Internet Safety Continued
 This is Part 2 of Using Browser Extensions – Internet Safety. We will be covering the two types of programs that probably have the ability to keep you safer than all the others combined: Password Generators/Managers, Virtual Private Networks (VPNs) and Proxies. Using these extensions can be one of your safest acts as a PC user.
This is Part 2 of Using Browser Extensions – Internet Safety. We will be covering the two types of programs that probably have the ability to keep you safer than all the others combined: Password Generators/Managers, Virtual Private Networks (VPNs) and Proxies. Using these extensions can be one of your safest acts as a PC user.
The rating conventions are explained in Part 1. If you would like to start at the beginning, please read Using Browser Extensions – Internet Safety.
As mentioned in Part 1 , I used Sandboxie to ensure that (Possibly Unwanted Programs) PUPs, Malware or Viruses are not loaded on my machine. One of the intentions of these articles is to show you the power, safety and fun available with extensions and in doing so, some of you might experiment with extensions not shown here. At least, I hope you would. I do recommend that you use a program similar to Sandboxie. It has its own free version and there are several free alternatives. In addition, I would encourage you to make sure you have an Antivirus or Anti-malware program running as well. I cannot vouch for the vetting process Chrome and Firefox use in allowing developers to put extensions on their site, let alone the one-up extensions you might find on the web. Bottom line, think safety first and be careful at all times.
Password Generators/Managers
To understand why you probably need a Password Manager, check out this Dave’s Computer Tips article, 25 Worst Passwords of 2014.
This particular group of Password managers load into your browser, unlike their counterparts that load as a program on your PC. They are, for the most part, a little lighter in functions and memory, but they still perform quite well in both generating random passwords and managing them for you.
They are a lifesaver for individuals that have several passwords for websites, applications, etc. Password managers do all that for you. Some do it across platforms so once you have your passwords safely ensconced in the manager, they are available to you on your other devices. Some charge a fee to go mobile but if you use your phone or tablet on the same sites, it is something I would recommend.
As mentioned, they generate passwords that you don’t have to remember. That is their biggest but not only strength. Password managers often let you include personal and financial information that is secure behind an encrypted password.
LastPass – (5 Star) (Free+) (Browser: CF) (Conflicts: None)
Note: The rating methods are discussed in Part 1 of this article.
 LastPass has been around for quite a while and the free version will allow you to save all the passwords you need. The extension will also let you enter your personal information so when you visit a shopping site or your online bank, everything is ready to be input into the online forms. This is a big time-saver, particularly if you do online shopping.
LastPass has been around for quite a while and the free version will allow you to save all the passwords you need. The extension will also let you enter your personal information so when you visit a shopping site or your online bank, everything is ready to be input into the online forms. This is a big time-saver, particularly if you do online shopping.
LastPass is one of the most used Password Managers in large part because their paid version for the PC is one of the least expensive around– $12.00 compared to some costing $40 a year. It is rich in features and exceptionally easy to use. If you sign into a LastPass account, your passwords follow you from one browser to the next.
The image below is how the LastPass Vault appears. It contains all your links and associated passwords in this vault. You may launch a site directly from the vault by clicking on the link.
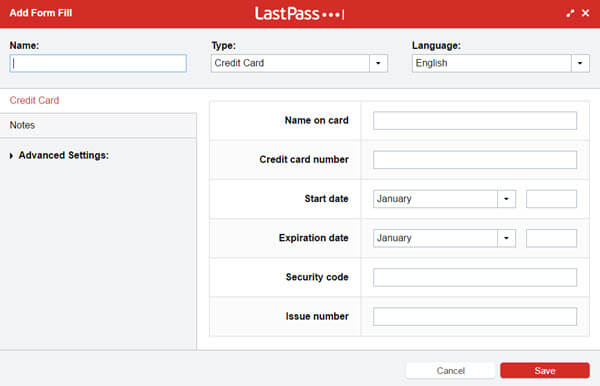
Last Pass has one of the most extensive list of options available for a free extension. Just click on the Icon in the upper right hand corner of your browser and have instant access to these options:
- Vaults: used for storing all your personal information and information unavailable with out the master password
- Sites: A list of your password protected sites
- A Form Fill: Use this to enter your information
- Password Generator: Create your own strong, unique passwords
There is even a tab for saving all your secure notes. Once it is dropped in the vault, it is only accessible to someone with the correct password. Keep your written thoughts private, create notes on credit cards, banking account numbers, etc.
