In this article I would like to talk about email and show/explain some specific examples of email you may receive. Remember that once your email address lands on an email list it will be in the “wild” forever. Bad guys sell email lists to other badies who add it to their own lists and sell it to others. The cycle goes on and on…
The nastiest of the nasty
We constantly preach about the need to have a good antivirus program on your computer and one of my requirements for “good” antivirus software is that it scans your emails. Fortunately ESET, which I use and recommend, does an excellent job in this area. Below is a screenshot of a recent email captured:
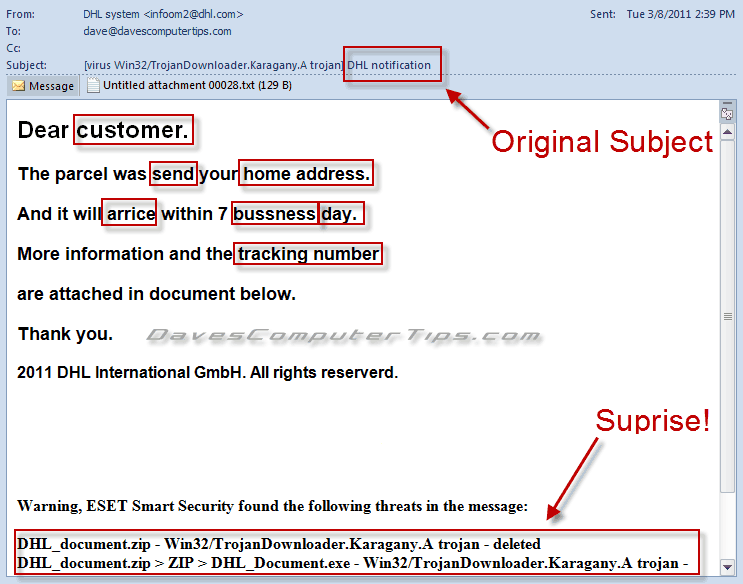
My antivirus caught the trojan and deleted it from the email and this trojan is a bad one. This particular trojan downloads other programs to your computer without your knowledge, so once your computer is infected you will most certainly be infected with many other pieces of malware! Not good, but one of the reasons you rarely ever see a computer with just one infection!
But I would have never opened the attachment. Why? The email has several “clues”, which you should learn to detect, that identify it as suspect.
- I didn’t order anything that would be shipped by DHL.
- If I did order from DHL wouldn’t they know my name, address, and the package tracking number?
- Obviously English is not the author’s native language, or spelling and punctuation were not their favorite subject in school.
- It is unlikely a business would include information as an attachment when they could display it within the email.
- No business in their right mind would send an archive (zip file) as an attachment without some prior agreement with the person meant to receive the email.
Looking for clues in your email goes a long way toward protecting yourself!
Scams
While not politically incorrect there is a specific “style” of spam called Nigeria Scams or 419 Scams because their tactic originated in Nigeria. The premise is usually to offer “something for nothing”, a sum of money to assist them in a financial transaction, or a high paying job. They are always too good to be true and often prey on your social sensibilities. If it seems too good to be true – IT IS!
Here is the text of a typical Nigeria scam spam email offering a job:
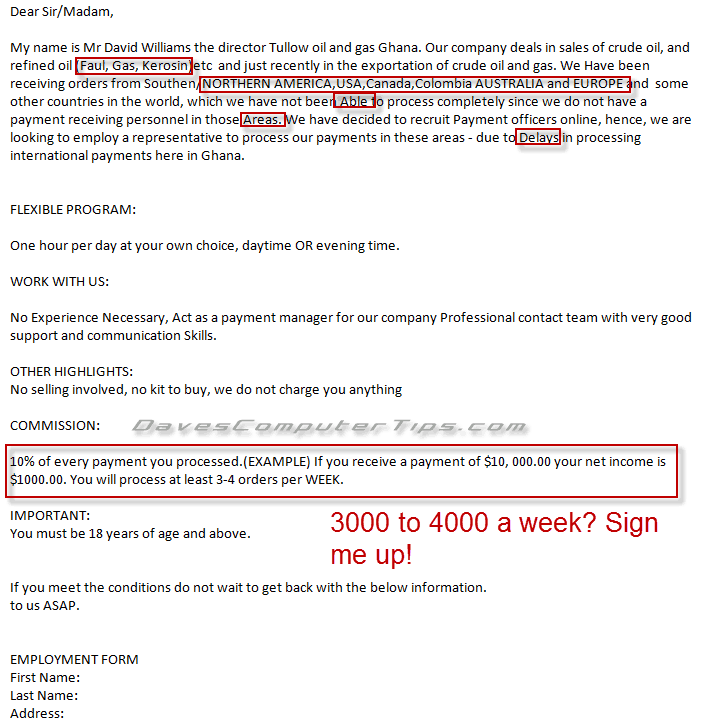
The goal of this type email is to convince you to reply with your personal information. They then attempt to open a dialog and develop a false sense of trust. In the end they send fake checks (or other forms of payment) for large sums of money and ask you to deposit them in your bank. All they ask in return is you send them a portion of the money and keep the rest for yourself. Sounds too good to be true (it is). You send the money and days later are notified by your bank that the deposit is fake and you are left holding the bag.
