Microsoft surprised (shocked?) a lot of people when announcing the requirements for Windows 11, not the least of which was the requirement for TPM (Trusted Platform Module). TPM is an obscure security protocol (at least it was until Windows 11) that has been the cause of much confusion. Even in PCs that have supported TPM it has always been disabled by default in BIOS, which tells you exactly how much importance manufacturers placed on it.
I, for one, could not see the logic behind TPM’s introduction as a mandatory requirement and have theorized for some time that it must have been part of an attempt to boost new PC sales. However, I have been researching this previously little known security protocol and it seems that Microsoft’s decision might well be more about DRM (Digital Rights Management) and control than security.
Trusted Computing or Treacherous Computing?
TPM is an integral part of the “Trusted Computing” initiative which has come under fire from many respected critics. One of the most eye-opening dissertations I’ve read was published by well-known free software activist and programmer Richard Stallman, a man with a long list of achievements, a brilliant mind, and a history steeped in technology. His dissertation is scathingly critical of “Trusted Computing” referring to it throughout as “Treacherous Computing“. Here is an excerpt:
The technical idea underlying treacherous computing is that the computer includes a digital encryption and signature device, and the keys are kept secret from you. Proprietary programs will use this device to control which other programs you can run, which documents or data you can access, and what programs you can pass them to.
Of course, Hollywood and the record companies plan to use treacherous computing for Digital Restrictions Management (DRM), so that downloaded videos and music can be played only on one specified computer. Sharing will be entirely impossible, at least using the authorized files that you would get from those companies ~ source
And Mr. Stallman is certainly not alone in his criticisms. This from Wikipedia:
Some security experts, such as Alan Cox and Bruce Schneier, have spoken out against Trusted Computing, believing it will provide computer manufacturers and software authors with increased control to impose restrictions on what users are able to do with their computers.
There is concern amongst critics that it will not always be possible to examine the hardware components on which Trusted Computing relies, the Trusted Platform Module, which is the ultimate hardware system where the core ‘root’ of trust in the platform has to reside. If not implemented correctly, it presents a security risk to overall platform integrity and protected data ~ source
Much of what I’ve read and quoted here is quite dated. However, the question must be asked- are these early concerns regarding Trusted Computing and, by association, TPM, now coming to fruition?
As I mentioned earlier, the introduction of TPM as a mandatory requirement has always baffled me. However, as a result of my recent research, I’ve canned my initial theory that TPM was introduced by Microsoft simply to boost the sale of new PCs and am now of the opinion it has come about as the result of pressure from powerful digital rights advocates, such as major media organizations and software venders.
NOTE: I must emphasize that there is currently no evidence to suggest TPM will be used for sinister purposes and the opinions expressed herein are theories based solely on its “potential” for abuse. Still, as far as “trust” is concerned, I would not trust the money-grubbing media organizations one iota.
Something to Ponder
What follows is a true story. One of the many devices I’ve always owned is a combination DVD player/HDD recorder with twin tuners. Early on these devices came with multiple input jacks to allow recording from external devices such as a camcorder, VCR, etc.
Some years back, when my current DVD/HDD recording device broke, I went into a major electronic store to buy a replacement only to find, much to my dismay, that the new models did not include any input jacks at all. When I queried the salesman about this he informed that it had come about as a result of pressure on manufacturers from the media organizations. A prime example of the massive influence exerted by these money-grubbing moguls.
—


And now every time I do a W10 update, I am reminded that my PC does not meet W11
requirements, and it never will, short of a complete PC rebuild.
Jim,
I’m one who has been using TPM enabled computers, mainly laptops, since Windows 7. When I found out about Bitlocker, I switched to the Pro version of Windows and starting using it. Bitlocker can be used without a TPM module, but requires either a key stored on a USB flashdrive or a password to unlock the drive. When it came time to replace the initial laptop, I looked for one that had a TPM module, which allowed the use of Bitlocker without having to enter a password or inserting a key when signing into Windows. I’ve continued the practice through Windows 8, 8.1, 10 and 11.
Before I retired, my job kept me on the road 26 days out of 30. Setting up the laptops I used to require a BIOS password, as well as using Bitlocker, meant that the laptop was essentially a paper weight if it got stolen.
The PC my wife is using and the one that it replaced, both Dells, were equipped with TPMs, and Bitlocker is used on it as well.
Based on what I’ve been reading elsewhere, the TPM requirement is a security issue. In the future, software will be required to have a digital signature or something like that to be able to run in Windows, making it harder to introduce malware.
As for DRM, up until about 3 years ago, I’d been using WinX MediaTrans to convert videos to .mp4. Then Apple changed the codex or something and it no longer works.
I’ve got to check, but I heard there was a lawsuit filed against Apple over DRM filed in Federal Court here in the U.S. over limiting how videos purchased could be played, i.e., having to use iTunes or Apple Music exclusively. I don’t know the current status.
Hey Mark,
Yes, that’s the spin, that TPM makes it more difficult to introduce malware. However, TPM can also be used (abused?) to force users to run media files from a specific software and prevent users from sharing.
Just look at all the adds for new computers on Microsoft websites involving Windows 11 – everything is geared towards getting you to buy a new PC with Windows 11 pre-installed. TPM is a total scam to make perfectly good computers artificially obsolete.
I do not disagree Walter.
It would be helpful to the reader to know why you disagree. We non tech guys depend on you technically aware people to keep us in the loop.
If you are referring to my comment John, I believe you must have misread. I said “I do NOT disagree”. In other words, I DO agree.
