This is the first of a three part series.
Using our credit cards online is a security risk, but one most of us deal with. Actually, credit card payment for goods on line is relatively safe from fraudulent charges because credit card companies are required by US federal law to charge you a maximum of $50 dollars US if someone made unauthorized charges on your account (country laws may prevail here, so if you live outside the US, this may be different.) And if you discover a fraudulent charge and report it to the credit card company within 24 to 48 hours of receiving the statement, most will not charge you anything at all (Generally this takes effect after you submit an affidavit to their Fraud Department that you DID NOT make the charge.)
However, that does not make you safe from Identity Theft nor does it make your account number safe from the bad guys SELLING it to other bad guys. There are a whole host of other “bad” things that can happen to you if your CC account number gets stolen; such as the hassles you may have to endure if you need to change your account number, and regular monthly charges to the “old” account don’t go through because of that (changing the account number itself is a hassle). So just because you don’t necessarily have to suffer the fraudulent charges doesn’t mean you are safe from other consequences.
While there are some alternatives to CC payment, such as PayPal, configured to link with your checking account as the mode of payment (you can use PayPal to pay by Credit Card too), not all vendors use PayPal.
 But for those vendors that have it, they will just redirect you to PayPal, and PayPal IS SSL encrypted (more on SSL in a bit). However, this article is not about transactions via PayPal. This is about Credit Card transactions handled by the site itself.
But for those vendors that have it, they will just redirect you to PayPal, and PayPal IS SSL encrypted (more on SSL in a bit). However, this article is not about transactions via PayPal. This is about Credit Card transactions handled by the site itself.
There are several things you can do to reduce the risk of your credit card account number getting stolen online. (Remember, you can only REDUCE your risk, you can’t eliminate it entirely . . . there’s no such thing as 100% security . . . so this is NOT a guarantee.)
In Part 1 here, I will deal with encryption as the mechanism for reducing risk.
Make sure your vendor uses secure encryption on the transaction page . . . indicated by an “https” in your browser’s address bar. That’s not necessarily a guarantee your account number won’t be stolen (more on that in a bit), but if the transaction page does NOT have Secure Sockets Layer (SSL) encryption, then it’s like shouting your account number to a clerk in a crowded brick and mortar store . . . everybody hears you say your account number. If the checkout page is NOT under valid SSL, DO NOT give out any personal information such as your Credit Card number.
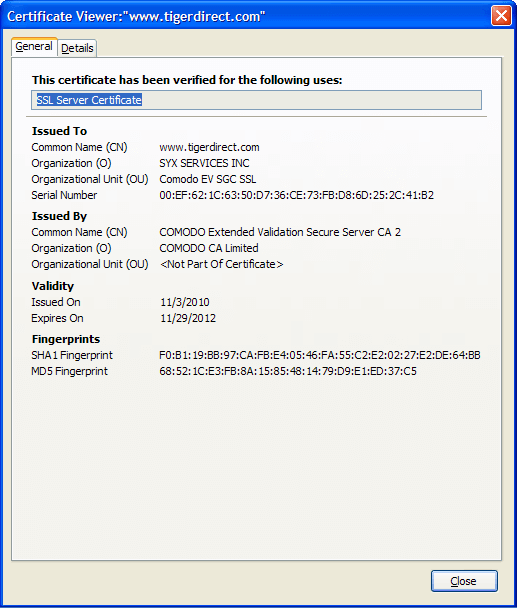
There used to be a “lock” icon down in the status bar of IE to indicate SSL encryption, but recent versions have moved that “lock” icon up to the address bar. Clicking that icon in IE will give you SSL Certificate information:
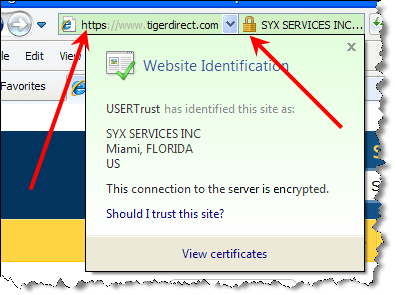
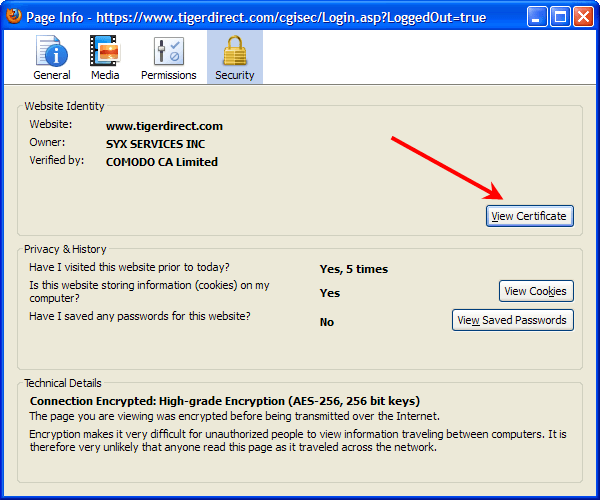
This will give you a lot of information about the certificate, most of it geek stuff . . . but for the casual user, checking the Expires On” date/time info is a good first step because some vendors allow their certificate to expire.
