Much has been written about PC security and how it can be enhanced per medium of adopting a layered approach, which generally means installing different types of products to help cover a wider scope of eventualities. I employ such a strategy myself, albeit in a fairly basic form; Avast Free, WinPatrol and Sandboxie. These three products have stood me in good stead for a number of years, I can’t even remember the last time one of my machines was infected. Both Avast and WinPatrol are very well known, WinPatrol in particular enjoys legendary status. Sandboxie is also quite well known yet, in my experience, substantially under-utilized. I don’t quite understand why that is the case; Sandboxie is simple, very easy to use, very effective and free. Perhaps it can be put down to a certain mystique surrounding sandboxing and virtual environment techniques in general. Whatever, I hope what follows will help clarify and maybe encourage more users to take advantage of this terrific software.
- Secure Web Browsing: Running your Web browser under the protection of Sandboxie means that all malicious software downloaded by the browser is trapped in the sandbox and can be discarded trivially.
- Enhanced Privacy: Browsing history, cookies, and cached temporary files collected while Web browsing stay in the sandbox and don’t leak into Windows.
- Secure E-mail: Viruses and other malicious software that might be hiding in your email can’t break out of the sandbox and can’t infect your real system.
- Windows Stays Lean: Prevent wear-and-tear in Windows by installing software into an isolated sandbox.
Sandboxie is a mere 2.2MB download, installation is clean and straightforward. To complete the process Sandboxie will install its own service Sbie.Svc.exe. This is Sandboxie’s core component and, although it is not necessary to have Sandboxie itself auto-starting with Windows, it’s imperative to leave this service enabled and running at all times.
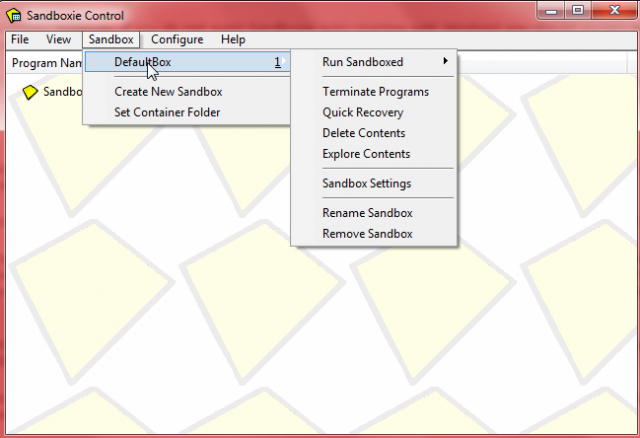
Sandboxie is operated primarily via the Sandboxie Control window which is accessible from the Start menu. The interface is entirely minimalistic, simply click on the Sandbox menu item, then on DefaultBox to reveal Sandboxie’s main options:
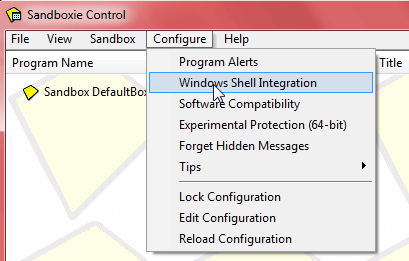
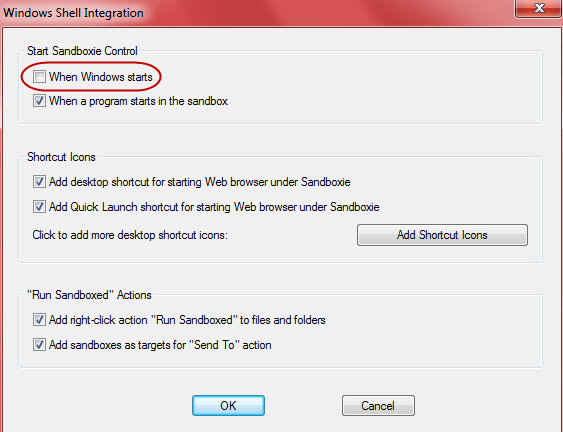