Pros: Very easy to learn and use. With every new site you log onto, LastPass will remind you to save the password and username.
Cons: None
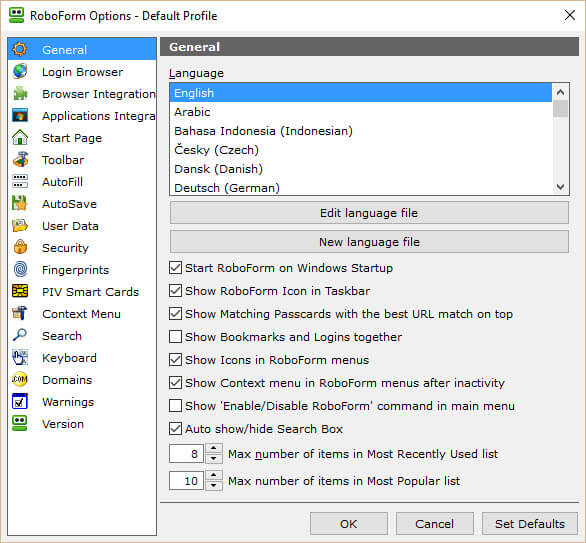
RoboForm – (5 Star) (Free+) (Browser: CF) (Conflicts: None)
 Roboform is another very popular password manager. Installing RoboForm will add a small toolbar to the bottom of you your browser giving you quick access to manage the application.
Roboform is another very popular password manager. Installing RoboForm will add a small toolbar to the bottom of you your browser giving you quick access to manage the application.
I really like the easy way to instantly log in to every account you have. RoboForm provides two simple  ways of doing this:
ways of doing this:
- Simply type the site in the RoboForm “search window” and it will automatically navigate to the site, fill in your username and passwords and open the site.
- You may also use the Logins tab on the toolbar where the logins are divided in Recently Used, Most Popular and Logins. The sample list showing the logins I created for this review clearly shows how easy it is to use RoboForm. Just click on it enlarge the image.
RoboForm also has an impressive array of options that should fill just about every need you might have for password management. Like other Password managers, it can generate complex passwords for you, auto fill documents and even create Passcard Logins. Use PassCards to store your form data that is specific to a website. They may include Username, passwords, and even Win32 apps like Skype.
RoboForm allows for the use of Windows Bio-metric Framework (WBF) and UPEK fingerprint readers.
Pros: In all, RoboForm is one of the most impressive Password Managers you will find.
Cons: RoboForm is very pervasive and when trying to ensure it is linked to your other devices places itself in several areas of your browser and computer folder and Registry. If you are protective of where programs place themselves you might want to consider another Password Manger.
Dashlane – (5- Star) (Free+) (Browser: CF) (Conflicts: None)
 Dashlane is the Password Manager I happen to use. It is, in my opinion, equal to the two Password Managers reviewed above. It covers all the same features like Password Generators, Secure Notes, Personal Information Form Fills, etc.
Dashlane is the Password Manager I happen to use. It is, in my opinion, equal to the two Password Managers reviewed above. It covers all the same features like Password Generators, Secure Notes, Personal Information Form Fills, etc.
Dashlane’s start page is broken down into three simple sections: Manager, Wallet and Contacts. Using any of the features is easy enough but I like three of the Dashlane offers:
 The First Feature
The First Feature
The Emergency Password Share – With this feature you can share your passwords with anyone you wish on an emergency basis. It will notify the individual by email that you have given![]() them emergency access to your passwords and once they click on the link, (when needed) they will have access based on a waiting period you may set. This makes it different than just sharing your passwords because you have full control of when it is available to them.
them emergency access to your passwords and once they click on the link, (when needed) they will have access based on a waiting period you may set. This makes it different than just sharing your passwords because you have full control of when it is available to them.
The Second Feature
The ability to store receipts of online purchases. Like the other Password Managers, you may store you credit cards, drivers license and personal information. 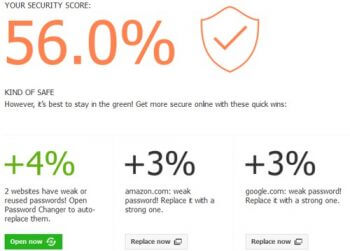 However, if you use this information in Dashlane to complete a purchase online, the receipt will be saved in a separate section. Nice and neat, all in one place.