(The Linux version of FF 10.0.2 for viewing the certificate information is essentially the same, with the obvious appearance changes in the UI.)
If the certificate is expired, you may want to contact the vendor if it’s one you trust and want to use. Some vendors truthfully do not realize their certificate has expired, and then some are flat out scammers. (More on how scammers can acquire SSL Certificates later in the article).
If you use any other browser, make sure whatever you use is equipped to give you SSL certificate info (I know Opera, Chrome, and Safari will) . . . as far as reflecting “https” in the address bar, all have that capability (since that actually comes from the server you are connecting to).
There are various SSL certification checkers on the web . . . a good one to use is at http://www.digicert.com/help/ and there is also another good one at https://www.sslshopper.com/ssl-checker.html
“SSL” is actually the phrase for the encryption transmission protocol (originally developed by Netscape), but “SSL” and “SSL Certificate” are terms often used interchangeably with “encryption.” Not necessarily technically accurate, but many times common usage isn’t either.
There are a lot of differences between “Geekspeak” and common usage Plain English.
Now let’s see if I can wrap this all together.
The reason you want to check that the payment transaction page is SSL secure is because you don’t want anybody other than the vendor “listening in” and “hearing” what your credit card account number is.
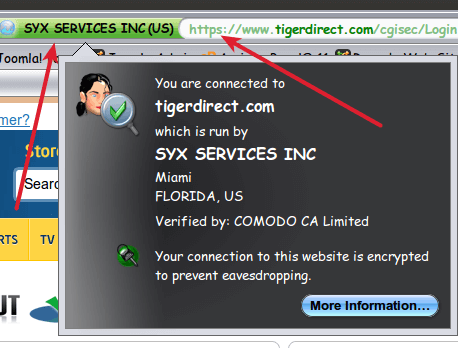
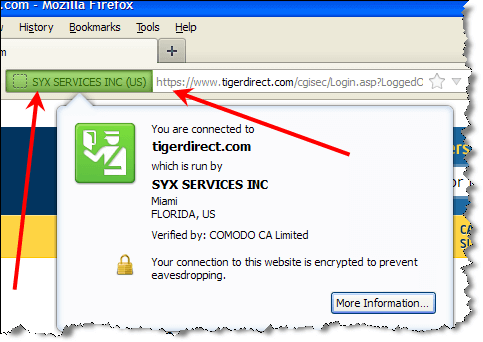
Some SSL Certificates (“EV”, “Extended Validation” certificates . . . reflected by the green color in the address bar . . . ensure encryption is used but ALSO tells you that who you think you’re doing business with IS actually who you’re doing business with. In other words, a green indication says that the vendor’s identity has been verified by the Certificate Authority. The plain vanilla SSL encryption, which only provides encryption but not site ownership verification, is indicated by blue.
Now here comes the part about scammers and “no guarantees.” 
Many of the “Certificate Authorities” (“CA” . . . entities that supposedly have gained trust throughout the industry, like VeriSign and Comodo . . . there are dozens and dozens of these, and when you add in resellers, dozens more), have been accused of selling their certificates (prices range anywhere from $5 per year to $1500 per year and maybe higher) to scammers . . . and indeed some have.
The wide range in prices reflects the turmoil in this particular industry (certificates, NOT SSL). It hasn’t settled out yet.
Now when you transmit info via SSL and you see that the company you’re doing business with has a certificate, you are assured that only that company can “hear” you (the SSL protocol is like a tunnel.)
But here’s the rub. Yeah, that company is the only one that can hear you, but what about if it’s a scam company that got hold of an SSL Certificate from an unscrupulous CA? Now you’re broadcasting your credit card number right to a scammer. Talk about the Fox guarding the Hen House . . .

