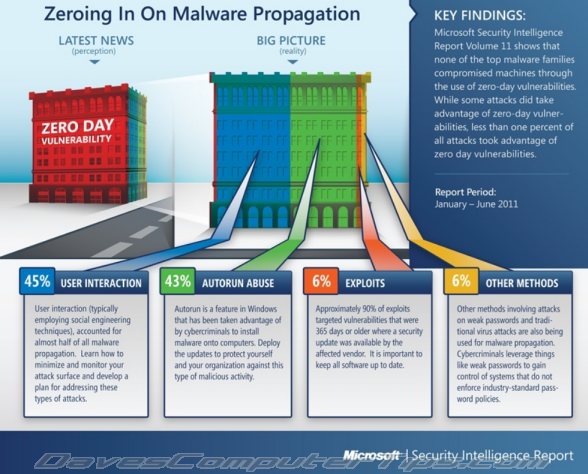
According to the latest Microsoft Security Intelligence Report released very recently, 45% of all malware infections are propagated per medium of social engineering techniques. These are the threats which trick users into running a malicious program and rely heavily on user interaction.
Not far behind is malware inflicted by maliciously taking advantage of the Windows Autorun feature. Autorun abuse weighs in at 43%. Somewhat surprisingly, the report states that a mere 6% of all malware is propagated by exploiting software vulnerabilities. It goes on to say that 90% of exploit attacks targeted vulnerabilities which were at least 365 days old and where a security update was readily available from the affected vendor – with less than 1% of all attacks targeting zero day vulnerabilities.
The remaining 6% is attributed to “other methods”, the most prominent being attacks on weak passwords plus traditional virus attacks. Whether you agree with the report’s findings or take them with a grain of salt, the statistics do tend to confirm the advice most often proffered by security experts – a large proportion of malware attacks can indeed be thwarted by user habits, per medium of a heightened awareness and a little more attention to detail.
Download the full report HERE (924KB PDF)