 We first published an article regarding the pernicious CryptoLocker ransomware and how to avoid the infection using CryptoPrevent a couple of weeks ago… you can catch up with that original article here: Block CryptoLocker Ransomware with Free *CryptoPrevent*.
We first published an article regarding the pernicious CryptoLocker ransomware and how to avoid the infection using CryptoPrevent a couple of weeks ago… you can catch up with that original article here: Block CryptoLocker Ransomware with Free *CryptoPrevent*.
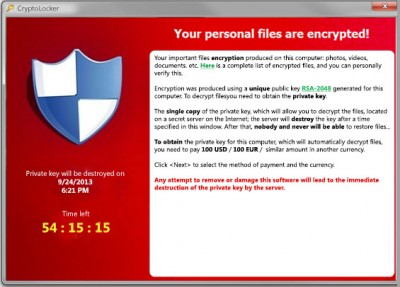
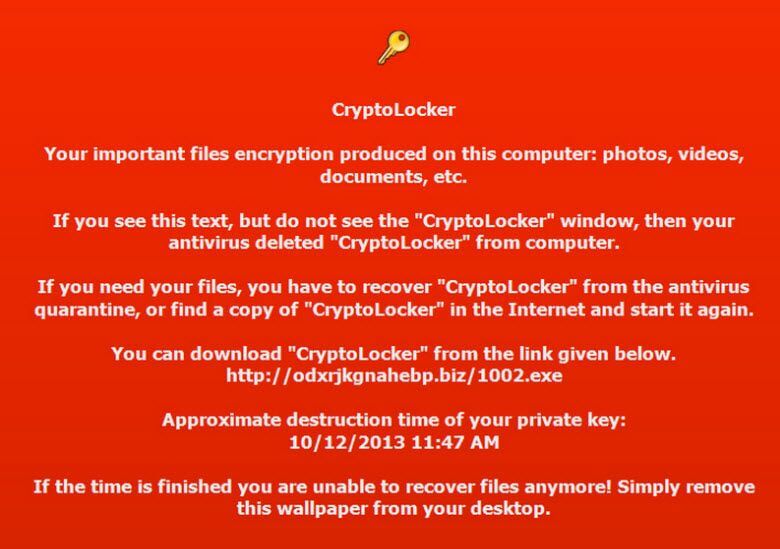
In précis; CryptoLocker introduces a particularly nasty innovation into what is essentially an old scam. This malware encrypts all the important files on a victim’s PC; video, music, pictures, documents, etc, including any files on networked or connected storage media. CryptoLocker then demands a payment within 72 hours to unlock the encrypted files and promises to deliver a key to victims who choose to pay up within the allotted time. Those who allow the 72 hours to expire without paying the ransom run the risk of permanently losing access to all encrypted files.
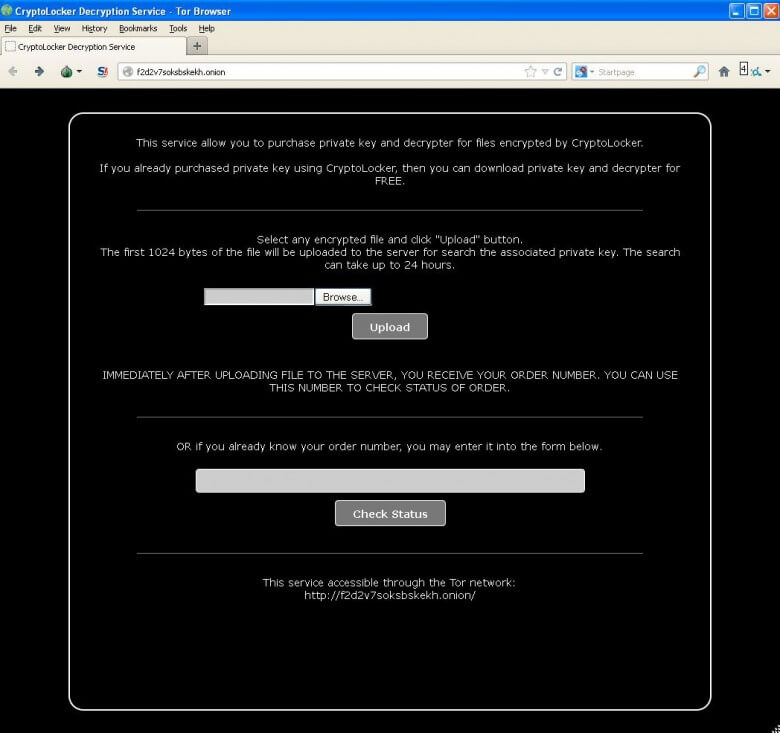
Now, it appears, the criminals behind the CryptoLocker scam have realized that the imposition of a 72 hour time limit may well be costing them money. According to Lawrence Abrams at BleepingComputer, who has been closely following CryptLocker developments for some time, many victims are willing to pay the ransom but don’t have enough time to organize payment under the systems provided. Accordingly, CyproLocker has now launched an online “CryptoLocker Decryption Service” which can be utilized to unlock files even after the time limit has expired. The rub; paying the ransom within the allotted time amounts to around $400.00, while utilizing the out-of-time decryption service increases that fee more than 5 fold, to around $2100.00
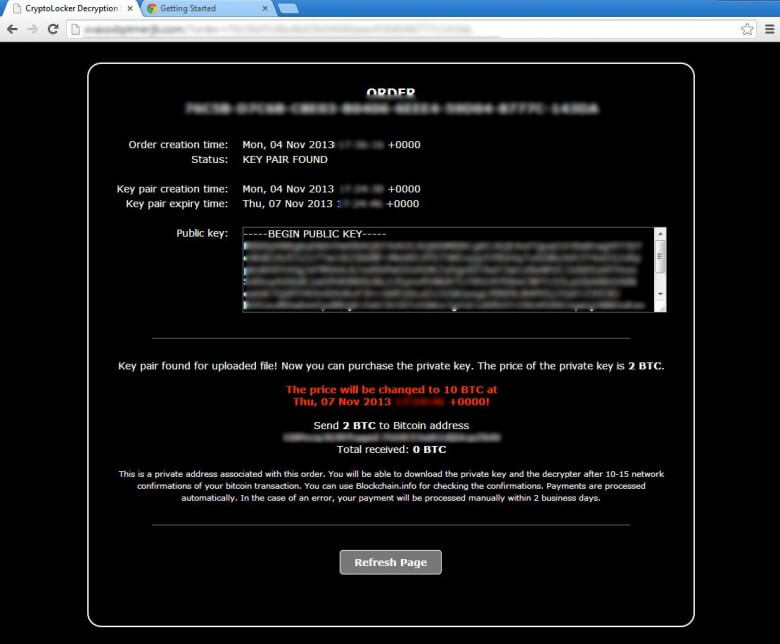
The developers behind the file encrypting ransomware called CryptoLocker launched yesterday a dedicated decryption service that allows you to purchase the decryption key for encrypted files. The price for the decryption key, though, has been significantly increased from 2 bitcoins to 10 bitcoins. With the current price of bitcoins at around $212 USD the ransom has increased from around $400 USD to over $2,100 USD.