However, if you use this information in Dashlane to complete a purchase online, the receipt will be saved in a separate section. Nice and neat, all in one place.
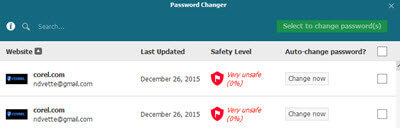
Dashlane also has a Security feature that will give you a page view of how safe your passwords are by giving you a security score. It will include the number times you use the same password, the websites that have weak passwords. All of which leads me to…
The Third Feature
The ability to change weak passwords easily by using the Change Password feature.  Because Dashlane indicates the passwords that are weak, simply click on “Change Now” and you will have a strong password applied and then saved in Dashlane.
Because Dashlane indicates the passwords that are weak, simply click on “Change Now” and you will have a strong password applied and then saved in Dashlane.
Pros: The three features mentioned in this review, and ease of use.
Cons: The free version does not allow synced mobile passwords.
Chrome and Firefox
This post is about extensions but I feel it is important to mention that both Chrome and Firefox have their own built in Password Managers. They will both let you synchronize with other devices, with Chrome syncing to Android devices and Firefox syncing with other Firefox devices. If you are going to use either of these Password Managers, you should make sure to have a master password to sign into your browser, or anyone using your computer will have access to your information.
VPNs and Proxies
The final Internet Security extensions are designed to make you invisible on the internet. Both VPN and Proxies mask your identity and Geo-location (where your device resides). The major difference between VPNs and Proxies is that VPNs use encryption to transfer data. The difference in the features on the both the VPNs and the Proxy programs are not always obvious. Some, like TunnelBear, do not give any options, while others give quite a few options.
Testing
I used my own purchased copy of PureVPN as a base for comparisons. When testing the speed of the browser with and without the VPN or Proxy, I used a random download from Europe. As you would imagine, if you live in the USA, hosts from Uzbekistan and France took longer than hosts from Chicago and Los Angeles.
Some VPN and Proxies use different types of servers: Standard, Premium and Public. Certainly, you should expect to see premium servers on paid VPNs, but some free extensions will only have Standard and Public. I would not recommend public servers because the performance is very slow. As an example, without VPNs or Proxies, the average time to open the sports page from France was less than three seconds. With a host in the US using PureVPN, it stayed around three seconds. However, if I set the host to Australia, the time jumped to closer to seven seconds. The extensions’ reviews fared favorably with these times, with most being a second or so longer.
TunnelBear VPN – (4 Star) (Free+) (Browser: C) (Conflicts: None)
 When it comes to pure simplicity, TunnelBear is hard to beat. Once installed, it will take control of your browser’s proxy settings in Chrome.
When it comes to pure simplicity, TunnelBear is hard to beat. Once installed, it will take control of your browser’s proxy settings in Chrome.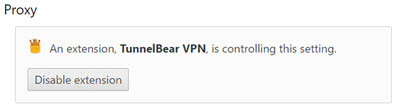 Clicking on the TunnelBear icon in the upper-right corner of your browser will allow you turn the VPN on or off.
Clicking on the TunnelBear icon in the upper-right corner of your browser will allow you turn the VPN on or off.
From this drop-down (see image to the right) you may also select the Proxy. Any end user will only see the proxy you select. You can check by typing in  the address bar “My IP”. This service will use your IP to show you where you are located. Prior to starting any VPN you should see your actual location. Afterwards, you will see a completely different IP address.
the address bar “My IP”. This service will use your IP to show you where you are located. Prior to starting any VPN you should see your actual location. Afterwards, you will see a completely different IP address.
Once you create an account, you are all set and you just have to surf– TunnelBear takes care of the rest. In a lot of situations this is the perfect solution for people afraid of using a VPN and only use the Internet on a limited basis.
Pros: Very easy to use.
Cons: Unfortunately, they do not yet have a version for Firefox, and the free version is limited to 500MB of data a month. Also, the only way TunnelBear can put a 500MB cap on your usage is if it is monitoring your usage, something most VPNs do not do.