Default configuration will be fine for the vast majority. However, if you do not want Sandboxie auto-starting with Windows you should access Windows Shell Integration from the Configure drop-down menu and disable that option:
Sandboxie places a special folder in the root of ‘C’ drive and this is where all data created while running sandboxed applications resides. In other words, this folder represents your virtual environment – all data related to any actions performed inside Sandboxie will go into that folder:
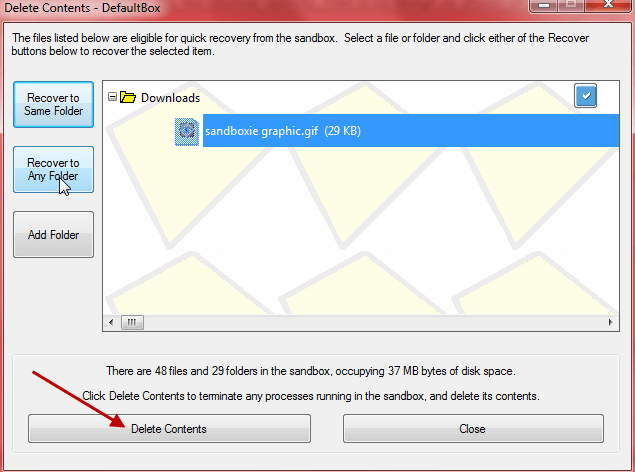
When you have completed your task, whether it be a browsing session or testing software, simply initiate the ‘Delete Contents’ option and Sandboxie will empty that folder, all associated data will then be gone – including any nasties accumulated along the way.
This isolation technique is eminently suitable for many situations; it all but guarantees a perfectly safe browsing session and you can test install software with total immunity from malware or unwanted extras which install without permission.
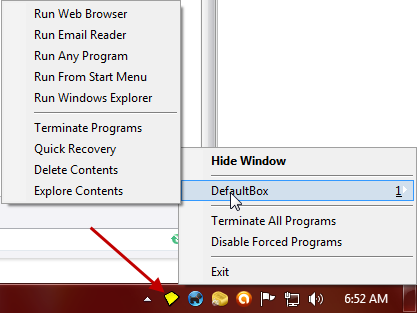
Sandboxie’s options are also available via the program’s system tray icon which appears whenever Sandboxie Control is running; simply right click on that icon and then left click DefaultBox:
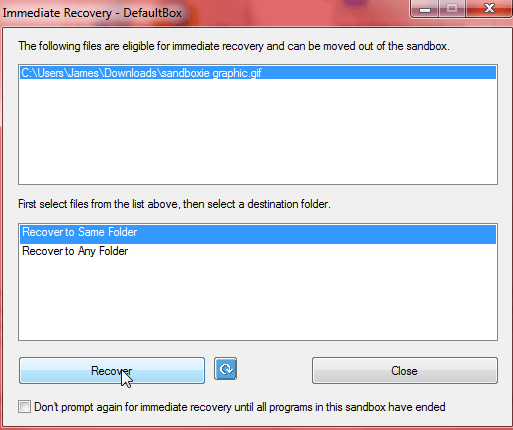
Selecting Run Web Browser for example will open a sandboxed instance of your default browser where you can surf around safely until your heart’s content. If, during a session, you happen to download anything you wish to keep, an image or file perhaps, Sandboxie provides options to ‘recover’ the file(s) via two methods; 1) an immediate prompt once the download has completed and 2) at the termination of the session when you initiate the Delete Contents option (use the Recover to Any Folder option first and then click on the Delete Contents button to get rid of the remainder):
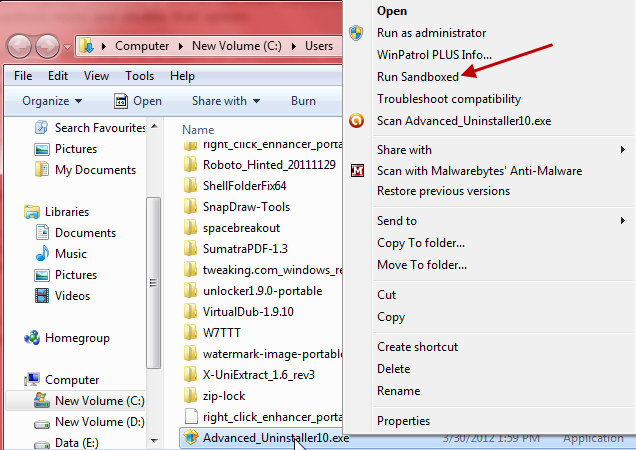
Sandboxie also adds an entry to Explorer’s right click context menu, right click any file and it can be run sandboxed. This is useful for handling any suspect files and particularly so for testing software – simply right click on the setup (execute) file and select Run Sandboxed:
Now the program will be installed entirely inside the sandbox, you can run the software and work with it as usual. When finished simply delete the contents of the sandbox and everything is gone – your system remains unchanged and unaffected.
