 It’s a fact of life, much like death and taxes, if you own and operate a PC for any length of time you are almost certain to encounter malware. This is an area where it seems everyone has an opinion and advice on how to proceed when a PC is infected, much of which is common sense but there is also a fair amount of misinformation involved.
It’s a fact of life, much like death and taxes, if you own and operate a PC for any length of time you are almost certain to encounter malware. This is an area where it seems everyone has an opinion and advice on how to proceed when a PC is infected, much of which is common sense but there is also a fair amount of misinformation involved.
There are several truisms associated with malware infections; one is that you can never be 100% certain that an infection has been 100% eradicated. You can be 99.99% certain, but the only way to be 100% certain is to completely wipe the hard drive and start all over again. Another is that prevention is better than cure, but while that sentiment is obviously sound advice, it is not always practical – no security product is going to catch 100% of malware 100% of the time (there’s another one).
There is one excellent method to remedy persistent and/or destructive malware infections. Unfortunately, it is a method which is most suited when initiated at the beginning of a system’s life and not so helpful for more time-worn systems. Here’s how:
When you get your new machine, or after a fresh install; setup your system the way you want; configure your settings, install all your favorite programs, etc. As soon as your system is just the way you want it, download and install free imaging software, there are several available, Macrium Reflect would be my recommendation. Then, use that imaging software to create a full system/disk image and save the image to external media (keep the media tucked away in a safe place). Now, if your system ever becomes so badly infected that it is unusable or irreparably damaged, restore the image that you saved earlier. It’s not ideal but it sure beats starting off from scratch again with a fresh install.
Okay, so let’s take a look at the remedial process and maybe debunk some of the myths:
1) Identify the problem – are you certain it is a malware infection?
That may seem a tad silly but you’d be surprised at how many people blame malware for literally everything. Just because a machine is running slowly or strange things are happening doesn’t necessarily point to a malware infection. Sure, it definitely raises suspicions but it is far from conclusive. The first step back to a healthy system is to determine if you’re actually dealing with malware rather than a problem with software, hardware, or maybe even PEBCAC (Problem Exists Between Chair And Computer :)).
Check for more obvious signs of malware; security programs disabled or refusing to start, processes with weird names appearing in Task Manager, native tools such as msconfig or regedit refusing to run. Of course, the most obvious of all is when a popup displays which actually includes the name of the malicious software, as is the case with many rogue security programs. In these instances it is often just a matter of searching that name with your favorite search engine to find a listed solution, or a software which is known to successfully rid the machine of the specific malware.
2) Scan the system – hunt down those nasty critters
Once you have decided that malware is indeed the most likely culprit and you have no idea what type of malware you might be dealing with, the next step is to perform system scans. At this stage scanning through your regular Anti-Virus program is not your best approach. After all, that program failed to indentify and prevent the malware in the first place. That doesn’t necessarily mean your Anti-Virus is not up to scratch though, don’t forget – nothing catches 100% of malware 100% of the time.
There are two ways you can go here; 1) online scanning, or 2) local scanning. If malware is preventing local scanners from running, then online scanners are your best bet. Either way, it’s generally best to perform the scans from within Safe Mode with Networking. Safe Mode loads a minimal version of the system with generic drivers only, and in some cases minus the malware. You will also need the Networking function to scan online or update definitions locally.
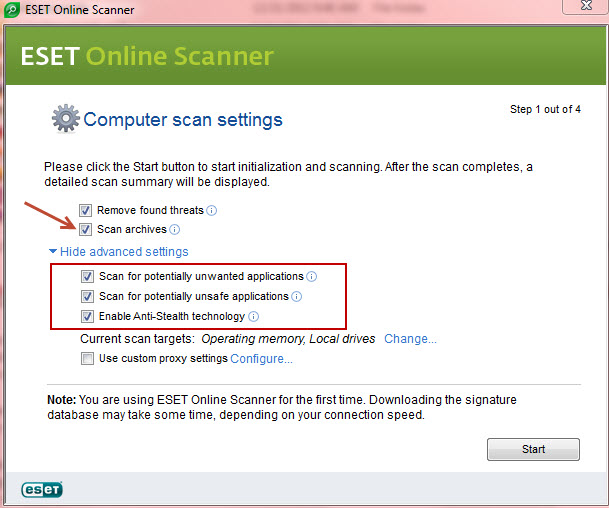
There are a number of effective online scanners available from reputable security software developers/vendors: my top recommendation is Eset Online Scanner – you will need to accept an ActiveX Control (Internet Explorer) or a small installation file (Firefox and Chrome). Also, before proceeding with the scan, make sure to enable Archive scanning, then click on Advanced Settings and enable additional options:
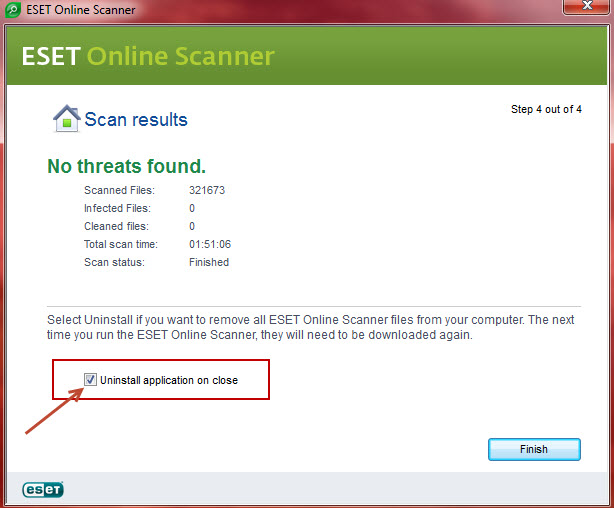
At the end of the scan, you will be presented with an option to uninstall ESET Online Scanner and all its components.
