First, some housekeeping is in order.
The previously published feature of this series, “Rogues, Part 1”, appeared on May 6th. That’s well over a month ago. Normally, most authors like to follow up with the next part of the series published within a week, or less, of the one prior. That way, the topic pretty much stays current.
On this one, this resurrection of the “Rogue” series has left readers in a lurch.
So I need to apologize here for the lapse. Unfortunately, I had a medical situation that disabled my ability to pound on the keys for a while.
However, I DID have a Part 2 in my pocket, ready to go. But compounding my medical situation was a peculiar error in publishing Part 1 (NOT WordPress or DCT’s fault . . . likely my own error or one of those mysteries of the ether) that made it necessary for me to trim Part 1 and thus leave out a lot of clarifications, and in turn has made it necessary for me to do a complete re-write of Part 2 and even make this a three parter (I had originally planned a 2 parter only)
So here in Part 2 I’m going to reiterate some things I said in Part 1 (no, I’m not going to repeat the whole thing, but you might want to open a separate instance/tab of Part 1 in your browser and have it ready for reference), and clarify and expand on some of those things too. Plus, I’m going to use the same convention I used in Part 1 and bombard you with screen shots of these ridiculous warnings, and by the time you read through this, you’ll be more than familiar with this scare tactic. (These screen shots are of older versions ON PURPOSE . . . outdated versions disguise the title more . . . see “Legal Threats” in Part 1.)
____________________
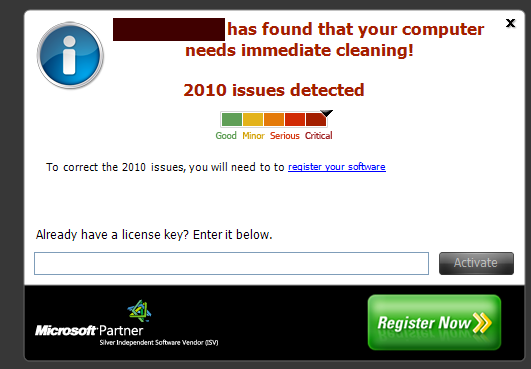
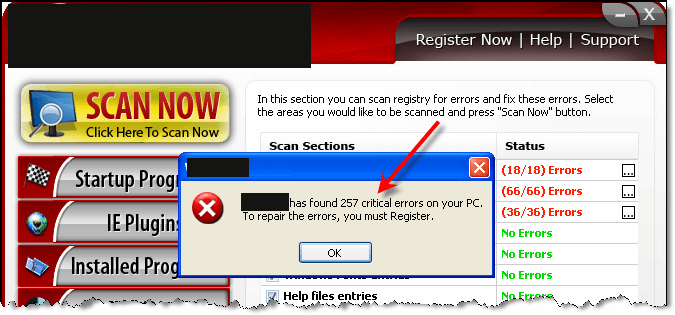
Now on this one we have 590 errors. To reiterate, that will scare the bejesus out of a novice and likely motivate him/her to get out their wallet.
____________________
OK, housekeeping out of the way now, let’s get down to the substance of this article.
EXPANSIONS AND CLARIFICATIONS ON PART 1
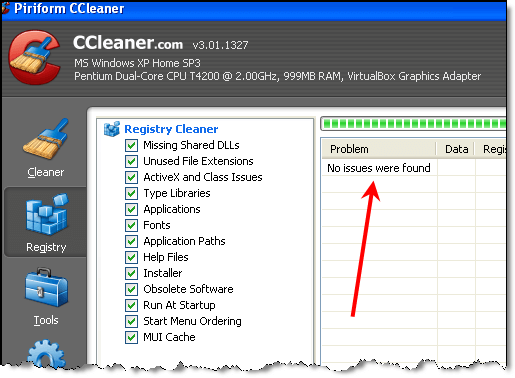
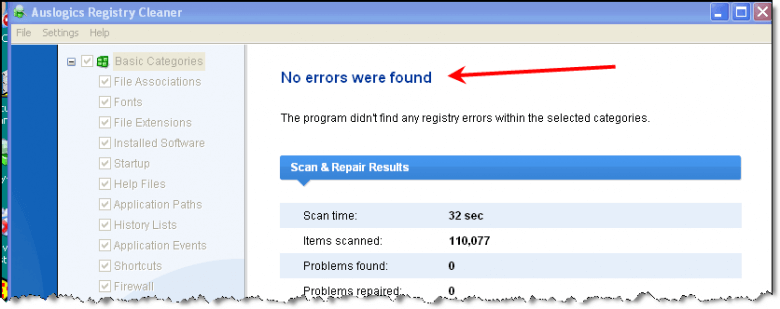
When I did these scans on my test machine, over a year ago now, I had previous to running each one, run CCleaner and Auslogics scans (two reputable FREE pieces) and used them to bring my registry errors to ZERO before I ran the culprits:
Now before you geeks jump all over me on this, let me qualify a few things.
