 E-mail Encryption for Private People
E-mail Encryption for Private People
Millions of people every day send messages to friends, colleagues, and business contacts, written on postcards. Electronic postcards, but still readable by anyone who cares to pick them up. Would you send a letter without an envelope? Every time you send an ordinary e-mail, that’s what you’re doing. What you need is encryption.
Difficult? Complicated? Well, not really, although e-mail client software like Outlook and Windows Mail hasn’t gone to any trouble to make it easier. They’ve hidden the set-up two or three layers down in the menu structure, for a start. Try to find any help on getting started, and you’ll find yourself giving up pretty quickly unless you’re determined. That’s where I hope this article will help.
If you are a journalist who needs to protect his or her sources, you really need to be doing this right now, as a matter of routine . If you are a dissident in a repressive country, you already know that you could go to jail if your messages are read, and more and more governments are buying the technology to make that possible. If you are politically active, know that you are probably on the radar of law enforcement, and you need to take avoiding action.
The journalist Glenn Greenwald nearly missed the Edward Snowden scoop because he initially found it too much effort to learn how to communicate with Snowden securely. Once Laura Poitras had started encrypted communications with Snowden, Greenwald learnt fast. And, as Snowden later pointed out, if Greenwald can do it anyone can. It’s worth the effort, but you do need to pay attention!
Email Encryption & Ciphers – Some Background First
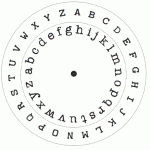 How does it work? You may have played around with simple codes, or more properly, “ciphers”, as a child, to send secret written messages. For instance, you could jumble the order of the 26 letters of the alphabet, write the scrambled letters in a row underneath the original alphabet, and use the two rows as a table to translate the original letters of your message into new ones. DCT ROCKS might become AGB HYGPU, for example. Then you send the scrambled message to your friend, who has a copy of the jumbled arrangement, and she uses the bottom row to translate the jumbled letters back to give the original words. The particular scrambled alphabet is the key to this symmetric cipher – so called because you use the same key to encode and decode the message (strictly – encipher and decipher).
How does it work? You may have played around with simple codes, or more properly, “ciphers”, as a child, to send secret written messages. For instance, you could jumble the order of the 26 letters of the alphabet, write the scrambled letters in a row underneath the original alphabet, and use the two rows as a table to translate the original letters of your message into new ones. DCT ROCKS might become AGB HYGPU, for example. Then you send the scrambled message to your friend, who has a copy of the jumbled arrangement, and she uses the bottom row to translate the jumbled letters back to give the original words. The particular scrambled alphabet is the key to this symmetric cipher – so called because you use the same key to encode and decode the message (strictly – encipher and decipher).
Unfortunately, this cipher is really easy for someone else without the key to break, partly because some letters in words occur on average more frequently than others. E is the most common letter used in the English language, so if you see a lot of Ys in the enciphered message, it’s a fair bet that Y in the code means E in the message. Without too much effort, someone else can work out what your message says.
Enter the computer, which can translate the message letters into bits (ones and zeroes) and scramble those instead, very quickly. Smart mathematicians have invented ways of scrambling the bits representing characters, given an initial key or password, which make it almost impossible to unscramble them again to get the original message without knowing the key. The Advanced Encryption Standard (AES), which is approved to government Top Secret level, produces enciphered messages which would take centuries to decipher without the key.
But you still encipher and decipher the message with the same key (symmetric cipher), and somehow you have to get that key to your recipient safely, without the enemy getting hold of it. You also need to change the key frequently, perhaps daily if the messages are really important. Until quite recently, government messengers would travel the world with briefcases full of cipher keys chained to their wrists, to get the keys securely to a country’s diplomatic and military outposts.

Here’s the critical bit. In 1976 all this changed, when two incredibly smart mathematicians, Whitfield Diffie and Martin Hellman, realized that they had found a way of exchanging enciphered messages using two keys. You use one key to encipher the message and the other to decipher it. Amazingly, the key that enciphers the message cannot be used to decipher the message again. Only the other key of the pair will do the deciphering.
If you think about this for a minute, it’s almost unbelievable. Everyone was so used to symmetric ciphers that the idea of a method which could encipher a message with one key so that only a different key could decipher it again was just weird. But three mathematicians, Rivest, Shamir, and Adleman, developed the idea into a cipher scheme known by their initials – RSA –which we all use today whether we know it or not, to establish secure connections on the internet when shopping, banking – or sending secure e-mail. This is asymmetric encryption.
