 Malwarebytes Anti-Malware (MBAM) is one of my all time freeware favorites, and I am certainly not alone in that regard – MBAM is one of the most downloaded freeware programs on the planet. Malwarebytes Anti-Malware follows a common ‘freemium’ distribution model, with the free version providing one of the best (if not the best) and most effective on-demand malware scanner/removers available while the paid for version includes the additional security afforded by real time protection.
Malwarebytes Anti-Malware (MBAM) is one of my all time freeware favorites, and I am certainly not alone in that regard – MBAM is one of the most downloaded freeware programs on the planet. Malwarebytes Anti-Malware follows a common ‘freemium’ distribution model, with the free version providing one of the best (if not the best) and most effective on-demand malware scanner/removers available while the paid for version includes the additional security afforded by real time protection.
What many users may not realize is that Malwarebytes also offers two other relatively recent free security tools… Malwarebytes Anti-Rootkit (AKA MBAR) and Malwarebytes Chameleon. MBAR was first released almost 12 months ago and still remains in Beta stage, which may seem a rather protracted Beta period. However, considering the huge and diverse variety of software configurations out there, it would be nigh on impossible for Malwarebytes labs to predict and test for all possible situations, so they rely on users for final testing and feedback… that’s what Beta is all about. Malwarebytes CEO and founder Marcin Kleczynski had this to say:
With MBAR we have been running the open beta now for almost a year successfully, and while there is a small chance specific configurations could pose issues; we are confident for most users MBAR will be extremely effective against any rootkit infections they encounter.
Rootkits are particularly pernicious little devils and removal often involves damage to the system. That’s because rootkits bury themselves deep into the operating system, replacing critical files with those under the rootkit’s control. So it’s not always just a simple matter of identification and removal, it also often involves a certain amount of damage control. I’ve been following MBAR’s progress with interest for some time, I may have even mentioned it here at DCT at some time, but I’ve always wondered why this latest tool was not included as a component or feature within MBAM itself. We now have the answer, coming from Marcus Chung, Executive Vice President and COO at Malwarebytes:
The bad guys have the edge when it comes to rootkits, they aren’t too worried about breaking the host computer, but we are, very much so. Having a separate tool allows us to make absolutely sure we minimize the risk of breaking the host computer.
Marcus also pointed out what now seems pretty obvious, that it’s all about reaction times. Rootkit developers have become adept at quickly morphing their code once they learn that rootkit removers recognize their handiwork. Using a separate tool, MBAR’s developers can react just as fast without any concern of damaging a larger, more complex program like MBAM, and also avoid the logistics of rolling out a new version of MBAM each time.
Makes perfect sense to me.
The second of the two, Chameleon, is (as the name suggests) pretty much Malwarebytes Anti-Malware in disguise. It’s specifically designed to help overcome those times when malware recognizes the security scanner you are attempting to install or run and prevents you from doing so. Chameleon fools the malware into believing it is something else altogether, allowing it to start and hopefully destroy the infection.
Lets’ take a closer look.
Malwarebytes Anti-Rootkit:
Unlike its big brother, MBAR is fully portable. Simply download the 13.1MB zip package available here: http://www.malwarebytes.org/products/mbar/, extract the contents and then double click mbar.exe to run.
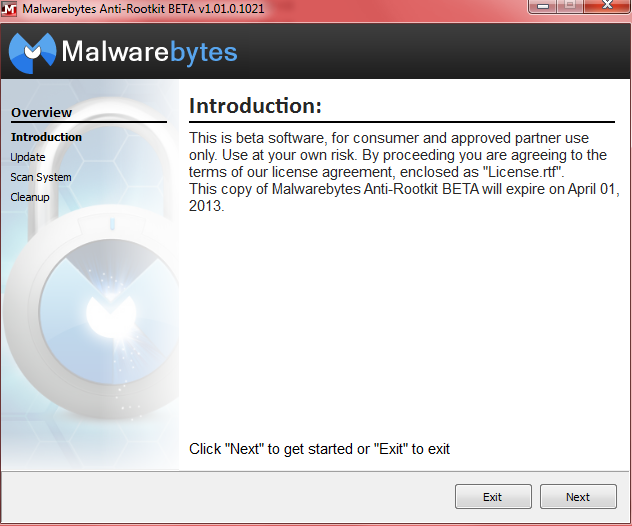
The initial screen is merely a warning regarding the Beta situation which we have already covered. Down the left hand side under “Overview ” you will see the steps set out in logical sequence – each click of the Next button will take you through to the following step:
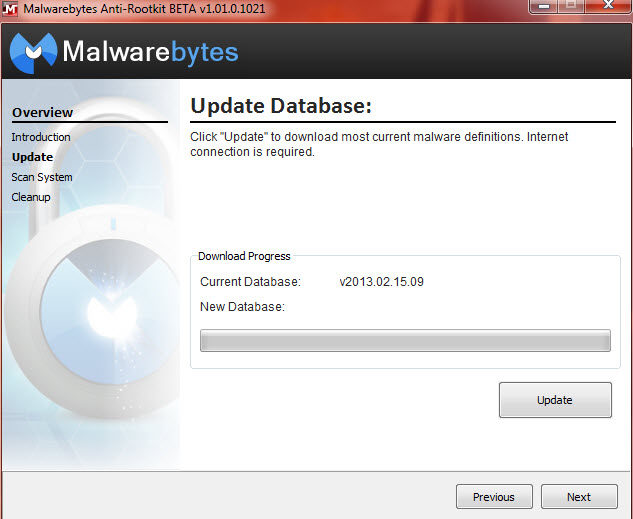
Update: downloads and adds the latest definitions
Scan System: around 5 minutes to completion on my Win7 64-bit system
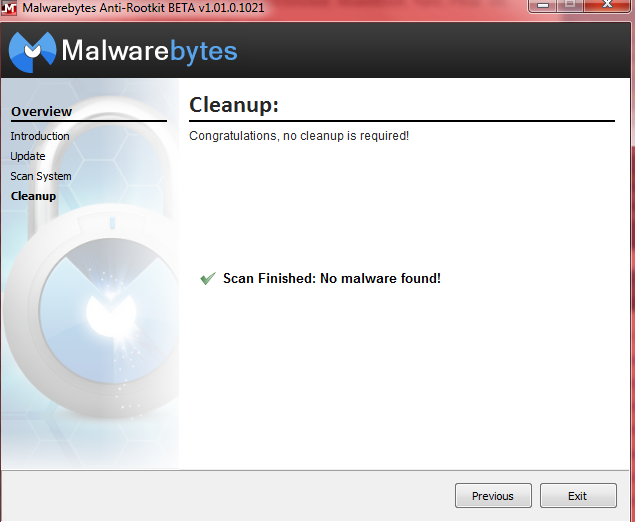
Cleanup: if you are fortunate and your system is clean you will see this
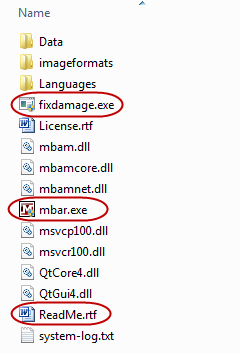
In the following screenshot I have highlighted three of the files included in the MBAR folder:
- ReadMe.rtf – because it contains useful information which you should read through.
