 Nvidia has just released new Graphics Processing Unit (AKA dedicated graphic card) drivers across the board. News of this release has been well documented across the net, mainly because of the vulnerability/exploit concerns. However, it now appears that the story has been sensationalized somewhat and the security issue is not considered overly serious. The vulnerability was first brought to light by UK researcher Peter Winter-Smith who posted details on Pastebin. Following a flurry of articles which have tended to overstate the situation, Mr Winter-Smith has since re-asserted his initial stance that, given the conditions under which the exploit would have to be carried out, the issue was not particularly severe:
Nvidia has just released new Graphics Processing Unit (AKA dedicated graphic card) drivers across the board. News of this release has been well documented across the net, mainly because of the vulnerability/exploit concerns. However, it now appears that the story has been sensationalized somewhat and the security issue is not considered overly serious. The vulnerability was first brought to light by UK researcher Peter Winter-Smith who posted details on Pastebin. Following a flurry of articles which have tended to overstate the situation, Mr Winter-Smith has since re-asserted his initial stance that, given the conditions under which the exploit would have to be carried out, the issue was not particularly severe:
An attacker would only be able to successfully exploit the vulnerability if they were on a machine in the same domain and firewall rules were severely relaxed, or file sharing were turned on. With local access, an attacker could elevate their privileges to root, or if the above conditions were met, could gain remote access from the same domain. I’ve (fortunately) not heard of any reports of this issue being exploited in the wild; I didn’t anticipate that I would, given the constraints on the attack vector.
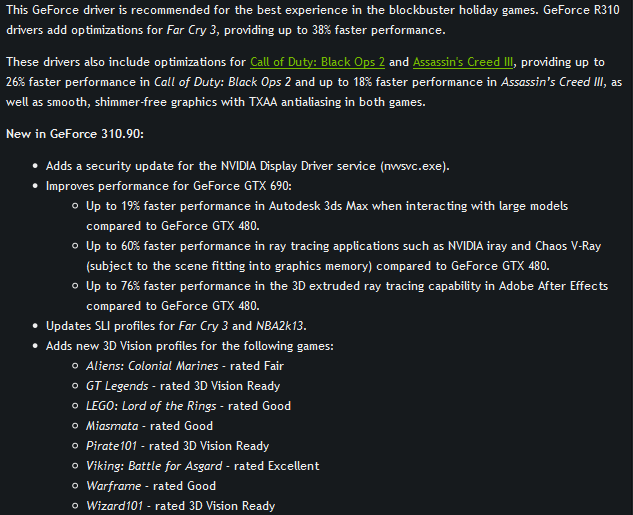
Even though the vulnerability is not considered to be particularly critical, the Nvidia driver update does include a patch which fixes the security flaw. The new drivers also enhance game play for certain titles:
What does this mean for you?
In layman’s terms; the vulnerability, as reported by Mr. Winter-Smith, can only be exploited locally… from a hands on position, and not remotely. This means that for the individual home user it presents a very low level of risk.
As far as drivers are concerned, I’m a great believer in the common adage… ‘if it isn’t broken, it doesn’t need fixing’, and I’m certainly no game player. That said, I’ll probably update my Nvidia graphic card driver at some time with this new version.
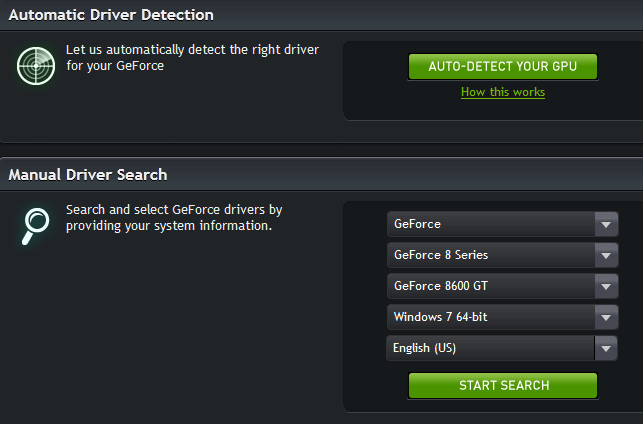
If you’re concerned at all about the security aspect or if you’re a game player who’d appreciate the enhancements, you can download the latest driver from the manufacturer’s website here: http://www.geforce.com/drivers
As you can see from the above screenshot, the page includes a tool which will scan your hardware and identify the correct driver for you:
NVIDIA GPU Reader is a web-based applet that identifies your GPU and finds the latest graphics driver for your GPU. A small Java Applet is downloaded the first time you run the service. This Java Applet only looks at and verifies your system components when you instruct it to do so from the website. This system information is then used to determine the best driver for your GPU.
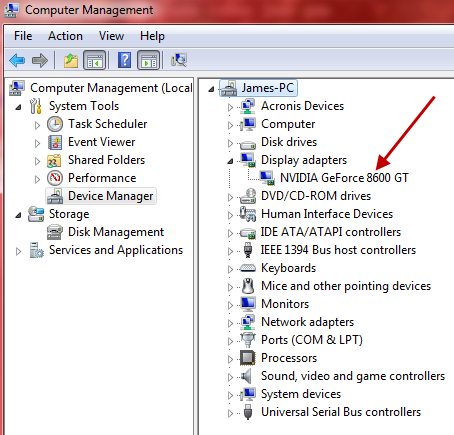
However, if you’re not entirely happy downloading the applet and/or allowing the scan, you can easily identify your Nvidia card model via Device Manager:
In Windows 7:
- Click on Start, then right click Computer and select Manage
- In the ‘Computer Management’ window, click on Device Manager (in the left hand panel)
- Look down the list for Display adapters and expand that entry
Armed with that information you can now use the manual system to access your new driver.
<source>
Thank you Jim for the heads up. I agree with “if it ain’t broke don’t fix it” and normally leave it at that but I’ve had good success with my Nvidia updates so I went for it. The security thing doesn’t look like much of a problem but I like to tweak the other functions to see if the enhancements are actually noticeable.
Regards.
I headed over to nVidea to update my Quadro drivers and low and behold Java is required for the auto-detect feature. According to CERT there is a known exploit in Java that could allow a “drive-by-download” attack. CERT further warns to disable Java in your browsers until the vulnerability can be patched. Do not worry, there is no problem with JavaScript however. Of course I’m pretty sure that http://www.geforce.com is a legitimate site with absolutely no ill will intended.
Peace and Prosperity to all..
Hi Eric – We have covered Java vulnerabilities here on DCT ad nauseam: http://www.davescomputertips.com/2012/08/java-zero-day-exploit-expected-to-spread/
It seems to be an ongoing and consistent issue, so much so that Dave actually published an article advising users to “Junk their Java” : http://www.davescomputertips.com/2011/11/you-should-junk-your-java/
I see one ‘expert’ is now declaring that, rather than continually patching these inherent vulnerabilities, Java should be rewritten from the ground up… not a bad thought.
Anyway, the Nvidia page clearly includes an alternative manual method for identifying drivers, as pointed out in the article.
Cheers… Jim