First of all, it’s not THAT insecure . . . indeed an SSL is not very hackable at all. But remember I said that there is no such thing as 100% security? That’s why this is a three part series. Verifying SSL as best you can is part of the “layered security approach.” “Layered security”, which maximizes your security efforts, means you have several security mechanisms in place . . . and in this case they’re all in place to minimize your risk of CC number theft. Verifying SSL is only ONE mechanism.
You needn’t be too worried about big mainstream companies, like TigerDirect. They are generally the ones who buy an expensive SSL Certificate, mostly because they can afford it, the trust level in the CA is very high (hence the elevated price), and it’s pretty much expected that a big brand name company will be secure . . . and generally they are.
Frequently, you’ll see the CA’s logo on the site, like the VeriSign image . . . and it MUST be clickable and lead to verification . . . otherwise that’s a pretty good indication that the logo is fraudulent and if you encounter that circumstance, DON’T release your credit card number on that site. You should report the “fake” seal to the CA.
But it’s the Mom and Pop and little-known brand name boutique online stores you have to watch out for. Like if your browsing the web to buy printer cartridges at a really cheap price. Or household fixtures or some specialty item. And you’re thinking about buying from a vendor you never heard of because the prices are so good.
THOSE are the ones you want to make sure show “https” for the address of their “checkout” page and you’ll want to scrutinize their certificate.
Here’s the address bar on the checkout page for a site that takes credit card info BUT HAS NO SSL:
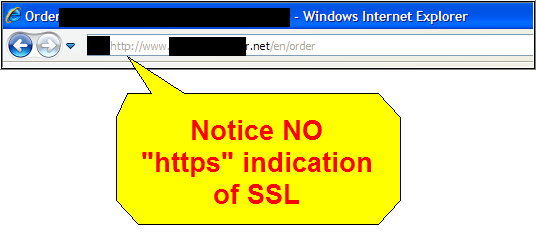
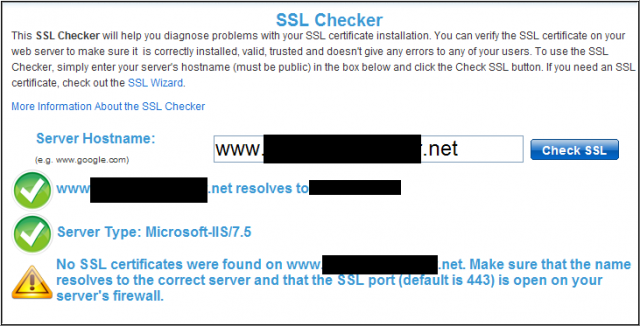 And you can always cross check on another SSL Checker:
And you can always cross check on another SSL Checker:
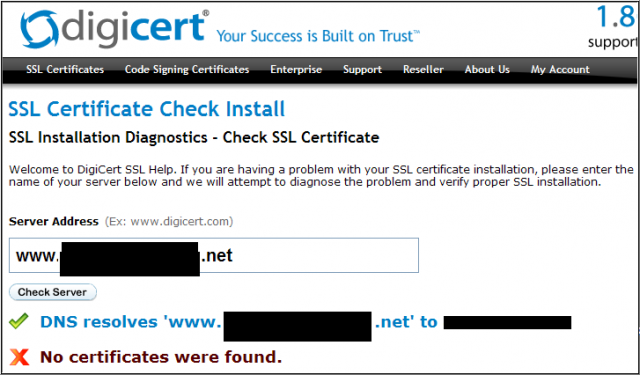 OK, we’ve beat this one to death. This site DOES NOT transmit your personal data via SSL.
OK, we’ve beat this one to death. This site DOES NOT transmit your personal data via SSL.
So what do we do? All together class: “DON’T leave a Credit Card number on this site!” (~shout~)
It’s not unusual to find a Mom and Pop or a boutique site WITHOUT any SSL at all . . . most of them can’t afford it unless they find a cheap deal . . . and a lot of those “cheap” deals come from CA’s that may not be too trustworthy.