Top picks for locally installed scanners are Malwarebytes Anti-Malware and SUPERAntiSpyware. Malwarebytes in particular includes a “Chameleon” mode which can help overcome malware preventing the security software from running.
Finally, do not scrimp on the scanning process; always select the deepest scanning mode and do not rely on just one scan from one scanner. When you have completed your initial scan and removed any malicious files, check again, this time with a different scanner. It’s well worth the extra time taken to be assured by multiple scanners that your system is clean…. just for peace of mind alone.
3) Last Line of Attack
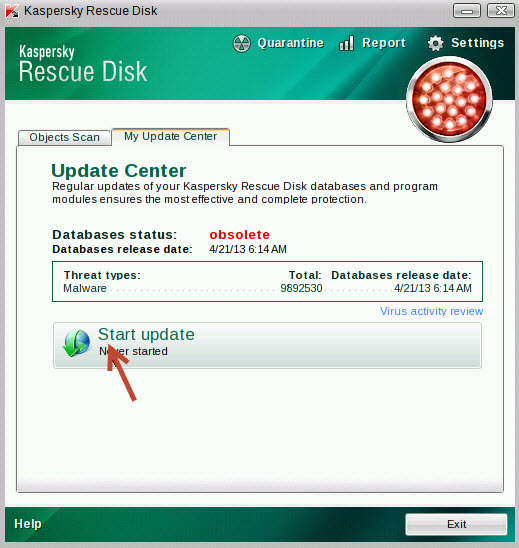
Of course, if the machine will not boot at all or is so badly affected as to be basically inoperable, you’ll need a scanner which can be booted from external media, generally a rescue disc. Most of the leading anti-virus/security companies provide this service; Dr.Web, AVG, Avira, Kaspersky, just to name a few. You will need to download an ISO file, burn to blank media, and boot the machine from that disc (there are some which also provide a bootable USB option). Rescue discs are generally Linux based but that should not present a problem, with most including a Windows-like interface. Arguably the simplest and easiest to use of these is ‘Rescue Disk’ provided by Kaspersky, which can be downloaded here: http://support.kaspersky.com/viruses/rescuedisk
Oh No! Not System Restore!
One of the most erroneous pieces of advice I often come across is to use System Restore to get rid of (or undo) malware infections. Unless you are 100% certain of exactly when the infection occurred and have a restore point which you are 100% certain will take you back to a previously clean state, this is patently bad advice. Yes, a user may be almost positive that the malware infection probably happened a couple of days ago but this is an instance where nothing less than 100% certainty is acceptable.
There are also those times when multiple infections are involved; where a series of malware infections may have gone unnoticed until that final piece of malware breaks the camel’s back. It is impossible under these circumstances for a user to know exactly when this all began. Without the benefit of an exact timeline, it is more than likely that most restore points will also include the malware infection(s). In fact, after recovering from a serious malware infection, my advice is to delete all previous restore points and start over.
Learn from the experience!
Okay, so ‘prevention is better than cure’ is a well worn saying, but that doesn’t make it any less applicable. Sure, your security program may have let you down, but installing anti-virus is only the beginning of security not the be-all and end-all. Most popular free anti-virus programs will do a good job for you but whichever you choose, it will need help, your help. Make sure you have the latest version installed and always keep those definitions up-to-date, surf safely, and above all… be aware!
Cheers… Jim
Hi,Jim,
Thanks for those info about OFFline scanners. I tried Kasper Sky , it takes at least more than a day to complete the scan of my C partition. Regarding AVG OFFline scan is much faster, but I am not able to update its Virus database. I downloaded the update File IAVI:6397 and tried to update manually , but I get indication that some files are missing on the UPdata File. Pl. let me know , how to Update AVG OFFline scan.
My conclusion is that AVG is good for detecting Trojans and AVIRA is goog for detecting Worms
milo499
One more info , I wish to add.While scanning with Kaspersky , one should click on settings and deselect ‘ Delete infected file’. Select only ‘Disinfect ‘. Otherwise it will delete some infected OS files making the computer UN-bootable. If it is not able to dis-infect , infected files , then it is better to Load the OS a fresh after wiping off the C partition
milo499