- mbar.exe – to help identify the correct file to run MBAR… and
- fixdamage.exe – because that is the file you may need to run to fix any damage following identification and removal of an infection
If after running the MBAR, restarting and verifying that the system is now clean of infection you experience other problems, such as lack of internet connectivity then run the tool fixdamage.exe included with the package. It will repair certain system services and settings which are frequently broken by certain rootkits. After running this tool you should always restart your computer even if it does not prompt you to do so.
MBAM is a very effective all-rounder but this little tool is dedicated specifically to the identification and removal of the particularly nasty rootkit family of malware.
Chameleon:
Did you know that, if you have the latest version of MBAM Free installed on your PC, then you already have Chameleon available? Yep, Chameleon is now included in MBAM’s program folder:
If you find that malware is preventing MBAM from running, simply navigate to and open the Chameleon folder, then click on the executable to run Chameleon:
If you do not already have MBAM installed and malware is preventing installation, Chameleon is also available as a separate 1.4MB zip download here: http://www.malwarebytes.org/products/chameleon/
History has taught us that the name Malwarebytes is synonymous with excellence in security software, and with these three tools on hand, you should be ready to tackle even the most stubborn of infections.


Except there is no fixdamage.exe on my C: drive, let alone in my Malwarebytes folder.
Hi Jim,
The fixdamage.exe is not part of Malwarebytes Anti-Malware, it is part of Malwarebytes Anti-Rootkit, which is a completely different and separate program requiring a separate download.
Cheers… Jim
Another top-class programme which I have been using for many years.
Good article, thanks Jim. 😉
Nice article Jim.I know Chameleon has been included for the better part of a year now (or so it seems),and I’ve used it to allow MBAM to retrieve definition updates on infected systems with a very high success rate.Though the process can lengthy while you search for the right “skin” so to speak.
I was not,however, aware of the rootkit Beta program,so many thanks for that info.I was wondering how it fares against the Aleuron family.
I’ve seen several PC’s come my way as of late with some form of this nasty little bugger.First symptom seems to be browser re-directs/hijacking.
I did see that BitDefender has released a rootkit scanner,but it literally runs in like 3 seconds,so I gotta wonder….
I’m hearing you Chuck! I’m generally wary of scanners which take no time to complete. It’s funny, most people will complain that a scan is too slow… my thinking is quite the opposite.
Cheers… Jim
Very good article Jim. Thanks. You may double-click on any of the files within Chameleon folder except mbam-killer.exe in order to attempt to launch Chameleon.
Hey Dacko – Thanks for the heads up mate… appreciated.
Cheers… Jim
Nice article, Jim. No PC connecting to today’s internet should be without it.
Glad to see you’ve mentioned this excellent program Jim. I’d like to add that the Pro version is very inexpensive (under $40 US), comes with a free life time upgrade feature (no additional yearly fees), and can be sometimes purchased with other software at a discounted price. Besides, only the Pro version offers real time (pro-active) protection. The free version is best in detection and removal once you’re infected. I prefer to remain uninfected, hence I own two registered copies of the Pro. Been depending on MBAM for years now and it works hand in hand with KIS as well, Mindblower!
Mindblower- I’ve picked that up as cheap as $11.99 for the actual CD.Not sure where you are located,but $14.99 is a frequent “sale price” at NewEgg.Further,you don’t actually need the CD for those interested.A key code received through your mail can be used to activate pro features in a previously installed free version.I would caution that you have a decent amount of Ram to take advantage of the real time protection afforded in the pro version.It is a bit memory intensive.
Tried to use the program. Error msg saying that Qtgui4.dll is not on my computer. When I open the files of the program, I can plainly see it there, but after I dbl clk the exe file , I get the error msg. Any suggestions? Thanks, Gerry.
Hi Gerry – What operating system? Have you definitely extracted the contents of the zipped folder? You will get this error message if you try to run MBAR from the zipped executable, the contents of the folder need to be extracted first and then run.
Cheers… Jim
i loves me my malwarebytes~!~!