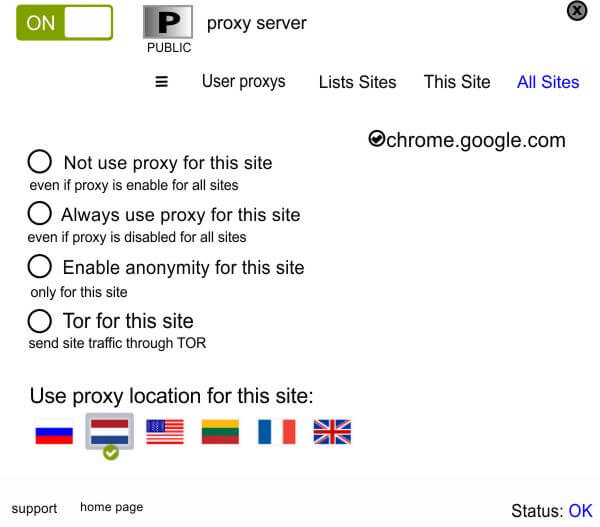
Proxy for Chrome – (4 Star) (Free+) (Browser: C) (Conflicts: None)
 Proxy for Chrome has a few more options than TunnelBear. Open the Chrome-like logo in the upper right of the browser and it will bring a drop down menu (see below). From the drop down window you may turn on the Proxy server for Chrome. You may also select any of the following options:
Proxy for Chrome has a few more options than TunnelBear. Open the Chrome-like logo in the upper right of the browser and it will bring a drop down menu (see below). From the drop down window you may turn on the Proxy server for Chrome. You may also select any of the following options:
- Do not use a proxy for this site even if proxy is enabled for all sites – This feature will let you use a proxy for all sites except those you exclude. Because it is natural for any VPN or Proxy to slow down transfer speeds in some cases, you may elect to have it turned off when visiting pages you trust.
- Always use proxy for this site even if proxy is disabled for all sites – If you have only one or two sites that might require extra anonymity, this setting would work best.
- Enable anonymity for this site and only for this site – This feature will mask your identity but often has a downside. Some sites will block access if it is able to see an IP.
- Tor for this site – Send site traffic through TOR. TOR (The Onion Router) option will allow Google Proxy to run through TOR. Some websites created with TOR will only work with the TOR browser. This option in the program will mimic the TOR browser.
It is important to note that unless you select “All Sites”, you will be forced to use a Public Proxy Server. Like TunnelBear, you may select the list of countries that will host your proxy. This list is smaller than most VPNs but should be enough for most individuals.
Pros: Made for Chrome so I would expect fewer problems, and none of these showed any problems.
Cons: Smaller Proxy list and Public Proxy Servers must be used unless “All Sites” is selected.
Hoxx VPN – (3 Star) (Free+) (Browser: CF) (Conflicts: None)
![]() Hoxx managed a very slow 1.1Mbps on the Russian servers which was about twice as slow as the other extensions.
Hoxx managed a very slow 1.1Mbps on the Russian servers which was about twice as slow as the other extensions.
Pros: Simple installation.
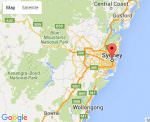
Cons: No USA proxies listed. Not a major problem but will slow your surfing. Using any of the VPN Proxy extensions will place you on a map indicating where anyone looking at your IP would assume you are located. In the map at right, I am actually in Nevada, but by typing My IP in the address bar of my browser this is what would come up. If I set my proxy to Sidney Australia.
Hide My IP VPN – (3 Star) (Free+) (Browser: CF) (Conflicts: None)
Hide M y IP has an impressive list of servers with many that will fit anyone’s needs. However, after the 3 day free trial, you will be switched to public servers. Three days is hardly enough time for a trial and I feel this is more of lead-on to purchase the VPN than a free copy. You may, however, choose not to upgrade. They have some servers available for free users, but far fewer than the paid version.
y IP has an impressive list of servers with many that will fit anyone’s needs. However, after the 3 day free trial, you will be switched to public servers. Three days is hardly enough time for a trial and I feel this is more of lead-on to purchase the VPN than a free copy. You may, however, choose not to upgrade. They have some servers available for free users, but far fewer than the paid version.
Pros: Hide my IP does the job.
Cons: It is a shame to lose the large list of servers unless you pay.
