How much damage getting hacked causes you often dictates how much you should care. If your mobile phone that’s only used to play Plants vs. Zombies gets exploited you probably won’t care. Your main computer getting hacked with banking access and email logins may take more time to recover from. So, how much do you care?…
My personal computer has little information that a hacker will find useful. My work computer getting hacked will lead to me losing money, time, and clients. For that reason, I tend to be a little more careful while working than I would if just playing games and watching YouTube.
I have studied hacking and cracking since my first website was hacked, almost 17 years ago.
I work as a programmer for a company called Judd associates. During the day I develop and market websites. At night I have always enjoyed learning about the more nefarious forms of programming. Kind of like dessert; saved until last. The advantage of learning the techniques has been to help protect my friends and clients from such attacks. So, consider yourself a client and let’s get started…

Browsing
If you have an internet connection, you probably browse the interwebz. Websites are the biggest attack vector, by a considerable margin. The two best ways to avoid getting viruses from infected or malicious websites are… *drumroll*
- Antivirus software
- Script/Advert blocking plugins
Preventing scripts from running is a little too heavy handed for most users as it’s a fundamental technology upon which the modern internet relies. So, we must make sure we block only known exploits.
Choosing a reputable anti-virus program is essential these days. Differences between the top 5 programs is negligible though. Even the most trusted websites can get compromised and deliver malicious code. These can come in the form of plain old data exfiltration (stealing passwords), to the lesser known vector called a watering hole attack. Attackers leverage the large user base of popular websites and insert malicious code to specific visitors. Want to buy a botnet made with Win2k servers? Done. Most things are for sale on dark markets.
Installing anti-virus software isn’t enough as exploits are discovered and made public on a daily basis. I always advise to set updates to “automagically”.
Email infections are fairly common and easy to obfuscate (that’s geek for hide). More so in the corporate environment than personal email accounts, but it’s still worth being a little mindful before making assumptions — some people call it paranoia, I call it common sense paranoia. Sometimes, they really are out to get you.
So what can we do to protect ourselves from email hackers? Most attacks perpetuated via email fall into one of the following categories:
- Phishing — Impersonation of another website.
- Malware distribution — Sending virii as attachments or links.
- Fraud — Claiming you have won, inherited, want to invest money.
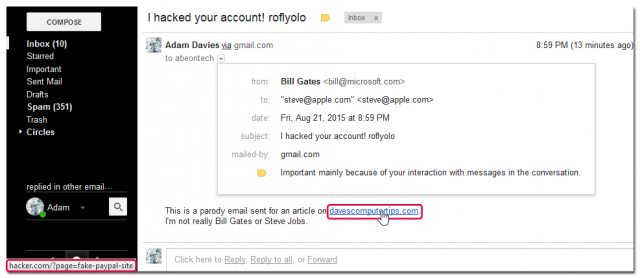
All of these may seem obvious to avoid but can be very convincing on first glance. It’s usually only after something stands out that we get suspicious. Let’s take phishing as an example. Below is an email I sent to myself to show how manipulating email data is fairly easy to do. The link to davescomputertips.com, pictured below, could easily be a login page I host which looks identical but steals your password and logs you in afterwards.
Check all links before you click them and don’t assume an email is from the person the sender suggests.
Aside: If you have been victim of an email scam, check out the 419 eater archive for a little morale boost. Some people scam back! If nothing else I like the idea of wasting their time and money to make it less viable as a business decision.
Banking
Most banking websites now use second factor authentication such as a PINsentry, text message, or mobile app. This is a great improvement but not perfect. The internet was developed before security was an issue. HTTP was, as the name implies, designed to transfer text documents and links from one computer to another. Tim Berners-Lee could never have imagined that online banking would end up using the same transaction process.
If the bad guys can “hack all the things”, and they can — under the right circumstances, what can we do to protect our banking information? It’s actually pretty simple and only takes a little heightened observance while using their services. Below is a list of things to keep in mind while using banking services:
- Wireless connections can be spoofed, hacked, and MiTM‘d.
- Mobile phones can be hacked to send data to another server.
- Some viruses specifically target banking details.
From the above list, it’s obvious that using an internet cafe can be hazardous. A malicious user could install software to capture your login details or use a Man in The Middle attack to spoof your session. Using a mobile application to authenticate your details isn’t such an obvious vector, although common. Hackers have been known to upload fake apps to the Google play/iTunes stores which contain code that sends your banking details to their servers. Installing an app called “Cracked CandyCrush Infinite Gems Latest Version!!!” will probably lead to bad times. Yet again, up-to-date anti-virus software on your computer and mobile phone will help mitigate these attacks to a massive degree.
Illegal downloads
Illegal download sites have always been a popular infection method. Users are typically more prepared to disable anti-virus software, install lesser-known plugins and SDKs. Simply to get around paying for the latest release they’ve downloaded. It should go without saying, but doesn’t: if you download films, games, or anything from an illegal website you are an open target.
Recent efforts by governments, police forces and Google to use DMCA legislation to take down many websites providing illegal downloads has largely been positive. Closing down the largest file sharing websites has, however, led users to look elsewhere. Hackers have noticed this and responded by setting up authentic looking download sites that distribute their malware. Unless you consider yourself more knowledgeable than those distributing such malicious software, be extra careful.
Sometimes, even hackers get hacked when downloading hacks. Savvy?
There you have it. The 4 things I’ve done to avoid getting hacked for almost 17 years. And I visit the shadiest places on the internet. For (computer) science, of course.
A good article Adam, and one thing annoys me, you can yell from a mountain-top or write it in the sky, and too many people will ignore the message, “Do NOT use weak, simple passwords.”
Greetings.
While reading your article 4 Tips To Avoid Getting Hacked, I came across “virii”. I had to do a double take. There is no such word. Please try to write more sensibly.
Norman.
‘Viri’ (or even ‘virii’) is often used as the plural of ‘virus’, because of the ‘…us’ ending and Latin plural standards. Neither is correct unless one wants to use ‘folk’ etymology.
The word ‘virus’ has no plural in Latin as it is a mass noun, therefore Latin standards don’t apply, and the plural of ‘virus’ is ‘viruses’.
More or less, the same goes for ‘interwebz’.
Thanks for the input Norman and SirPaul2. I intentially went back and replaced an instance of viruses with virii for two reasons…
1 – If we never challenge these archaic etymological constructs, our language would never have evolved past the Latin language from which it originates.
2 – Many people search using terms including “virii”. We would like them to find this website, if possible.
For those reasons I will continue to use the word as much as I hear it spoken. Maybe one day it will be seen as word worthy as such recent admissions to the dictionary as selfie.
Thanks for the feedback Jon. Of course I agree. Having a strong password is the ultimate way to protect your account, especially if a website database gets hacked as it will make cracking it harder!
Not to be nitpicky…but I do believe you meant “dessert”…which normally comes after dinner for me unless, of course, it’s my homemade Boston Cream Pie and then I’ll just bypass dinner completely…and not “desert”. :-p
“Kind of like desert; saved until last.”
Good catch speppers. Now corrected. Thanks!
Yep, nice find. Really need to get my beauty sleep before posting next time. Thanks speppers69 🙂