The important part here is that we no longer need to distribute keys securely around the world before we can send encrypted messages. In fact we can actually publish one of the keys so that people can use it to encrypt their messages to us. For this reason, the published key is called the public key. Once encrypted, the message cannot be decrypted by anyone else, even if they have the public key. Only you, with the other key, can decrypt the message. Hence the second key is known as the private key (or secret key).
You can send people your public key, in an unencrypted e-mail, or publish it on a public website – it doesn’t matter; once a message is encrypted with the public key, only you can decipher it.
Email Encryption – Clients and Certificates
 So what do we need to be able to do this? First, an e-mail program which can do the job. You may be surprised to learn that most common e-mail clients can handle encryption, but it’s usually well-hidden in the security options. Then we need a key-pair, which has to be generated using a special algorithm. The key-pair makes up your security certificate. There are two types of security certificate in common use. One is called a PKI (Public Key Infrastructure) or S/MIME (Secure Multipurpose Internet Mail Extensions) certificate. The other is the PGP (Pretty Good Privacy) certificate, and unfortunately the two are not compatible. There are advantages to each. Out of the box, Microsoft Outlook and Windows Mail will handle S/MIME, which is used in business communications, so let’s get going using Mail.
So what do we need to be able to do this? First, an e-mail program which can do the job. You may be surprised to learn that most common e-mail clients can handle encryption, but it’s usually well-hidden in the security options. Then we need a key-pair, which has to be generated using a special algorithm. The key-pair makes up your security certificate. There are two types of security certificate in common use. One is called a PKI (Public Key Infrastructure) or S/MIME (Secure Multipurpose Internet Mail Extensions) certificate. The other is the PGP (Pretty Good Privacy) certificate, and unfortunately the two are not compatible. There are advantages to each. Out of the box, Microsoft Outlook and Windows Mail will handle S/MIME, which is used in business communications, so let’s get going using Mail.
Next you need an S/MIME certificate, which has to be generated by an official certification authority. It will be associated with one particular e-mail address, and will only work with that one. The authority will only issue one valid certificate at a time per e-mail address. Normally you have to pay to be issued with a certificate for business use, but the Comodo company generously issues free certificates for personal e-mail. Let’s go and get one.
Navigate to http://www.comodo.com/home/email-security/free-email-certificate.php. Which browser you use here matters, because the certificate is given to you via the browser’s internal security mechanism – the browser handles certificates all the time, when talking to HTTPS (https://) sites. Let’s use Internet Explorer, since that is Windows Live Mail–friendly. Firefox does things slightly differently.
Select the button to sign up for a certificate. IE will give you a warning that “This Web site is attempting to perform a digital certificate operation on your behalf”. Let it, and enter your details carefully. The process will check that you really own the e-mail address. Set a Revocation Password, and note it down somewhere; you will need it if your certificate ever gets stolen, so that you can revoke or cancel it. Accept the subscriber agreement and press Next. You may get another warning; press Yes. The system will check whether a current certificate has already been issued for that e-mail address, and stop you at this point if it has . All being well, you will now see “Application is successful!”. Go to your e-mail client and open the e-mail from Comodo. Follow the method given by Comodo. Use the same browser throughout; Comodo is very secure and will refuse to give you the certificate if you try to use a different browser to collect it.
Click through any browser warnings, and you should see “Attempting to collect and install your Free Certificate… Successful”. OK, so where is it? IE has put it in the Windows Certificate Store. At this point you MUST back it up, in case your computer ever collapses in a heap. If you lose a certificate you also lose the ability to read any messages encrypted with that certificate – unless you’ve kept plain-text copies, which would not be wise.
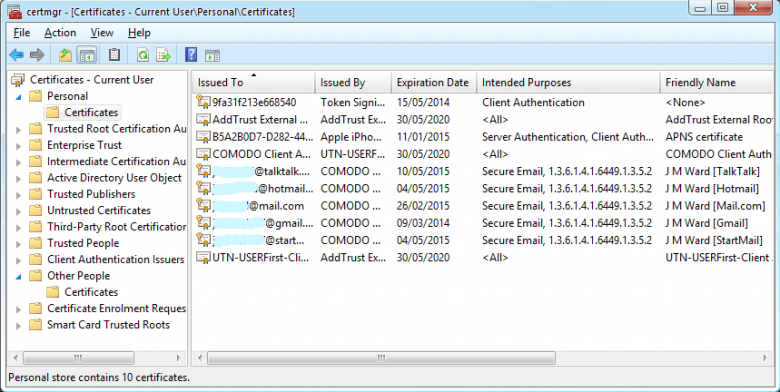
OK, so how do we back it up? Again, Microsoft carefully hides the means of doing so. We want the Certificate Manager, but if you can find it in Administrative Tools or Computer Management, you’re doing better than me. The best way to find it is to type “certmgr.msc” in your search box. When it comes up, right-click it to send a shortcut to the desktop, which you can then put somewhere appropriate or pin to the taskbar. In the Certificate Manager, click on Certificates – Current User | Personal | Certificates, and you should see it listed there under the appropriate e-mail address. Double-click it, select Details | Edit Properties, and give it a reasonable Friendly Name, like “Fred Bloggs [Hotmail]”. Click OK until you get back to the Certificate Manager, then select Action | All Tasks | Export… This brings up the Certificate Export Wizard. Click Next, and elect to export the private key along with the public one. Click Next, and note that the export file format will be Filename.pfx. Check the boxes to export the private key along with the public one, and also to export the extended certificate properties, but do not check the box that specifies the deletion of the private key! Click Next again. Check the Password box, and enter a good strong password – and note down what it is. There is no way of recovering it. Finally, browse to a suitable folder, perhaps in Documents, give the file a name, and save it. Click Next again, confirm that the settings are what you expect, and click Finish. Throughout this process you may be asked to allow crypto-secure actions; if so, just agree to do so. Copy the file somewhere safe, in case your computer drive fails or gets wiped. Phew! Safe at last!