I recently tested a similar free program from Toolwiz called TimeFreeze, you can read through that review HERE. So which do I prefer? Sandboxie, hands down! I’ve since experienced some issues with TimeFreeze, specifically after the reboot process. The system has occasionally restarted with a service randomly disabled, it has been a fairly simple fix – just go into Services and restart/reset the appropriate service. Still, it shouldn’t be happening and I can’t help wondering what else might be adversely affected. I sent a ‘please explain’ type email to the Toolwiz support team but have not received a response to date. That was weeks ago so I doubt anything will be forthcoming now.
In a nutshell; Sandboxie is tried and true (reliable and safe) – TimeFeeze has yet to pass that test. Sandboxie does not require a reboot, simply delete the contents – TimeFreeze does require a reboot, and I believe this is the aspect which makes it susceptible to problems. Any hiccup during the reboot process and who knows what might happen.
I hope after reading this you will understand Sandboxie a little better and just how useful this small program can be, Sandboxie is a wonderful security tool which should be utilized by everyone.
NOTE: The free version involves a 5 second delay prior to initialization of the selected operation.
- Sandboxie HOME PAGE
- A comprehensive ‘Getting Started’ guide is available HERE
- Download from FreewareBB HERE

Jim,
Thanks for your easy to understand and enthusiastic overview of Sandboxie. I have considered giving it a go several times in the past, and believe that I will do so now based partly on your recommendation. As always, I very much appreciate all of your efforts here.
John
Hey John – Pleased to hear you are going to give Sandboxie a try – guarantee you won’t be disappointed.
Thanks for the kind words,
Cheers… Jim
Avast paid version has Sandboxie included (mine is about to expire). What about Wondershare Time Freeze. Seems to be a similar program.
I have this; I just keep forgetting to start it before downloading software. :[
Hey Mizdoc – All Avast editions include a sandboxing function, even Avast Free… but it is not Sandboxie, it is Avast’s own version of sandboxing.
Wondershare Time Freeze is payware (costs $39.00) and requires a reboot to clear changes… as already stated, that’s a system I believe is susceptible to issues.
Cheers… Jim
Well, I did not know that. Thanks for the heads up. Must be new in the past year, ’cause I used Avast Free before this past year and never saw it.
I got Time Freeze in a giveaway, but don’t keep it running unless I’m installing something I’m not sure I want to keep. Seems TimeFreeze wants me to disable System Restore if I run it all the time, and I’m not willing to do that. As far as Sandboxie goes, it looks a bit too involved for me, so guess I’ll just go back to Avast Free, now that you’ve told me it has it’s own sandboxing version. Hopefully that’s enough for me.
Thanks Jim, for the info…
PS…I see you were a Commodore groupie too. I started out with the good ol’ Vic 20 and I was hooked!
Traded in my Commodore 64 for my first PCin ’95 when I heard Commodore was closing down shop.
They were great machines, weren’t they? Wish I still had mine.
Yes Mizdoc, the sandboxing component in Avast is very new.
And yes, I am a Commodore man from wayback. Still have a working ’64’ and Amiga 500 but haven’t fired either up for ages. They were terrific machines, and great fun in their day.
You might be interested in this: http://www.commodoreusa.net/CUSA_C64.aspx
I must admit I have been very tempted. 🙂
Cheers… Jim
Hi Jim, I too have been considering Sandboxie for some time, I used it on XP and when I got Vista (64), I went to their website where there was a curt notice stating something about not being to work wit 64 bit due to measures taken by Microsoft. Then I read your article and thought “great – we’re back in business”,
So I downloaded and installed on my now Win 7 Home Premium (64). I got three error messages and codes. Following the web links was a waste of time. Uninstalled and cleaned the registry, retried in ‘Safe Mode’. Same result. Checked on Sandboxie web site, the say it’s good for 64 bit.