ZenMate – (3 Star) (Free+) (Browser: CF) (Conflicts: None)
 You have probably surmised by now that most of these extensions are pretty much the same. It is pretty hard to make the call on which is better or worse. Frankly, I would not get hung up on that. For casual surfing while remaining a anonymous, these programs will do that. ZenMate’s drop-down window clearly shows that you are protected and also indicates that your connection is from Germany, or wherever you set the host.
You have probably surmised by now that most of these extensions are pretty much the same. It is pretty hard to make the call on which is better or worse. Frankly, I would not get hung up on that. For casual surfing while remaining a anonymous, these programs will do that. ZenMate’s drop-down window clearly shows that you are protected and also indicates that your connection is from Germany, or wherever you set the host.
Pros: Clear knowledge that you are protected and fairly quick transmission speeds.
Cons: No choices other than VPN On or OFF.
Summary
There is no doubt that I could have listed about four more Password Managers and about 12 more VPN & Proxy extensions. There are certainly a lot of them out there but I think you get the point. Try one or more of these Internet Security extensions and start feeling a little safer while you surf the internet. I will try to lighten up the topic matter in the next post and show that extensions can be fun and helpful. If I left out a version that you believe to be particularly useful, let me know in the comments and I will give it a try.
Jim
- Using Browser Extensions – Internet Safety – Part 1
- Using Browser Extensions – Internet Safety – Part 2 ← You are here
- Using Browser Extensions – Utilities
—




Going through the ISP is still going to be monitored by the the ISP, you can connect to any VPN but not truly be anonymous.
Extensions have always been security risks, so we take risks using them in the first place. Actually, connected to the net and we are automatically at risk.
Antivirus aren’t as great as they appear, there tons of viruses that are in the wild and still undetectable.
My argument is that users can be too paranoid and they should just disconnect from the net and wear a tinfoil hat; then again, they could always be lenient.
Thought on add-ons that are useful:
Since I make my browser clean everything, I use LastPass for auto-filling. Plus, I’m happy that it’s on Windows Phone and while I use other browsers on other computers.
megaman, I don’t mean to negative but I believe you are not necessarily correct in your first three statements. If you are using a VPN and you have DNS Leak Protection ON, your ISP cannot see into the encrypted tunnel and therefore have no idea of your traffic and content – provided that you are using a VPN with sufficient encryption. While they may know that someone is using VPN, that is pretty much the extent of their knowledge, So do they know you connected to their ISP using a VPN, the answer – in most cases – is yes. Is where you go and what you do anonymous? YES. Therefore, VPNs equal anonymity.
Yes, extensions can and have been security risks but extensions of Google, Firefox and especially the new versions added to Edge are thoroughly vetted for risks. Search the internet and add an extension not much vetting going on.
I think we can agree that there is no 100% virus protection program but antivirus software that keeps 95% of the malicious infections away from your machine is by nature better than 0%. That’s a fact.
Using Lastpass for form-fills “Brilliant”
Jim
Thanks for the articles. Several months ago I followed languy 99, usually a good source, and he advised that I use Comodo VPN. This latter is a total pain, and I want to remove it totally. Problem is, it sets in like a Siberian Winter, it does not remove. Please tell me how to remove Comodo VPN totally, unconditionally. Thanks!
By the way, several of those also work on IE and also on Android.
Sergieye, All aspects of Comodo can and usually are a very nasty clinging piece of software. There are so many remnants that it is almost impossible to remove it with Window Uninstall. Please download Geek Uninstaller from Geekuninstaller.com. You may also try Wise- Uninstaller from http://www.wisecleaner.com/wise-program-uninstaller.html. I would not recommend downloading these from any other site because they may include additional programs you won’t need. With Geek Uninstaller, Install and Run the program then highlight the offending program, There may be more than one Comodo and if there is you will have to do each. When it is highlighted, click on Actin and then perform a “Force Removal” wait for the uninstaller to do its thing. When it is finished, click on scan and it will search your computer any remnants; select All then delete, there may be another scan screen that appears, select all then delete. If there are other Comodo programs do the exact same thing. This should remove every trace from the registry, and computer. Wise Uninstaller will work in a similar way. Good Luck, Hope this helps.
Jim
Charley, you are correct. I mention that in the beginning of the article but Microsoft will be stopping support for IE. There are several other browsers some of them will work on.
Jim