Ok, so technically, someone tried to hack into my home network. Although they did not get in, I thought it would be informative to go over what happened. In this article, I will explain the different methods used to get into my network, what the hackers could have potentially acquired, and the steps I took to strengthen my network security.
Methods To Connect To My Home Network
The first way to access a home network is to plug an Ethernet cable directly into the network. This would require a hacker to be physically on my premises. I use door locks to keep individuals out of my home.
WIFI is the second access method. A hacker trying to connect to my network wirelessly would have to be within a few hundred feet of my home. Wired Equivalent Privacy (WEP) was an older protocol that was insecure against modern attacks. In 2003, Wi-Fi Protected Access (WPA) came out to replace WEP. WPA brought updates, including the Temporal Key Integrity Protocol (TKIP). A few years later WPA2 came out with improvements, the most important being the upgraded AES-CCMP encryption. Recently, WPA3 arrived with security improvements. However, because many legacy devices are not supported, WPA3 has not seen widespread adoption. To prevent a wireless hacker, I use the strongest wireless authentication method that my router and clients can employ. In my case, that is WPA2-Personal. I use a random 32-character password (the largest that all of my clients will accept).
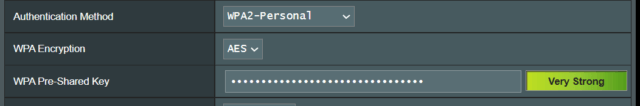
Remoting into the network’s router is another way to connect to the network. To protect my network from this, I have disabled all remote access.
A server would be the final method of accessing my network. A server is software that processes requests and delivers data to another computer. The only server I have set up on my network is a VPN server. A VPN (Virtual Private Network) is a mechanism for creating a secure connection between two computing devices using the insecure Internet as the communication medium. The VPN creates a secure communication tunnel between the client and the server. Many employees use a VPN client to securely connect to their employer’s network through their employer’s VPN server. You may use a VPN provider (NordVPN, ExpressVPN, ProtonVPN, etc.) to hide and/or change your location by securely connecting from your computer (via a VPN client) to your provider (via the VPN provider’s VPN server). You then connect to the Internet from the provider.
I set up an OpenVPN VPN server on my router to securely connect to my home network when I am away from home. The VPN server allows me to tunnel into my network and perform any function on the network as if I was in my home, even if I am on the other side of the world. For example, if I need a file stored on my network, I can get it. This is how the hacker tried to get into my network.
How I Discovered The Attempt
I looked at my router’s log and saw MANY entries that looked like this:
ovpn-server1: 89.161.47.252:35102 TLS Error: TLS key negotiation failed to occur
ovpn-server1: 89.161.47.252:35102 TLS Error: TLS handshake failedThis showed someone trying to hack into my OpenVPN server. They failed but kept trying.
If They Got In
The hacker could have accessed my router and changed its settings. I have a Network Attached Storage (NAS) device with backups and storage of my data which the hacker could have gained access to. The hacker could have acquired access to any computer, tablet, or phone connected to my network. Finally, to a lesser extent, they could have gained access to media servers, security cameras, or IoT appliances connected to my network.
But, even if the hacker had successfully bypassed the security on my VPN server, they would still have had to bypass the security on the various network devices. So, there was still another layer of security to get through.
What Changes Did I Make
Although the hacker did not get into my network, I decided to tighten up my network’s security.
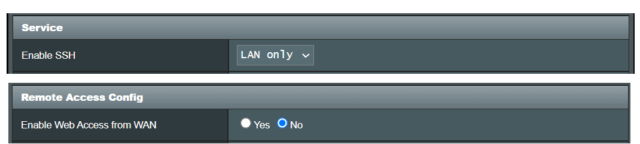
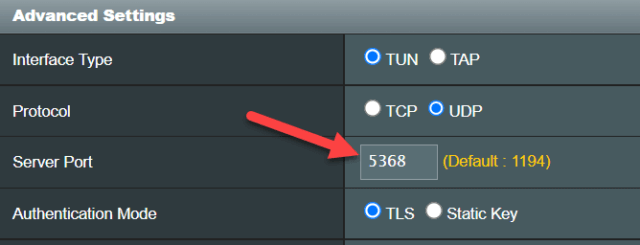
First, I changed the VPN server’s port from the standard 1194 to an unused, unallocated port (5001-32767 on my router). Using a non-standard port greatly reduces the chance of the VPN server being detected. Second, I increased the password length for each VPN server user from 12 to 32 characters.

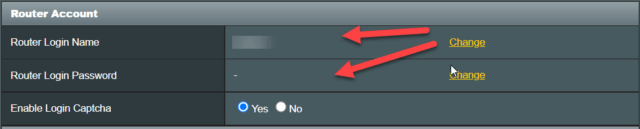
Next, I changed my router’s name and password. It was good that I did not use the default name and password (admin, admin for my router), but I still increased the length of the name I used and the length of the password from 10 to 32.
I went through my NAS and encrypted all files that contained personal or sensitive data. I did the same with my computers. I will have an upcoming article on the secure encryption tool I used.