First of all, my manipulations were by no means a “laboratory test”. But “ZERO” errors (CCleaner and Auslogics) compared to 100’s of errors is pretty dramatic and may prompt one to scrutinize those 100’s of errors (which I will do in Part 3.)
Secondly, and perhaps most importantly, I will gladly admit that CCleaner and Auslogics is nowhere near as aggressive as some of the other registry cleaners out there, consequently it is only natural that the more aggressive would find more errors. But, as you’ll see, these “errors” are really trivial and certainly NOT “critical”.
____________________
Here we have “critical” again.
____________________
Now someone pointed out to me that these things are not really rogues but rather scareware.
Here is what I said in Part 1:
It would be nice if everything in this world were black and white and there were no blurred lines. The truth, in many cases, lies somewhere between the two extremes.
The term “rogue” is a good example.
Relative to the term “rogue” . . . there is a technical definition and a “common usage” definition. Very often the two are different. What is meaningful is what YOU take as the definition, which is often the “common usage” type.
While sticklers/computer nerds may insist that the technical definition is the “right” one, “rogue” in common usage is generally taken to be ANY piece of software that renders a detection result (most often on a scan of the windows registry, but things like “optimizers” supposedly scan other areas, like start up programs) that scares the bejesus out of novices with numbers like the message above displays and then offers to remove the nasties IF YOU PAY.
The terms “scareware”, “hostageware”, and “crapware” (there are a few others that I probably missed) are perhaps more descriptive, but the novice’s common usage term for all of these is “rogue”.
When you say “rogue”, that is what most people think of, with the exception of geeks that adhere to technical definitions, and who sometimes are quick to point out that you are “wrong” to think otherwise. Of course, they are correct insofar as technical definitions are concerned, but in the case of “rogue”, that technical definition does not portray what the common usage is.
Here’s the “geek/technical definition” of rogue and this may clarify things here:
Most geeks maintain that a piece of software is a “rogue” if it deposits a trojan on your machine, and “phones home” when you “register” with them to “fix” the errors (there is usually this huge “FIX” button somewhere along the line that leads to the scammer’s web page), and anything that does not infect your machine like that is NOT a “rogue”. That, however, is not what comes to John Q. Public’s mind when you say “rogue”. Mr. Public does not always run to Wikipedia (not always an accurate source anyway) when he hears a term that he recognizes as “common”. He relies on plain English, not geekspeak.
By not adhering to the technical definition, I don’t mean to perpetuate any “inaccurate” definitions or otherwise sponsor a misunderstanding, but when the novice searches on “rogue” I think the substance here would be helpful. Again, “scareware” is perhaps more accurate, but a lot of novices recognize these things as “rogues”.
These articles are directed more to novices, i.e. those people who speak plain English, rather than to geeks.
(Interestingly, I have a geek friend who always writes it “rouge” . . . which is the term for the makeup that a gal puts on her cheeks to make them look red. The guy is really brilliant in most areas, certainly computers and computer security, but I guess like Einstein he can’t even tie his shoelaces or work a yo-yo. Apparently, getting the difference between “rouge” and “rogue” is not in his skill-set.)
____________________
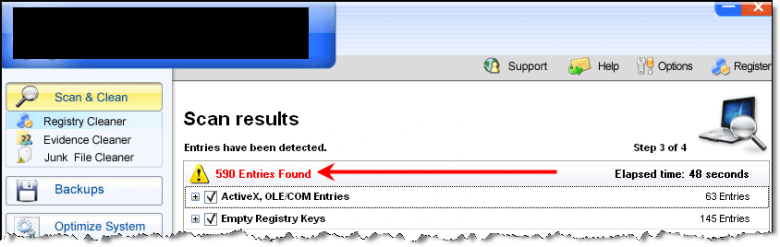
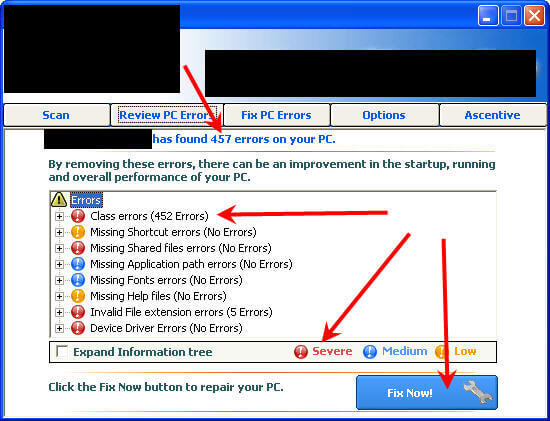
Here we have a total of 457 errors, ALL of them “Severe”. And that ever present “Fix” button, which takes you to the companies web page where you can register AND pay to have these “Severe” errors removed.
