Security researchers have uncovered a new type of ransomware which is not actually designated as malware but attempts to extort payment from its victims nevertheless. The new strain of ransomware is being labeled “HTML Ransomware” and it works by injecting JavaScript code into the browser. This is a pretty savvy approach on several levels:
- Because of the serious negative effect on browsing, most users are reluctant to completely disable JavaScript
- No need for anything (malware related) to be installed
- Traditional anti-virus programs are ineffective against HTML Ransomware, even with the latest definitions
Furthermore, in order for HTML Ransomware to initiate successfully, there are just two basic requirements; JavaScript must be enabled, and the victim’s web browser has to incorporate the ‘Recover session after a crash’ feature – which is part and parcel of all major browsers, including Internet Explorer, Firefox, Chrome, and Safari.
HTML Ransomware operates on the same principle as the malware variety in that it purports to have emanated from a policing authority, creates a lockout situation, and demands payment to restore normal functionality.
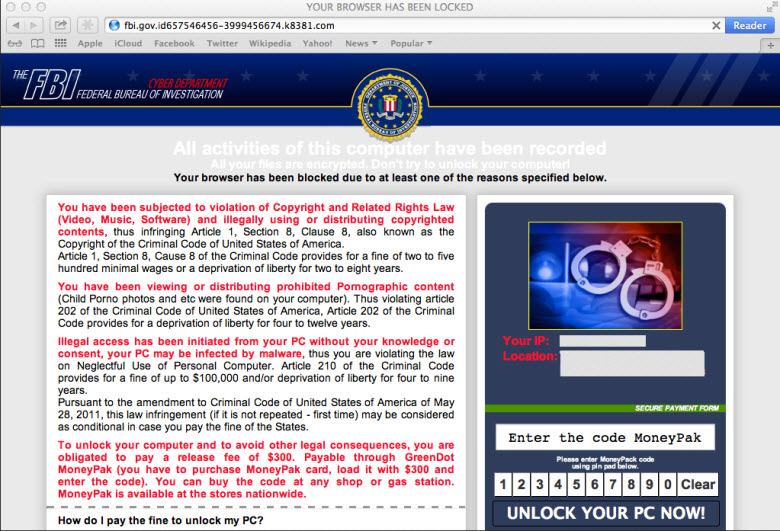
In reality the browser is not permanently locked at all but rather caught up in a loop. The introduced JavaScript creates an iFrame loop which continues taking the user back to the same warning message 150 times over. In theory, if the user were to open and close the browser 150 times, the loop would then be exhausted and the browser should return to normal.
Jerome Segura, Senior Security Researcher at Malwarebytes, has published a blog article detailing this new ransomware, including information on how Mac OS X/Safari users can get rid of it. Mr. Segura’s advice for Windows victims is to; first disable JavaScript and then end all processes associated with the browser.
By all accounts this attack is fairly easy to overcome, the danger lies in users not recognizing it for what it is… a scam. Although a browser may freeze (or lock) for a variety of reasons, typically the scam will include several key components:
- A warning from some authority, such as the Police or FBI
- The browser will of course be locked
- Payment is required via a voucher system
For Firefox users, I imagine that installing the NoScript extension would help prevent this type of JavaScript intrusion.
- You can read through Jerome Segura’s detailed report here: http://blog.malwarebytes.org/intelligence/2013/07/fbi-ransomware-now-targeting-apples-mac-os-x-users/
- Firefox users can check out the NoScript extension here: http://noscript.net/
If you’re using Google’s Chrome browser you can install ScriptSafe to accomplish the same level of security in that browser.
Install it through the Chrome Web Store: https://chrome.google.com/webstore/detail/scriptsafe/oiigbmnaadbkfbmpbfijlflahbdbdgdf/related
Thanks for the additional info Bob, appreciated.
Cheers… Jim
While ransomware injures the innocent and uninformed – and lines the pockets of thieves – occasionally some good can actually come from this. Accidentally, of course.
Here in the U.S., just a couple of weeks ago, a man – who was sick enough to be viewing child porn – fell victim to this scam. But instead of paying the ransom, he went to the local police to find out how much trouble he was in. He was in no trouble (legally) prior to his visit, but he sure is now!
Illness, ignorance and stupidity are a bad combination!
Here’s one article referencing the story:
http://arstechnica.com/tech-policy/2013/07/man-gets-ransomware-porn-pop-up-turns-self-in-on-child-porn-charges/
They walk among us!
Thanks for that Joseph, it’s nice to know that the infamous ‘ransomware’ may at least be doing some good. 🙂
Thanks for another great article Jim. Those of us who are extremely security conscious appreciate being ‘kept up to speed’ with all aspects of computer security. Unfortunately when I send information such as this to family and friends they appear to be ‘too blind to see’, but when their computer goes belly up, who is the first to get the call for help. In the computer world, “She’ll be right mate” never is. :-{
I installed a no script extension in Firefox, and both Youtube and Netflix didn’t work. But with the extension installed, there’s a small icon on the Firefox page and it’s easy to click on that and temporarily enable the script whenever I chose. Thanks for the information!
Hi Susana – Yes, that’s correct. In fact, most sites utilize script in one way or another but, as you say, it’s very simple to temporarily allow script for a particular site in NoScript… just be sure it’s a trusted site.
Appreciate your comment,
Cheers… Jim