Jim,
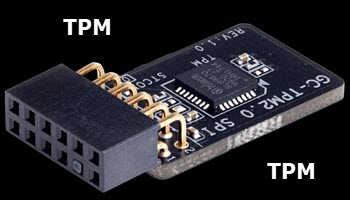
At the head of your article on TPM there is a “picture” of what could be taken as an “add on module”. Is the picture an artist conception of a TPM add on module, or is there such a module available? My ASUS mother board, as fas as I can tell does not have TPM. so an add on would solve WIN 11 compatability and a perfectly good motherboard from the trash heap.
Sherman
I have the same issue with my Asus P8Z77-V LX socket 1155 mobo. I do believe
the bios would also have to support TPM, and since my mobo is only a socket
1155, it will not support the ninth generation cpu, that is also a W11 requirement.
Hey Sherman,
The image at the top of the article is a TPM module. The motherboard MUST include a TPM header, which houses the module. So, if the motherboard includes a TPM header then purchasing a TPM module is an option. If the motherboard does not include a TPM header, then the module would be useless.
Hope that clarifies.
Scary times Jim.
We should not just be “accepting” this from Microsoft and blindly believe what they tell us. They are clearly trying to force everyone to embrace TPM over the next few years as we are eventually compelled to upgrade to a system that will have these chips built in. When you are forced to do something without any choice in the matter then it is time to start digging in and asking questions.
Who knows what little backdoors this could potentially open onto your PC so that they could scan your PC for any particular information they might be seeking ? They tell us is just to prevent Malware getting in but who knows what else these little beauties are capable of ? Does anyone but Microsoft know exactly what these chips do ? This smacks of the equivalent of a computer “vaccine mandate” to me.
Given the state of US politics at the moment and the fact that Microsoft has become a very “woke” organisation in recent times I wouldn’t be at all surprised we find that it could be used in future by Intelligence Agencies to access computers of anyone they deem a threat or for example, to search for copyright infringements. I wonder if anyone has anyone be able to do a full technical analysis of what these chips actually do, whether they can “phone home” and/or allow access remotely to the PC at BIOS level ? Is anyone capable of doing such an analysis or is the chip totally encrypted to all except Microsoft ?
George Orwell might have been a few years off but his essential warning was correct. 1984 is pretty well here now and my tinfoil hat is firmly on because we are finding more and more that they really are necessary and not just the headgear of choice confined to “kooks” only any longer.
Hey Reg,
I’ve tried to find out more about TPM but am unable to locate any in-depth assessments, only basic descriptions of its security features. Still, when the likes of Richard Stallman and Bruce Schneier are warning about TPM and its potential for abuse, one has to sit up and take notice.
The anecdote above reminds me of an Amstrad VCR I bought many years ago It took two tapes at once and would copy from one to the other.
I bought it because it was actually cheaper than the single tape model.
A friend of mine was a quartermaster sergeant at the time and had some educational tapes (basic physics if my memory serves) that the regiment needed copies of.
Great we thought. A use for the copy function and the ‘copy from rented’ enhancement switch.
I am sure many have realised what happened. When I put the switch on the message was ‘corrupted tape cannot be copied’. With the switch off the copies were perfect.
That was around thirty years ago and Amstrad has been gone for many years.
I use VLC for audio and video but every so often after an update Microsoft attempts to make me use their player.
DRM by the back door and a new stream of income for the copyright holders. It’s been a few years since there have been any front page prosecutions for copyright theft, there could be a lot more in the next few years.
With books the split on sale price used to be one third for the author, one third for the retailer and one third for the publisher. Large companies have been enlarging their percentage for many years and on top of that downloading has a tiny cost compared with producing a book.
My thoughts run on the lines of will this prevent illegal use or will it be a system to report illegal use.
Unfortunately, it seems about control. Why else would MS offer a [another] “free upgrade?” This is why many people would rather bang their head finding drivers and software for Linux – because they can set it up as they like. Now that WIN11 is going to be contingent on a certain processor architecture is asinine.
I was just fine on Windows NT, until forced to 2000. It wasn’t too bad, I’ll admit. Thankfully I skipped Vista – which was the same kind of hype. Got to WIN7 and was stoked. I watched as people flailed with WIN8 – same kind of hype again, big fumble. Somebody throttled someone and ironed it out to WIN10. Decent.
To expect people, businesses, and schools to update hardware just to run a mediocre update because their hardware “Isn’t [healthy] enough” and you should “consider buying a new [chip compatible] machine” is ridiculous. I teach CS at a small school where dropping $25k because the machines in the lab don’t have hardware based DRM… is, is B.S. Even my Admin laptop, a two year-old Lenovo P51, with 16GB RAM, dedicated 4GB NVidia card, Intel Core i7-7700HQ CPU @ 2.80GHz, that can smoke Autodesk Inventor, Revit and Maya cannot be updated because of no DRM hardware??? I’ve got a torch, somebody get a rope… the greed it disgusting.
As has been mentioned here already. This whole closed-source “trusted computing” initiative is about control, restriction and hidden access to people’s computers.
TPM is for the DRM part and to control which software is allowed to run on a machine. Of course, that control will not only block malware, but any software that the powerful corporations don’t want users to run.
Other technologies, like Intel’s management engine, active management techology (and the respective AMD equivalents) are not only full of security holes, but would in general leave computers potentially open to remote access and remote control.
All of this junk is sold to the public as “better security”, and naturally only for our own benefit, right?
Unfortunately, despite many good ideas and great effort, the open source community hasn’t been able to come up with hardware and desktop software that would appeal to a broad range of end users and rival the commercial counterparts in polish, functionality, and industry support. This is largely due to the huge proliferation in the FOSS community concerning the desktop, Focus is on the server, mostly because there is commercial interest behind it, and commercial companies are funding professsional developers to advance e. g. the Linux kernel and related server software.
We’re in a tight spot here considering the recent developments, particularly those who need commercial software for work, or are not tech savvy enough to make a Linux desktop work for them.