 Yes folks, yet another new Ransomware variant has reared its ugly head. This one is nicknamed ‘Locky’, so called because it encrypts all your important files and renames them with the extension [.locky]. Keep in mind too that Locky will not only scramble files on your system (C) drive, it will scramble any files in any directory on any mounted drive that it can access, including connected removable drives and/or accessible network shares.
Yes folks, yet another new Ransomware variant has reared its ugly head. This one is nicknamed ‘Locky’, so called because it encrypts all your important files and renames them with the extension [.locky]. Keep in mind too that Locky will not only scramble files on your system (C) drive, it will scramble any files in any directory on any mounted drive that it can access, including connected removable drives and/or accessible network shares.
As with most Ransomware threats, Locky requires user interaction to deliver its malware. In Locky’s case it’s in the form of a malicious email attachment. The attached document looks like gobbledegook with an associated message to “Enable macro if the data encoding is incorrect“. Of course, this is a trick, if you do enable macros you’ll download a Trojan which then downloads the final malicious payload from the crooks.
Not only does Locky scramble important files it also removes any Volume Snapshot Service (VSS) files, also known as shadow copies, that you may have made. Once Locky has completed its dirty work it hits the user up for a ransom by changing the desktop background to display the following message:
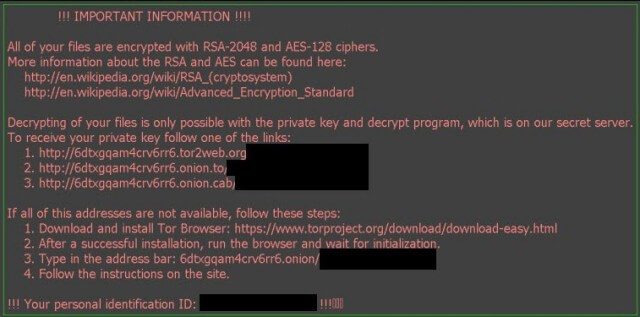
If you then visit the dark web page as per directions in the warning message, you’ll receive instructions for payment which, at the moment, varies from 0.5 BTC to 1.00 BTC (BTC being short for “bitcoin”, where one bitcoin currently equals around $400).
Ransomware is both effective and lucrative so it’s no surprise that cyber-criminals are adopting this approach in droves. There is little doubt that Ransomware currently constitutes one of the biggest threats to users everywhere, and it is very much on the increase. Of course, the best and simplest way to mitigate these types of threats is to never open suspicious attachments in the first place. Backing up regularly and maintaining an off-line backup will also stand you in good stead. And, if you are not running a good Premium antivirus solution, you might also consider installing one the security programs dedicated to protecting against Ransomware – such as WinAntiRansom Plus.

These crooks are taking things to a new level which I fear is only going to get a lot worse over time. As stated in the article, education is key to knowing not to open suspicious emails in the first place.
What I want to know though, is if my wife opened a virus on her laptop, would my PC over the network get infected too? Or are these virus’s only currently isolated to the computer they were opened on?
It depends on the type of infection but In the case of ransomware, it is definitely a risk. Locky, for example, not only scrambles files on the primary machine, it will also affect any connected removable drives as well as drives shared over a network.
Aren’t we a dumb lot.
So many “experts” on computers and operating systems and IT technology in the world?
I don’t think so.
These Ransomware folk must be laughing their heads off at our dumbness and lack of knowledge.
Lucky them!!
I am still amazed that these scams are so easy to set up and no one can fix it/eliminate it.
And there I was thinking how smart “Computer experts” are.
I certainly don’t feel so dumb now as these so called “experts” are so impotent at real problems too.
Maybe we should begin to learn about these things a bit more seriously??
Maybe pay someone to teach us? Or are we just stupid, lack knowledge, or not interested?
Colin, what has this got to do with “experts”?
The vast majority of ransomware requires some sort of user interaction in order to succeed, such as the user clicking on a malicious link embedded in an email or opening a malicious attachment. In other words, these types of infections are generally initiated by the user themselves.
As Andrew commented above: education is key.
Just like swimming pool fences maybe?
Education is the key?
No need for them if we are careful?
What a load of rubbish.
People/users are clicking on links, full stop.
Experts:
There are obviously no “experts” in this field of Ransomware or it would have been shut down. Simple as that.
Why are you so puzzled about that word,”expert” Jim?
I’m not blaming you.
I’m guessing you have no idea on how to shut these sites down either !
Just wondering how Druggie sites Porn sites, terrorist sites pirating sites etc can be demolished and yet Ransomware seems to be increasing?
Not sure how you are comparing having swimming pool fences with ransomware. Pool fences are extremely effective at preventing drowning of young children where education is futile as they are too young to understand. Pool fences are designed for a situation that doesn’t change so can be designed for. Ransomware is technology that changes all the time so relying on Anti-Virus software as the pool fence won’t necessarily work as the situation changes. In this case education is the best solution to making people aware of how they can avoid these infections. The education goes beyond just avoiding the infection but also to preparing for one by having backups made regularly that are disconected from the computer. I really can’t see how you tried to draw an analogy between 2 very different scenarios.
Hi there. Senior citizen here. Not an expert, but not a novice either. Several articles in this newsletter letter got my attention. I think my house is typical these days with it’s own network. Everything is connected to that network. Starting with the cable modem/router, desktop, 3 wireless laptops, a wireless printer, and of course 2 wifi smart phones. So security is important to me. About 2 years ago ransomware started to load on one of the laptops. I didn’t panic. I popped the battery out very fast. Next day I rebooted everything and with that specific laptop in safe mode. Scanned it and all was fine. Ransomware did not install.
The other article in the newsletter was about using a VPN. It recommended the TOR browser. In the article above Locky tells the person to download the TOR browser. So is it a good safe browser or something for the bad guys?
I’ll use my experiences as a senior to explain why the bad guys are always ahead of the good guys. It’s pretty simple. Good guys don’t think bad. With years of work experience it’s amazing the way some people steal stuff. I usually shake my head and say ‘I never would have thought of that’. Bad guys are always looking for ways to steal or get something for nothing. Good guys don’t think that way. We are hard wired that way.
Love the newsletter. Thanks.
TOR is a good safe browser, however, I’ll try to explain its involvement. These cyber-criminals operate on the dark web and when a victim needs to pay the ransom they often have to do so by accessing the dark web. Even though TOR browser is perfectly safe it does provide access to the dark web and that’s why the criminals behind Locky are saying to download TOR – just to accommodate payment of the ransom.