Fortunately these type emails have “clues” also!
- How did they get your email address?
- Are they offering large sums of money for what seems like a menial task?
- Does it sound too good to be true?
- Poor spelling and capitalization.
Here are two additional examples and I’ll let you make your own decision about their true intent:
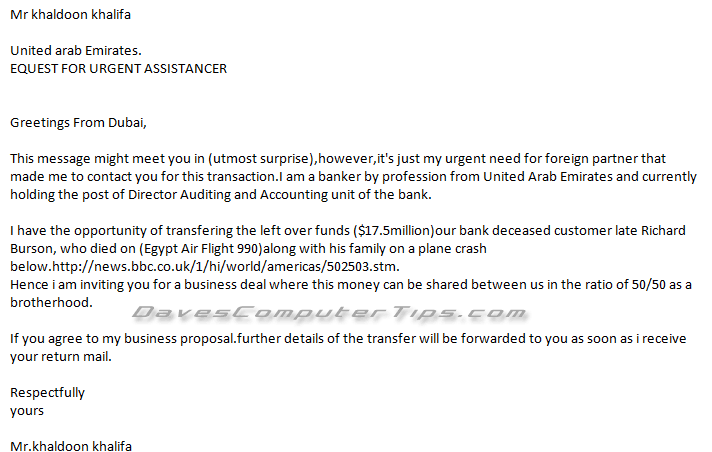
Interesting. I don’t know anyone from the Middle East.
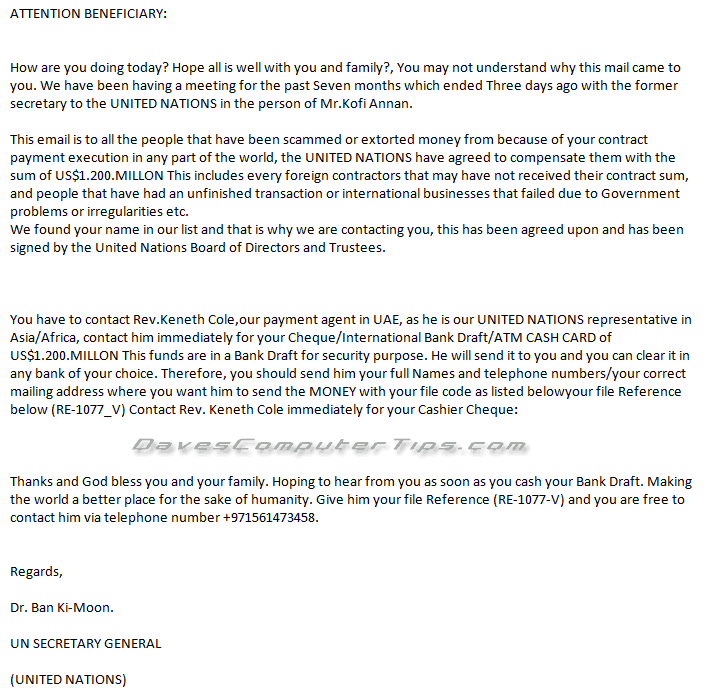
I’m more important than I thought. After all I receive email from the UN Secretary General!
Just plain SPAM
The third category covers quite a bit of territory. There is no method to the madness, but they all have one goal – for you to click a link. Unfortunately you have no way of knowing what is on the other end of the link. Virus? Pharmaceutical drugs with dangerous contents? Malware? Porn? You don’t know and you don’t want to find out! If you click the link you are only going to regret it in one form or another. Maybe you will get a virus. Maybe you won’t. What you will do is validate your address – they track the link, know your address is good, and your address becomes more valuable at resale time so you get more spam.
Here are some examples of common spam:
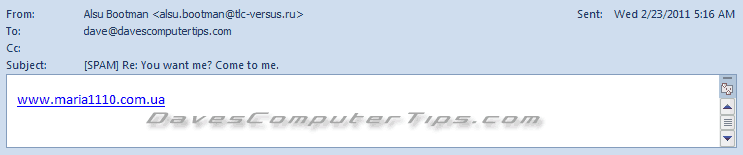
Only a link? I don’t think so! Another “clue” in this email is the use of RE: (for reply) in the subject line. They reason you will be more likely to open the email if you see that and believe you are opening a reply to an email you previously sent.

I don’t care how low my self confidence is, I’m not clicking that link!

Not where I would want to get my medicine from! Also note the use of RE: again.
