Email Discipline
Email has become an evil necessity in today’s electronic world. Email is used by just about everyone “as of 2021 4.26 billion people around the world use email” (Source: 99 Firms Blog) with a mobile device or computer.
Understanding that “Spam comprises 85% of all email” (Source: Dataprot.net) should give you a clear picture of how today, email is used to try to sell us everything from Appliances to Ziplock bags.
With Self-Discipline, most anything is possible – Theodore Roosevelt
SPAM VS Infected Email
Not all SPAM is malicious. In fact, most SPAM is a nuisance more than a threat. But up your mobile device and unfortunately up to 73% of it carries the ability to steal your identity and 2.5% are scan and fraud attempts. These are big numbers but the profits for scammers that steal your identity are just too tempting. 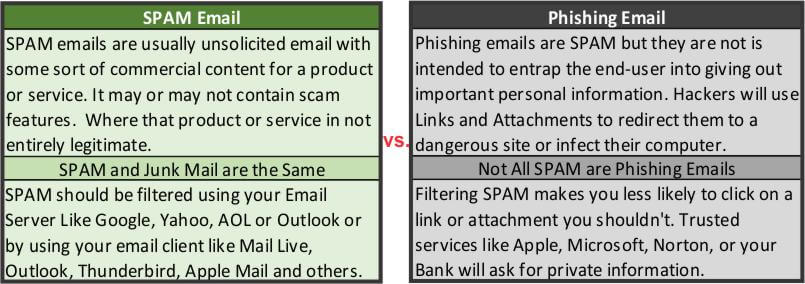
Can We Stop SPAM?
Probably not! You don’t become one of 3 trillion-dollar companies without having some smarts, but Bill Gates really dropped the ball when in 2004 he said, “Within two years from now SPAM will be solved”. While stopping SPAM might not be possible, we should be more concerned about stopping SPAM that contains malware. Both (malwarefox.com) and (cybersecurity-insiders.com) claim that phishing emails are the number one method of hackers and state-sponsored hacking organizations to spread malware and ransomware. If we can’t stop it, what can we do? Practice good email discipline.
Email Discipline
One of my first articles for DCT was Learning Computers: Phishing back in 2015. In rereading it, I realized that not much has changed. We still have SPAM fighting programs in Outlook, Yahoo, and Gmail but they can only classify emails as SPAM once they are known to the community or once you have notified your email client to stop receiving them. In most cases, you will still receive them but they will simply populate a junk or SPAM folder instead of your inbox.
Today, computers are not infected simply by opening an email. You would have to take the next step to be infected. Those steps include:
- Links: Clicking on any links that look like “Beware of Scam or Phishing emails!” This link is a valid link to an article by Jim Hiller that you should read. But in an email, a link might direct you to a phishing site and by clicking on it you have just become infected. Before clicking on any underlined link or even an image, you should right-click on the link with your mouse and a pop-up will tell you exactly where that link will take you. Try it on the link above. Just because it says Google Play or Apple App Store there is no guarantee you are not going to be redirected to another site a hacker wants you to visit

- Attachments: Not only does everyone love to share! A lot of us like to spend the day checking out emails from friends and relatives sharing photos of the grandkids, a funny joke, or a quick video. As harmless as that might sound these are good reasons to be suspicious. Attachments are one of the most common methods of infections
- Use Two Step Verification: (TSV) also known as “Two Factor Authentication” (2FA) and truth be told it is somewhat of a pain in the butt but worth the added security. We have several good articles to help with that. “How To: Enable The Microsoft TSV” by Alan Wade, How to Set up Instagram 2FA “Google To Enforce TSV” and “What is 2FA & Why You Need It“, both by Jim Hiller.
This is where good discipline comes in. NEVER open attachments or follow links from an email you did not expect to see. That should be your first rule. Even email from your most trusted friends and relatives can be infected and you should ensure that they sent it. *
Precautions If You Are Email Hacked
If you ever have the misfortune of being hacked by email, you should visit every site that has your sign-in and password. You may keep your sign-in, but you must change your password. Not only might it be used on other sites by you, but hackers can use it to guess what other passwords you might use. If your dog’s name is Susie and your password to site one is Susie101&, it is not hard to guess that another site might use Susie 456*.
Microsoft Recommends:
- That you delete all your sent messages
- Change your security questions
- Warn Your Friends
- Look for any account settings that might have been changed
- Report any identity theft to the Federal Trade Commission Identity Theft site
Summary
On my daily computer repair trips, the only infected users I meet are infected by email and phishing websites. They believe that just because the joke they clicked on came from Uncle Joe it was safe but that might not be the case.
*If your Uncle Joe has already been infected, hackers can use the Contacts feature in his email and send infected email to everyone on that list and each one will receive his correct email address. Staying safe while using email is not hard, but it does take a little discipline to ensure you and your loved ones are always protected.
—


Hi Jim,
A few more Bill Gates quotes/predictions:
“640 K [of computer memory] ought to be enough for anybody” 1981
“There are no significant bugs in our released software that any significant number of users want fixed,” 1995
“I see little commercial potential for the internet for the next 10 years,” 1994
Thanks for the link, John. But even Einstein said, “failure is success in progress”. Without Apple’s G4 block computer, we might never have had the beautiful Apple Airpad.
You said “you should right-click on the link with your mouse and a pop-up will tell you exactly where that link will take you”, but that doesn’t work for me. I can check by pointing at the link with my mouse, but right-click only gives me a menu with options to Open in a new tab or window, or to copy the link.
Tony, thaks for catching that error. it should have said when you hover your mouse pointer over the link not right-click