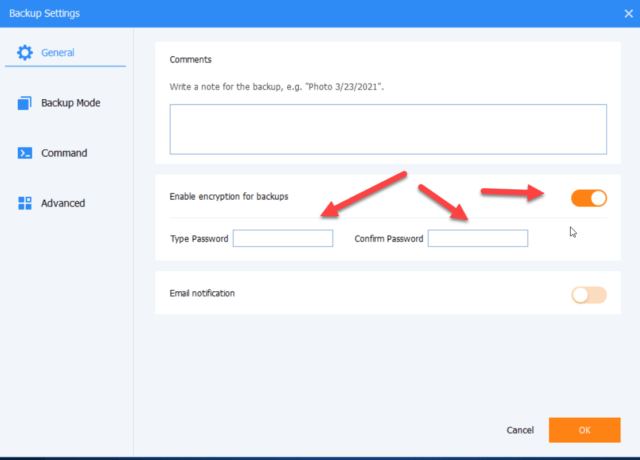
Finally, I decided to add encryption to all backups that I make and store on my network. Over the next month or so, as my old unencrypted backups cycle out and are replaced with new encrypted backups, everything will be encrypted.
If you have any questions, please leave a comment below.
—

Good article! I recognize the ASUS UI as I use ASUS AiMesh too.
Hi Bruce,
Good eye! I have Asus routers but I actually run an alternative, customized version of the Asuswrt firmware – Asuswrt-Merlin on my router.
https://www.asuswrt-merlin.net/
I do run the stock Asuswrt firmware on my AImesh node though.
Great informative read.
I should add that RDP seems to be a common way that people get breached. Often they have a poor password or a breached password and there’s no group policy rule to block after so many attempts
Thanks Peter,
Glad you enjoyed the article. Good point on RDP. I don’t do a lot of remote desktoping and don’t use RDP, but our Jim Hillier recently had an article on 2 portable RDP alternatives https://davescomputertips.com/2-free-portable-remote-desktop-applications/ Not sure if they have similar susceptibility issues though.
Thanks John – as a recent newbie into the NAS world I originally used the APP provided by the company (Synology) to be able to access files. Then I saw a security video stating that having a password protected way to log in was increasing the risk of getting hacked so I disabled it. Would like to be able to log in though remotely to get a file or whatever so if you have a chance to show how you set up your more secure VPN access I’m in !
If a hacker gets in through the NAS will also have access to other PC’s running on the network ? And if they don’t have both your UserName and Password are they just hoping you have left the Username as Admin and then trying brute force on the password ?
Hi Reg,
There are a lot of ways to attach storage to a network. I don’t use Synology and am not familiar with the APP, but the advice of having a password to connect being less secure sounds counterintuitive to me. I require a password to connect to my storage. I mostly connect to my storage with Windows. In Windows, when I add a network location to the storage, I add the password once and Windows remembers it after that.
As for setting up a VPN, there are a lot of variables involved. What hardware and software are you using, what type of VPN do you want to set up (IPsec, PPT, OpenVPN, WireGuard, etc). And, even how you are connected to the internet — with a static IP address or dynamic IP address. I can tell only tell you what I did. My router allows me to set up a VPN, and its CPU is powerful enough to run it easily. I set up an OpenVPN server on my router. I have a dynamic IP from my internet provider (my IP address changes every now and then). To connect to this dynamic (changing) address I set up a DDNS (Dynamic DNS) on my router. There are lots of DNS providers and I set mine up on the dynamic DNS service afraid.org and I use DNS-O-Matic to announce that.
As for the router username and password, most routers come with defaults. Common ones I have seen are admin/blank admin/admin and admin/password. A lot of people never change this when they set up their routers. If you have changed these, then a hacker would have to attack them using some form of a popular passwords list, dictionary lists, patterns lists, and finally brute force to try and break in.
Thanks John – I may have to learn and research a bit more about setting up that VPN as that sounds a bit beyond my tech skills at the moment. Will definitely check to see if UPnP is disabled though
Cheers
Reg
Reg,
Out of curiosity, what router do you have?
Thanks John
Your article is a very useful reminder of the need to take router security seriously….
In addition to your points above – I believe it is also worthwhile disabling UpNp (Universal Plug and Play.). A brief search on the web will show why we may be trading security for convenience by using UPnP.
Your thoughts?
Hi Gavin
I have UPnP disabled. When enabled, UPnP has zero configuration. Connections are automatically established. Clearly, this is a security risk!
I also have WPS disabled for similar reasons. WPS PINs are very easy to “brute force” by guessing different combinations. A WPS PIN can be brute-forced in about a day.
I went through a similar experience about 5 years ago. I got into a heated argument on Fascist book and the other person proclaimed that SHE was a US NAVY Criptographer and intended on hacking my computer, doing a deep dive into my background, and Exposing all of my CRIMINAL history across the WEB.
I replied to her with the Address of a hacking site that gave exact instructions on how to go about the process. About 20 minutes later I got a notice from my computer that it was rejecting an attempt to gain access that it didn’t see as legitimate.
It was totally comical and that was prior to me getting a VPN. I did report this person to the DoD and IF ‘SHE’ was anyone involved with security at a Government level she is probably behind bars now.