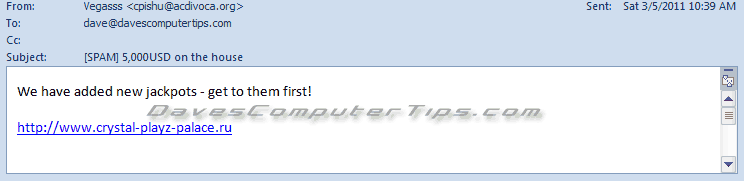
$5,000? Yeah, right.
Do we see a pattern here? You bet. Interestingly enough the spammers often cycle the exact same emails.
Phishing
Phishing is the act of attempting to gain your personal information through unauthorized means. Usually this is through a carefully crafted website designed to look, or impersonate, a legitimate one. Email is often used to draw the user to the offending site using language of an immediate or emergency sounding nature.
Here are two that I’ve recently received:
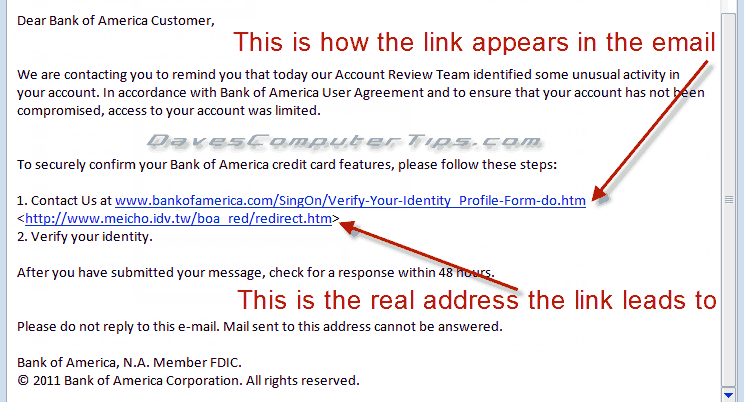
They expect you to click the link and be carted away to the actual URL address hidden in the link where you will enter your banking information on a site that looks like your bank, but isn’t. Boom! They have access to your bank account.
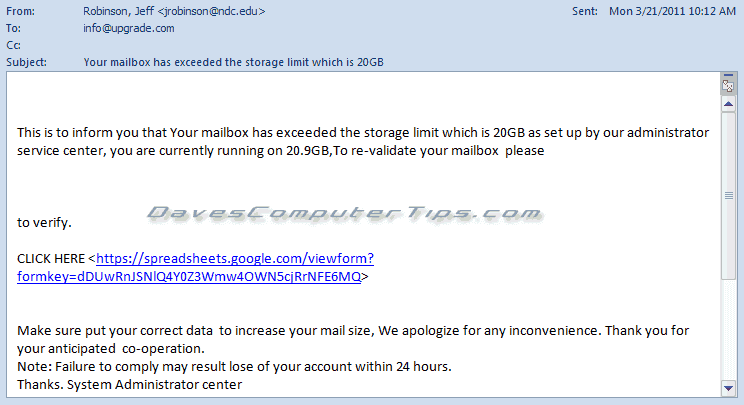
Punctuation anyone? Poor English? Why isn’t my email address listed in the email? If you look closely at the URL in the email you’ll notice they aren’t even trying to be clever and are using Google Docs allowing you to enter your email address and password directly into their spreadsheet – Nothing worse than a lazy criminal! Why do they want access to your email account? Spam! They can then send spam using your email account and in some cases have access to your address book. Won’t your friends and business contacts love you!
What can I do
Hopefully you’ve picked up on the fact that this type of email generally contains clues to the true reason for the email. Actually, I know you have because you are super smart and read DCT! (big grin) Here is a quick refresher:
- Observe the sender. Do you know them? If not why would they contact you?
- Observe the subject. If you don’t recognize the sender then does the subject raise any red flags?
- Observe the content. Is the email written in a generic format?
- Observe the content. Is it an offer that is “too good to be true”?
- Observe the content. Does the email express a sense of urgency or an emergency?
- Observe the content. Is the language used incorrectly?
- Observe the content. Is spelling, capitalization, or punctuation incorrect?
These simple checks can save you many headaches, but what do you do after you identify an email as suspect?
- Never click on a link in a suspect email! If you receive an email with a link that raises suspicion you should always go to your browser and type the address in yourself.
- Never open an attachment in a suspect email! If you aren’t sure don’t open it. Not only can zip files contain bad things, but many other types of files can be compromised. Extensions can also be hidden so the file appears harmless.
- Never reply to a suspect email. When you reply you verify that your address is valid and things go downhill from there.
Remember, use common sense when dealing with email. Don’t share your personal information or passwords. Use a quality antivirus.
Thanks Dave for this important reminder. I want these helpful tips to be cemented in my brain to avoid any of the negative results you mentioned. So far I have been able to get by without a problem by being vigilant in these matters.
Regards