And caveat emptor to the Mom and Pop’s who think they got a good deal. Often, the cheap cert is only good for a limited time and the CA then makes it up on an elevated renewal fee . . . the classic “bait and switch marketing scam” . . . which is why many expire because sites just cannot afford the renewal:

There is “DV-SSL” and “EV-SSL” (“DV” = “Domain Validated” . . . that’s the plain vanilla type, “EV” = “Extended Validation”) and there IS a difference between the two. “EV-SSL” is more safe . . . not the encryption, that is the same for both . . . but EV-SSL authenticates the site owner in addition to encryption, whereas “DV-SSL” does not. Just look for the green color in the address bar when you login or go to the order screen and you’ll be fine:
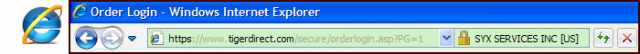
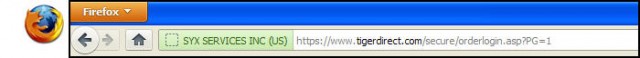
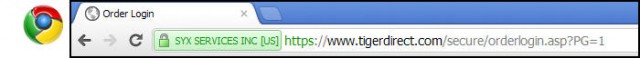
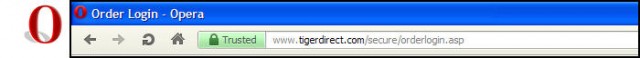
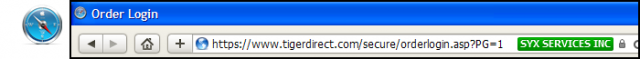 Actually, there is a third variety of SSL certificates . . . that is the “self-signed” certificate. In that event, the site owner himself/herself says that the communication between you and the site is encrypted and he/she is who they say they are. A trusted Certificate Authority does NOT verify encryption or ownership. These do NOT show up as green, but the “https” is present.
Actually, there is a third variety of SSL certificates . . . that is the “self-signed” certificate. In that event, the site owner himself/herself says that the communication between you and the site is encrypted and he/she is who they say they are. A trusted Certificate Authority does NOT verify encryption or ownership. These do NOT show up as green, but the “https” is present.
These self-signed certificates are pretty controversial, with the owner saying they’re good and “trust me”, and others (particularly CA’s for obvious reasons) raising an eyebrow. It really boils down to how much, if at all, you trust the owner (discussed at length in Part 2). At the risk of angering some “self-signers”, I would say that unless you absolutely know and trust that person COMPLETELY and really want to use that site, stick with the green indication of EV-SSL sites.
One caution I’ll repeat again later: DO NOT make this a big project. The actual time you will spend implementing all the checks I speak of in these articles is at most half an hour, likely less. If you find yourself going over half an hour, you’re spending too much time agonizing over this . . . stop and move on to the next candidate.
SSL checking, when coupled with the measures listed in Parts 2 & 3, will help reduce your overall risk to minimal.

Good article. Learned some things I didn’t know.
Great article. I am waiting for parts 2 and 3 so I can send the links to relatives and friends. Thanks.
P.S. I still won’t put my credit card (or other financial information} on-line. Too paranoid. I do know that many companies store their customers credit card information in databases that can be accessed on-line and then get hacked. They do open themselves up to law suits when that happens.
@ Steve and @ bobc4012,
Thanks for the kind words.
@ Steve,
That’s a good attitude. Learning should never stop FOR ANYONE,
@ bobc4012,
Am going to post Part 2 today and Part 3 this same time next week.
I too am reluctant to put a credit card on line, but I do now and then. As far as credit card company databases being hacked, that really has nothing to do with whether you use yours on line or not . . . those databases exist regardless.
There was a horror story in the news a while back that a “certain” credit card company had sent a hard copy of their database out with a courier in New York city. Somehow (I don’t know if the courier was in cahoots with some bad guys, but that was certainly a suspicion) the courier “lost” the database package. As I recall, it was not a database that contained ALL their account numbers, but for those holders that were on that list the CC company notified them that their account number may have been compromised, alerted them to scrutinize their statements with extra care, and offered to change the account numbers of the affected clients.
I recall that this news story got quite a bit of exposure in the security news, and that CC company suffered the black mark that you would expect.
OK, I just checked my bank’s site with FF11, IE8, and Chrome18. All show https on the login page, but only Chrome shows it, or any part of the address bar, in green. Are there settings that I need to change in FF and IE? Thanks.
@ David,
What color does FF and IE show?
Who is the CA of your bank?
As I understand what you’re asking, Chrome shows an EV-SSL and FF and IE don’t?
Assuming FF and IE show BLUE, which means they see a “DV-SSL”, the only thing I can guess is as follows:
Each browser has it’s own list of “approved SSL CA’s and shows a color based on that. That being the case, I can only speculate that your bank’s CA is only on the approved list for DV-SSL’s in FF and IE, but EV-SSL for Chrome.
Can you click on the colored field in each browser and tell me who they show as the CA?
As far as settings, I’ll look into that but off the top of my head there are SOME in the FF Advanced preferences that MAY be pertinent in this case, but it would help if I knew who your bank’s CA was and the server the CA is using.
I have a specific credit card that I use only for online purchases and keep the limit as low as possible.
@ Phylis,
Wise on your part. Clearly you have given this some thought. Compliments.