a regular browser would do. This will prevent websites from tracking you and allow you to access websites you might not be able to without Tor. It acts like a censorship circumvention tool because if a website does not know the origin of someone accessing the site it does not know if the request is from a restricted site.
Unfortunately, software like Tor, Proxies and VPNs are used for a host of very bad reasons. Many drug transactions, downloading of pirated media or software, illegal pornography and others are performed under the cover of anonymity afforded by this type of software. I cannot stress enough the seriousness and consequences for using software for illegal uses. This post in no way condones this practice and promotes only the legitimate reasons for using this type of software.
There are a lot of very legitimate reasons for surfing the internet anonymously. Let’s say you are part of a cancer or AIDs support site or even a member in a chat room talking about sensitive topics like civil liberties, or being a victim of cyber bullying, you may feel the need to converse with others openly without your identity being known. Similar to the anonymity afforded to Alcoholic Anonymous members. Some e-commerce sites might base your interest rates on the country of origin. Searching for information about bankruptcy may negatively affect your credit score. You might want to notify the authorities or news service about an illegal activity but do not want your identity known. Similar to the www.wetip.com site.
In the above examples using a Tor browser and perhaps adding a proxy will allow you all the anonymity you need.
However, Tor is said to have been compromised in some situations and while it does do an admirable job in keeping you safe I would not bet my life on it. That is exactly what you might be doing if you live in a country which prohibits the freedoms we have in the USA. For example, if you live in North Korea or China, there are several, probably most, websites that you are not allowed to visit. If you are a corporate whistleblower and really want to keep your name out of it.
According to Tor, journalists use Tor to communicate with whistleblowers and dissidents. If you are a person who works overseas, it allows you to connect to your company website without the country you are working in knowing or being able to block your transmissions.
The Dark Web vs The Deep Web
 Most of us use a part of the internet that is often referred to as the Surface Web. This part of the web is accessed by search engines like Google, Bing, Yahoo, etc. (for a very nice understanding how search engines work click here) However, the Deep Web and the small part of the Deep Web known as the Dark Web are much larger in comparison and are not searched by the above mentioned search engines. In fact, the Deep Web is so big, nobody can put a clear number on how big it really is, hundreds or thousands of times bigger that the internet we normally use.
Most of us use a part of the internet that is often referred to as the Surface Web. This part of the web is accessed by search engines like Google, Bing, Yahoo, etc. (for a very nice understanding how search engines work click here) However, the Deep Web and the small part of the Deep Web known as the Dark Web are much larger in comparison and are not searched by the above mentioned search engines. In fact, the Deep Web is so big, nobody can put a clear number on how big it really is, hundreds or thousands of times bigger that the internet we normally use.
The Deep Web is in many cases just a bunch of information that is typically not accessible because it is a non-standard DNS or hidden behind search boxes of other sites. A perfect example is an unpublished post. When I write this article it is absolutely on the internet, in fact it has its own unique web address, but it is in no way searchable. Only if you had the unique address would you be able to access it.
The Deep Web/Dark Web
Reaching and even searching the Deep Web and therefor the part that is the Dark Web is available to the Tor browser. That is not in any way what this post is about. Don’t do it! In my opinion there is no good reason for the average person being on the Dark Web. Surfing the clear web with Tor and being able to search with anonymity is the only reason for this post. Remember: It is not illegal to search the web anonymously, it is illegal to perform illegal activities on the internet whether you are using the internet anonymously or not.
Other Programs
The TOR Browser is not the only program that provides anonymity over the internet. Programs Like Freenet and I2P allow users to communicate with each other while keeping out the general public. Both are in my opinion a little harder to work with than Tor but for using in chat rooms they are very effective. 
Proxies and VPN
In this post I mentioned the use of Proxies and VPN. I will be explaining VPNs in my next post but Proxies are simply a server or another computer which serves as a relay hub to enable your internet request to be processed from other than your IP address.
Summary
When the internet was developed security was not considered. Things have evolved over time and while I am not trying to be an alarmist, the Web can be a very dangerous place in some instances. Everyone has the right to surf the internet and feel safe about doing so. These programs can help achieve that. They do not offer the full security of a VPN but they are solid programs made by people who want to keep the internet safe for all of us.
- Further reading: 5 Best Reasons For Using A VPN
Jim

Seems I’m not able to have posts accepted while using TOR. Here’s what I tried to post.
Thanks for the article Jim. Trying it out right now. So let me see if I get this right. The Ghostery addon can block tracking, while TOR totally prevents trackers from seeing you, Mindblower!
well I tried to get to the website to read more about “tor” but webroot blocked it saying it was a bad place to be. LOL, I don’t need censorship in my life, but it seems even my anti-virus is after me. Maybe it is part of the deep dark web? LOL. Thanks Jim.