If you wish to use Firefox, the procedure is much the same except that Firefox will download the certificate into its own store. You will have to select Tools | Options, then the Certificates tab, then View Certificates. Then look under the Your Certificates tab, where you should see a Comodo certificate registered. Select it, then select Backup… You will find that it backs up as a .p12 file, but this file format is interchangeable with the .pfx format. Once you have backed it up, you will need to go to the Certificate Manager and select the Personal store, then Action | All Tasks | Import… in order to register the certificate in the Windows store. All this is tedious, which is why it is best to do the whole job through Internet Explorer.
Now you have a valid e-mail certificate (public key plus private key) registered on your system.
Email Encryption – Windows Mail Setup
 Now to set up your mail client. This is a little tricky, but once it’s done, sending and receiving encrypted messages is really easy.
Now to set up your mail client. This is a little tricky, but once it’s done, sending and receiving encrypted messages is really easy.
Initially, Windows Mail will not know which of the certificates that you may have installed to use for your e-mail account. However, Mail knows where the certificate store is, so it allows you to select a default certificate for this account. To do this, select the top left (blue) tab on the Mail ribbon, then Options | Email accounts… |. Select your account, then Properties, then select the Security tab. You will see boxes for the Signing certificate and the Encrypting certificate. We are going to use the same certificate for both. Press the upper Select button, and Mail will present you with the relevant certificate that it finds in the Certificate Store. Press OK. Repeat with the lower Select button. Note that the default encryption algorithm is 3DES (triple-Data-Encryption-Standard). I’ll come back to this later. Press OK and Close. The setup is now done.
Now you need your correspondent to set up a certificate on their computer in the same way. It is possible to test the procedure out on one computer (I am checking it by using Windows Mail in a VirtualBox Windows 7 virtual machine, and sending messages between two of my e-mail accounts). But it’s much less confusing, and more useful, to test it out between you and a family member or friend. Once they have done the same thing, you are ready to go.
Email Encryption – Initiating Contact, Sending & Receiving Messages
 First you need to send your correspondent a digitally-signed message. This will automatically give them a copy of your public certificate. Of course you won’t be able to encrypt this first message, since you don’t have their public certificate. You also need to have your correspondent registered as a Contact in your Contacts folder; their public certificate will eventually be stored as part of the Contact details. If you haven’t done this already, you can do it from the message they send back.
First you need to send your correspondent a digitally-signed message. This will automatically give them a copy of your public certificate. Of course you won’t be able to encrypt this first message, since you don’t have their public certificate. You also need to have your correspondent registered as a Contact in your Contacts folder; their public certificate will eventually be stored as part of the Contact details. If you haven’t done this already, you can do it from the message they send back.
Open a new Email message form and write a message. Press “To…” to select your correspondent from the Contacts. Now select the Options tab, and press “Digitally sign”. (You can try selecting Encrypt as well if you want, but Mail will complain when you try to send the message). Send the message, confirming any security prompts that pop up.
Now your correspondent has your message and your public certificate. They will be presented with a message “front page” telling them that the message has been digitally signed. On pressing Continue, they will be able to read the message. At this point, if they have not already made you a Contact, they should do so. Then, if they examine your contact details, under Edit Contact | IDs, they should see your Digital ID (public certificate) with a big green tick against it, listed under your e-mail address. (It may be necessary to open the received e-mail fully, click to dismiss the warning page, then close the e-mail again in order to register the certificate ID with the contact).