It’s either my machine or a conflict with my A/V or other software. I not prepared to play with those, if Sandboxie doesn’t run out of the box then I won’t trust it. I will try something else.
Indecently, I now use Revo Uninstaller Pro to install (and if necessary,uninstall) software unless it’s portable. I cannot speak too highly about it, but even that some times leaves some registry entries. Yes I do reboot before checking the registry.
Anyway, sorry for going off post and thank you for much valued reviews!
jayesstee
Hey JST – I am using Sandboxie in a Win 7 Home Premium 64-bit system, no problems at all. I’m disappointed to hear Sandboxie does not work properly for you.
I don’t believe it is a 64-bit issue, more likely a software incompatibility – Sandboxie includes a built-in software compatibility scanner, the results of which are listed in the ‘Sandboxie Control’ window under “Configure/Software Compatibility”. If you access that section you will see a list of installed software which is liable to cause issues. Just click on the “OK” button and Sandboxie will apply configuration settings to improve compatibility with those products.
Cheers… Jim
Tried it again twice! First time I directed it to install in my app. partition, second time I allowed default installation.
Both times a succession of error messages: “can’t find this”, can’t find the other”. No desktop Icon either time.
Same decision as before, but now with more resolve.
Thanks for your help,
jayesstee
Thanks for the article. It was very informative. If I install a program sandboxed and it interacts with a non-sandboxed program what happens with the data from the non-sandboxed program? I’m not sure if that’s a good question or if I’m thinking about this the wrong way? Hopefully you’ll understand my concern. Thanks in advance.
I’m not sure the scenario you put forward is even possible – can you please give me an example of a program “interacting” with another completely separate and different program. Did you have something specific in mind?
All actions initiated inside the sandbox are isolated within the sandbox, as is any associated data. Say, for example, you were to run a sandboxed instance of MS Word – you type in your text, insert images, etc. and then save to ‘My Documents’. You will not find that document saved in ‘My Documents’, it will be inside the sandbox. From there you can either choose to ‘recover’ the document and save it to a location outside the sandbox or delete the entire contents of the sandbox and everything will be gone – there will be no record that the document ever existed.
Cheers… Jim
Having played around with it more I can see that I wasn’t making any sense, so disregard earlier my question.
I’m using sandboxie to install programs so they do mess with my main install of windows. I then make a shortcut of those sandboxie installs on the desktop. All the icons have the same sandboxie yellow and red icon. Do you know how to change the icon to something else? I’m on windows 7. I’ve tried the normal way (right click/properties/shortcut/change icon) but that doesn’t work since the “start in” link is to a sandboxed folder. I thought maybe it would work if I did it in a sandboxed explorer window and it did, but only in the sandboxed version of explorer. Any advice??
I found a solution but it’s not very elegant. I just make a dummy folder for the non-sandboxed programs folder that corresponds to the folder it’s looking for in the “start in” link of the shortcut. Then delete the dummy folder after I’m done. Any better ideas?
I figured it out! Now all my shortcuts have the correct program icon.
Click the notification area of windows and open the Sandboxie icon
Right click on the sandbox with your program installs and choose “Explore Contents”
Drive/C/Program Files/the installed program
Right click and drag program icon to unsandboxed shortcuts folder and choose “Create Shortcut Here”
Although I’m still not certain of what it is you are trying to achieve Tat, glad to hear you persevered and finally worked it out… well done!!
Cheers… Jim
Hi, thanks for this article. What I don’t understand is once you’ve installed a program in a sandbox how you then run it from inside the sandbox? For example, I’ve installed IE6 in a sandbox for testing. Great. Apparently it’s there. So now how do I run it? Where is the .exe file? Or is the usual way to create a shortcut? If so, what path do I use?
Hi Jamie – If a program does not automatically launch at completion of the installation you will need to start it manually. The execute file, along with everything else, is included in the sandbox. Just choose to “explore” the contents of the sandbox, locate the program’s execute file and double click that.
NOTE: Not all programs will run successfully when sandboxed, some require external associations.