Installing anti-virus software isn’t always enough to protect against hack attempts. Sometimes the companies themselves get hacked. As happened to Kaspersky recently. This article covers how a top anti-virus company was infiltrated by an Advanced Persistent Threat.
Kaspersky vs. Duqu
Kaspersky labs recently tested a new Advanced Persistent Threat (APT) detection suite on their internal network. It worked. An engineer spotted anomalous activity so uploaded a driver to an online virus scanner and it returned a hit from various vendors.
The infiltration was then fully analysed and the results are a little worrying, to say the least!
Kasperky Labs said that “a few dozen” systems had been hacked by the Duqu team. They used advanced techniques to move the data across the network before sending to Command & Control servers.
The hackers obtained a valid SSL certificate from Foxconn, either by remote access or inside help, to sign their own “Duqu 2.0” APT. The deployed code was far beyond the level of your average hacker, using asymmetric polymorphic encryption and authentic security certificates from one of the major hardware manufacturers. This highlights the inherent problem with certificate revocation lists.
the whole point of digital certificates becomes moot – Says Costin Raiu, director of Kaspersky’s Global Research and Analysis Team
Mostly minor differences in the code suggest a similar coding standard, for example:
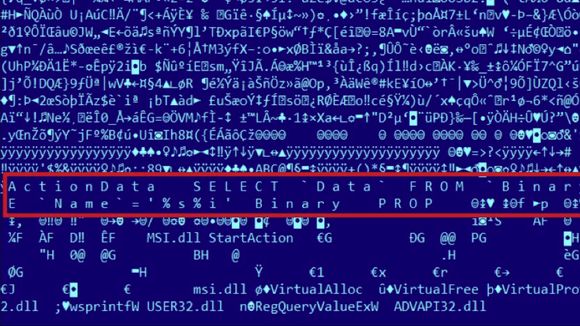
Duqu 2.0 used %05d.gif to send data over the network, compared to DSC00001.JPG for Duqu 1.0. The latest variant also used drivers as a bridge to rate limit traffic over the network, averting suspicion during data exfiltration.
The kernel level memory injection involved several files including klif.dll, CTwoPENc.dll, KMART.dll and msi.dll:
Why would I hack Kaspersky?
I considered what my motivation might be if I picked Kaspersky as a target. There are three obvious reasons I can think of to target one of the world’s leading anti-virus companies:
- Advanced notification of detection methods
- Backdoor into millions of computers, embedded devices
- Intelligence gathering
It should go without saying but, knowing exactly how Kaspersky detect code means bypassing it a lot easier. It also means the attackers probably have, or at the very least, had the possibility of backdoor access to millions of computers and embedded devices.
The last reason to infiltrate a major company, not matter the business, is to gather intelligence. The reasoning can be varied, but the outcome is always the same; information in the hands of undesirables. Hacking any big company will usually result in a massive data breach involving emails, passwords, etc.
Just Kaspersky?
Due to the attack complexity, it would be unwise to assume Kaspersky are the only company affected by this insidious team’s plan. I would expect that a variation of the code is readily available for the next target if not already in place.
The hackers have clear ties to the original Duqu attack, which envolved a completely different country, business, and method. The motives behind the attack are still not really known. High-level attacks such as this are on the increase. It is probably safe to assume we haven’t heard the last of Duqu.
Who was it?
The Duqu team became infamous for creating Stuxnet, which targeted the Iranian nuclear program. It would stand to follow that being aware of current anti-virus detection methods would be a useful thing if you’re planning on taking down a national nuclear weapons program.
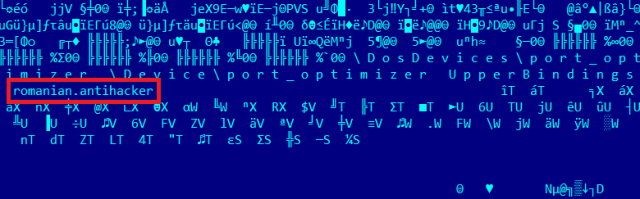
Duqu 2.0 is currently being attributed to Israel. Attribution to attacks such as this is always hard due to complete access to the network. Command & Control servers were reportedly “ugly.gorilla” with ties to China’s Comment Crew and “romanian.antihacker”, with obvious ties to Romania.
The evidence is weak and false flags are common place among nation-state hackers. Kaspersky is a Russian company, so there is a possibility of Duqu being an Israel/USA collaboration.
Am I at risk?
Kaspersky was obviously keen to update their software to detect this threat. Virus definition updates from other companies followed shortly after. There is little risk to the average user as the hackers have a propensity for penetrating high-level targets.
Most people will simply need to update their anti-virus software. If you’re a world renown hacker or into political espionage, then you are probably on a hit list somewhere, it may just be Duqu’s.


I know it’s not funny but ……… LMAO!
How in the world does a security / Antivirus company that is considered to be “one of the best” get hacked?
Well, at least I don’t run it, just in case there are trickle down effects.
Well, I can proudly say I’m using Kaspersky Internet Suite. As stated, any security company can and does get infected. Finding out, correcting the problem and informing the public is what separates the good from the bad, Mindblower!
I have not bothered with a real time anti this or anti that since MS retired XP.
Most of the bad stuff these days is ‘invited’ onto folks computers…. like optimizer pro .for example
I run adwcleaner and malwarebytes periodically but rarely find anything .
For all suspect sites or unknown downloads I use the protection of sandboxie.
As for paying for protection .not required.
Most companies have been hacked to at some point, to some degree. I guess, how they handle it is what matters.
I agree completely – it’s almost inevitable these days. The steps a company takes to mitigate the consequences should it happen and the steps a company takes when it happens make all the difference in the world. Target = how to do it wrong. Kaspersky = how to do it right.