____________________
A clarification to the “Legal Threats” section in Part 1:
You will see throughout here that I have redacted (blacked out) ANY information that either NAMES a specific title or can even lead to finding out what that title is.
That’s because there is some legal risk associated with naming a title and calling it a “rogue” . . . both to the author and the blog host. Some dubious companies that produce these “rogues”, as I’m defining here, will hang their hat on the “technical” definition (above) and sue based on them NOT filling those criteria (as I was threatened.)
Which leads me to a caution about whatever responses YOU may make in the comments to this series here and is one of the real reasons I bring this up at all.
Now I’m not an attorney So I’m not about to render any legal advice here.
(Watching two non-attorney individuals argue legal issues, on a forum or blog or whatever, is like watching two roosters in a barnyard seeing who can crow the loudest. It’s laughable and often degenerates into a flame war and an uncivil exchange based on amateur speculation ONLY.)
But I AM going to offer some common sense advice. If you want to make a comment here, fine. But if you accuse a piece of software of being a “rogue”, please refrain from mentioning specific titles. While I probably would be inclined to agree with you, these scumware clowns frequently respond with threats of a law suit (see “Legal Threats” in Part 1), and as frivolous and capricious as YOU may think that threat is, juries are notoriously fickle and judges are all too human.
____________________
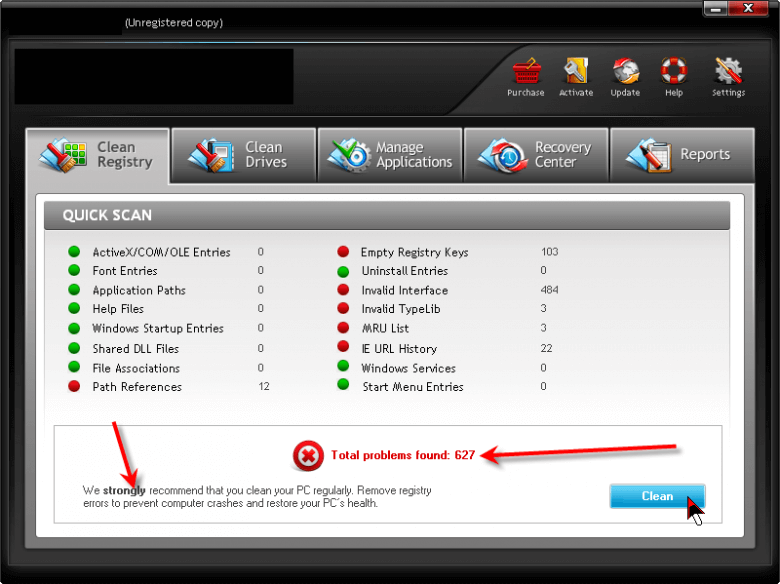
Here we have 627 errors. And notice in the upper left corner it indicates this is an “unregistered” copy. I point that out because these peddlers will often argue that if it was a “registered” copy, the results would be different (and presumably more realistic.) Of course, you have to PAY to get a registered copy.
Now I’m dedicated, but I draw the line at PAYING to test this nonsense.
____________________
REITERATION FROM PART 1:
I want to point out here that DCT is NOT hiding anything. Blocked out/blacked out areas cosmetically make it look like the document is the result of a Freedom of Information Act query or it is otherwise a cloak and dagger effort to hide information. Clearly it’s not the case here that DCT is hiding pertinent information and acting fraudulently, and I don’t want anybody to get that impression.
My redactions are to protect DCT from any potential legal action . . . which is a very REAL possibility as you saw in the screenshot of the threatening letter I got (Part 1).
By the way, if you use a link checker like McAfee’s SiteAdvisor(SA), most of these things will show GREEN. That’s because SA’s parameter ONLY is the presence or absence of malicious code. In a link checker that is based on user TRUST, like WOT, you may see these things downrated. So is SA or WOT wrong when their ratings for these things show differently? NO! They both are correct within the parameters they use: SA for the presence or absence of malware, WOT for user trust.
Now this may seem like a bit of a digression and off topic, but I think it needs to be pointed out because some users may see these things have the green light from a link checker and think they’re “safe”. Au contraire, mon ami!
And one more thing on link checkers that’s pertinent here. They are ONLY guidelines and should be used as such. Link checkers are not infallible nor are they substitutes for common sense.
One of the popular link safety/trust checkers was sued recently in a court in Florida. (When your business is to call someone’s baby ugly, you can expect that, and that does indeed happen frequently and in fact these popular safety/trust link checkers have attorneys retained just for that reason.)
(This is pertinent to this discussion because I want to show that legal repercussions ARE possible if you name a title and call it “rogue”.)