Mindblower, Some websites remember you by your IP address, using Tor totally masks that IP address. Google mail for example does not like it when they see a regular US user signing in from the UK or Russia. TOR claims to totally prevent trackers from seeing you and in most cases it does just that by routing you several different relays. if you use the “Disconnect Me” feature and then click o the Onion Logo you will see your Tor circuit for the site. Right now mine shows the Netherlands, Sweden and the UK. Every so often they will automatically refresh to other relays making your location very, very hard to locate. However, anything is capable of being hacked. Actually the more people that use Tor the harder it would be for hackers to every find the original source.
I sometimes access Daves Computer Tips while using a VPN, so my ip is different. Never had a problem posting. But I now see my original post as well. I’m using the preselected features of TOR, and so far no problems for simple browsing. Will see what happens when I try using TOR and a VPN together, Mindblower!
Roo, I am not surprised that Webroot would flag a site like TOR but it is safe. I used Webroot and actually like the program because of its speed and the fact that it has a very small foot print in windows two very desirable features but the program does flag a few times too often on non threatening sites. If you had any concerns, use Sandboxie to download the program and then scan it with Webroot. You will see that once it is downloaded it will not receive a virus or malware flag. Then recover it from sandboxie to your computer or continue to run it in sandboxie. I run Tor in Sandboxie like all my browsers.
Jim
well good news about the tor website – I complained to Webroot about the fact they are blocking this site and here is what I got back –
—————————————————————————-
Hello –
We have reviewed https://www.torproject.org/download/download.html.en and have updated the site to a reputation score of 81. This change is now published in the BrightCloud Service and is available in Database version 4.729.
Thanks again for your suggestion!
– BrightCloud Team
Questions? Suggestions? Need help? Contact us at: dbchange[at]brightcloud[dot]com
—————————————————————————-
LOL, not sure what a level of “81” is, but it is better than whatever “bad” is.
I have a hard enough time figuring out how to sandbox, much less using it. Thanks though for the suggestion.
A support team that actually listens. Goodness, whatever next! 🙂
actually they didn’t 🙁 I sent them an email asking what a lvl 81 was and all I have received back is contradictory to what they sent me. I sent them back all their emails showing what they what they told me and told them to get off their butts and get it changed. I think my choice of words upset their precious little brains for I have not heard back from them. I feel sorry for this younger generation, where everyone is a winner.
But I did download the program and going to try it out. Oh well, onward thru the fog!
Roo, the 81 raking by Webroot is for the Tor site. Primarily because of you bringing it to their attention, they have removed it from a “be aware” site to an “ok no problem site” although different than WOT and in my opinion more accurate thy rate the dangerous sites on the web by reputation not by actual virus infections. Jim was right by noting that they are at least responsive in the fact that they have responded to a comment on a post on ther than on their website. Nice job by you and the Bright Cloud Team
Mindblower commented on Daves Computer Tips:
Thanks for the article Jim. Currently trying it out. So unlike the Ghostery addon, which blocks, am I correct to believe that TOR prevents tracking all together, Mindblower!
Jim did a good job of explaining how TOR works. The Wikipedia article has more. He also warns against trying to use it for illegal purposes. That’s a point worth elaboration. The authorities already have ways of breaching or getting around the TOR web. And they can always resort to the time-tested tactic of turning your internet buddies against you even if you are communicating via TOR. There are people in prison right now because they thought TOR was infallible.
A number of sites have now taken to blocking TOR users altogether. As soon as TOR’s IP addresses are identified, the site delivers a mysterious 303 error message instead of the content.
Hi Jim,
Is it illegal to download Tor on a computer?, when i try to download the program
on my computer i get a message that it is not a trusted site and will not let me open the webpage.
I live in Australia last time i looked not North Korea, can my ISP do this to me?
Hi Ivan, it is totally legal to download, own and use Tor. It is not likely that an ISP would block the download, it is more likely a reputation blocker like WOT (web of trust) or even a part of an antivirus program. The program is just letting you know it is not a trusted site you are visiting. Make sure you are downloading it from the Tor site at: https://www.torproject.org. If it is from that site it is a safe download. If you notice the comment above by roo, he had the same message from webroot his antivirus, he notified them and they declared the site safe.
Jim
I don’t know why people choose Tor (full of craps) instead you should choose the cheapest alternative like Hide My IP, after all Privacy Comes First. I have seen many guys talking about using free VPNs/proxies, but have you ever noticed how these free stuff transfer loads of viruses to your PC/laptop.
Sharon, thanks for your comment. Tor and Hide my IP are similar in many ways but differ in some important ways. First TOR was created by the US Navy and is still used by some military units. It is a good program but not for everyone. It can do some things that a program like Hide my IP cannot.
Having said that, to remain anonymous and safe you are still better off using any VPN than not using one so I am glad to see you use one.
As far a free programs, I would like to say that there are three kinds of “Free”, free with strings, like you mention, Free with ads to pay the cost. and purely free. The last one is rare but happens. The second type is the only one you will see me mention because it is no different than watching TV. Watch for free, watch an ad.
Jim