The decryption service now still allows you to pay 2 bitcoins during your normal 3 day timer period. After that period, the price increases to 10 bitcoins:
It also seems that, although they are obviously trying to be helpful, antivirus programs can create another major obstacle for victims who wish to pay the ransom. Antivirus software tends to identify and remove the CryptoLocker infection after the event, which means affected files remain encrypted but the victim no longer has access to the payment mechanism. Newer CryptoLocker versions overcome this eventuality by including a URL where victims can download the infection again and then pay the ransom. This does appear to be a somewhat contrary solution but one which I believe desperate victims may well take advantage of.
Block CryptoLocker & Keep Up To Date with CryptoPrevent
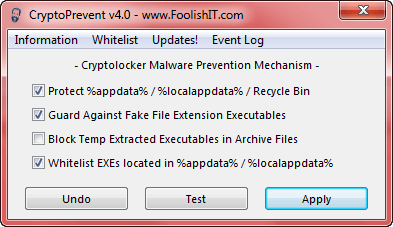
As discussed in my previous article, CryptoPrevent is a simple yet effective way to help block the CryptoLocker infection. I am happy to report that, as CryptoLocker continues to introduce new strategies, so John Shaw (CEO of Foolish IT) continues to develop and improve his free CryptoPrevent software. In fact, there have been several new/updated versions released in just this past two weeks. I suggest all those who are utilizing CryptoPrevent should keep this most useful software always up-to-date. You can download the latest version here: http://www.foolishit.com/vb6-projects/cryptoprevent/.
*For users of CryptoPrevent portable: there is no need to undo any previous protections. Simply download and run the latest version and click on the “Apply” button.
**The quotations and some of the images included in this article have been extracted from a post by Lawrence Abrams published on BleepingComputer forums. You can view Mr. Abrams’ original post in full here: CryptoLocker developers charge 10 bitcoins to use new Decryption Service
Jim,
As preached by you any many other, open NO attachment unless you know who it is from and are expecting it and stay on “safe” sites when browsing. If you wander in dangerous territory, expect danger and take precautions.
Absolutely Tom.
The other mantra that we often “preach” also applies… backup, backup, backup!! Up-to-date backups go a long way toward nullifying the effect of CryptoLocker and similar malware.
Appreciate your savvy comment,
Cheers… Jim
Thanks for the update, Jim.
Will this work only for Windows 7?
Hey Kestrel – CryptoPrevent works with Windows XP, Vista, 7, 8, and 8.1.
Cheers… Jim