Well, that suit was pretty ho-hum, was brought by a convicted felon who had never won (in fact, most previous suits of his had been thrown out of court even before going to trial), the claims made by the raters for that link safety/trust checker were supported by plenty of solid fact, and the defendant was based in a foreign country (so there were questions about whether or not a Florida court EVEN had jurisdiction). Consequently the case was an excellent candidate for one of those “frivolous and capricious” suits that gets thrown out right out of the gate.
The betting money on this thing was that it was a dog that just flat out wouldn’t hunt, that it wouldn’t even grow legs and go anywhere.
But, and this is the part about juries being fickle and judges being all too human, it DID get to court. It was eventually defeated, but the foreign guys had to fly their expensive attorneys over to the USA and respond in Florida.
In Part 3, which I WILL publish in a few days, we will wrap up the discussion by showing common ways these things are distributed, examining some particular tactics, and giving advice on what to do if you find yourself dealing with this nonsense.
Oh . . . one more thing before I close. This is NOT a discussion of the virtues or lack thereof of registry cleaners. It just so happens that the registry cleaner category is most easily leveraged by these “rogue” peddlers.
The Windows registry has been portrayed as a black box, mysterious and troublesome (Dave has authored a good article explaining the registry . . . it’s here), and that IS the way most novices think of it (which is probably just as well anyway.) But that is a perfect characterization for scareware marketers to leverage.
What better way to scare money out of your wallet than giving you the notion (with the huge “critical error” numbers) that something you don’t even understand is misbehaving and these automated scanners can “fix” the problem . . . for a price of course.
This is a great article Bob, and what you say is happening in every home of novice computer users. They hear, see and read, on a daily basis, about computer hackers who obtained…. X, money, Y, personal & credit card details. They are ‘experts’, because a friend told them that viruses are deadly little creatures who will destroy their computers, and they surf the Internet looking for a cyber-wizard to keep their computers ‘safe. They have been indoctrinated with a ‘Fear Factor’ and believe everything that the ‘super-dooper, whizz-bang, you-beaut, best protection programme in the world’ tells them, and spend money because it makes them feel safe on the Internet.
Several years ago I assisted many seniors in simple computer use, and I issued severe warnings relating to the above. Alas, they didn’t take heed and became ‘experts’ overnight, which resulted in their computers turning into a cyber mine-field.
We can only keep up the pressure to rid the cyber-world of the Bad Guys.
Regards,
Jon in Oz (Jonno)
I thank you for this information, But – What is that irritating floating “SHARE” thing that stays at the top of the page and blocks that part of the page? How can we get it off the page? It certainly discourages me from reading information from you.
Susana,
That is the least intrusive option we have at the moment. Our previous method was causing javascript problems that prevented users from logging into our forum. Sorry for the inconvenience.
So Dave, can we expect to have this bouncing SHARE icon removed a.s.a.p, as it really is a big bother. BTW, why was in installed, Mindblower!
It is much less obtrusive than any other solution I have found to date. The other solutions all appear in an “open” state that covers much more vertical real-estate.
Because we must have a social sharing method and, as previously stated, the one we were using developed some very bad problems due to poor coding. The present “Share” button is the least obtrusive replacement I’ve been able to find. When the problem was first discovered I tried many alternatives and this is the least intrusive, especially for those with higher screen resolutions.
@ Jon in Oz,
Thanks very much for the kind words.
Now when I read through your comment, for a lot of it I thought, “Geeezzz, this guy already knows what I’m going to put in Part 3.” (Which I just now put up.) You weren’t that fly on the wall, were you? (~grin~)
Seriously, a lot of your comments are things that I dealt with in Part 3.
On your remarks about getting rid of the Bad Guys . . . well, I have a coupla’ things.
While I applaud the efforts by LE (Law Enforcement), FCC, etc., it’s like a “wack-a-mole” game. I mean when you shut one down, two more pop up. These scammers change hosts like the rest of us change clothes every day. Nevertheless, I value the LE approach and am grateful they are doing their job.
But I think the education of novices is also needed. Problem with that is the old “You can lead a horse to water, but can’t make it drink.” thing. As much as we try to educate these folks, it’s dependent on their willingness to consider the cautions we make. They either are not “interested” (’till they get scammed), or, as you say, think they’re experts and follow their own crooked path to disaster.
So, we are reduced to wack-a-mole and trying to get that horse to drink. Still, it’s all a worthwhile effort, even though it can be frustrating at times.
@ Susana,
I think Dave or Jim are best suited to answer your question, so I’ve emailed them and hopefully one or the other will pop in here and answer your question about that “SHARE thing”. I really don’t know how to make it go away (I’m not even sure a user can do that), but if I did I would tell you.
Thoughts, Dave, Jim?