That’s the first stage done. Now you are almost set up. Your correspondent can now send you an encrypted message which should also be signed, so they should select both the Encrypt and Sign buttons when composing their message. That way, you get their public certificate in return.
When you receive it, open the message. You will get the warning first page; press Continue, and you should see the decrypted signed message. You may get a security prompt now and then, but all you have to do is OK it. Clicking on the seal and padlock icons will show you the signing and encryption certificate details (the same, in this case). You should check the contact details for your correspondent, as above, to ensure that their public certificate has been registered. If not, you may have to create a new Contact for them from the e-mail they sent (right-click on the sender’s e-mail address).
That’s it. You and your correspondent can now encrypt your e-mails to each other, simply by pressing the Encrypt button when composing the message. That wasn’t so bad. Was it?
You can simultaneously digitally sign your encrypted messages by pressing the Sign button (signing is done transparently with your private key), which means that your recipient can automatically authenticate the message with your public key. This assures them that the message really came from you and has not been tampered with. Whether you do this every time or not is up to you.
Incidentally, you may notice in a message that you receive that sometimes the little seal symbol is greyed out; if you click it you will find that this is because Mail has not yet finished the online verification that the certificate is valid.
Email Encryption – The Non-Essential Details
You can do it now. You don’t need to read any further. Or skip to the bottom if you use Outlook 2010. So far I have glossed over the gory cryptographic details, in the best traditions of intelligence need-to-know. But if you want to know, here is some more background on the process.
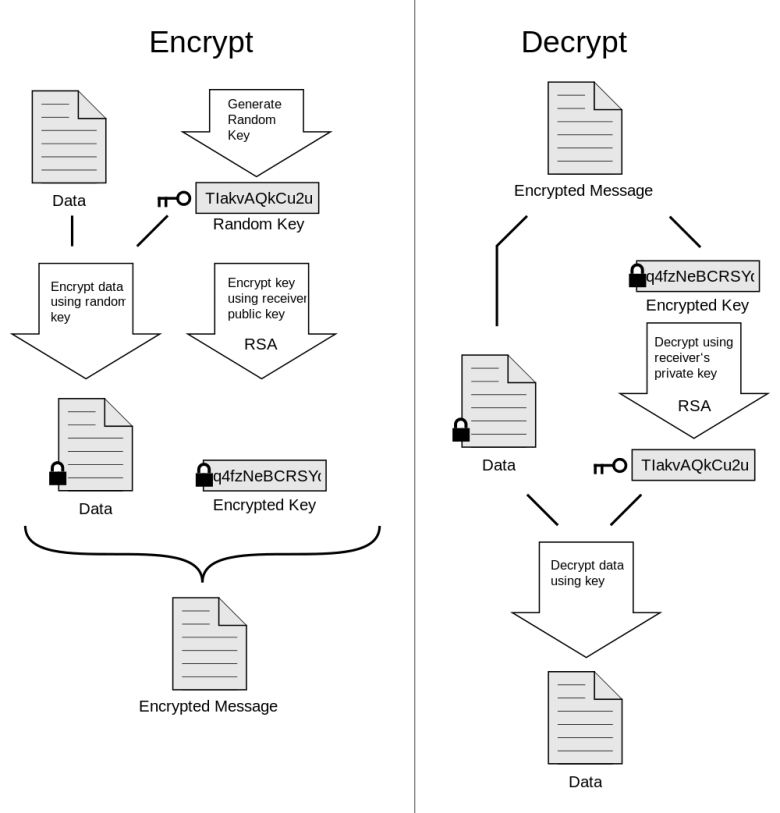
I mentioned 3DES above, and you may be wondering what happened to the asymmetric RSA algorithm. The wrinkle here is that RSA is slow in decrypting and encrypting all but the smallest message, so the message is actually encrypted using 3DES, which is a symmetric algorithm like AES. It’s a little long in the tooth now, and generally accepted as not as good as AES, but it’s still highly secure. Why does Mail not use AES? Ask Microsoft.
RSA is used only to encrypt the randomly-selected key for the symmetric 3DES algorithm. When your correspondent gets your message, they use their secret key to decrypt the 3DES key, which is then used to quickly decrypt the message.
If you go back to your contact details, in Contacts, then select Edit Contact | IDs, then select Properties and the Details tab, and scroll down to Public key, you will see that it is described as being RSA (2048 bits), which is very secure for now, although cryptographers are talking about moving to 4096 bits before too long, which will be secure much longer into the future. The signature algorithm is also shown as RSA.
Select the Certification Path tab, and you will see the trust hierarchy for this certificate. Your e-mail certificate is based on trusting COMODO to issue a secure certificate, and they trust UTN-USER to certify their issuer’s certificate, and so on back to the root authority. The PKI system is one of hierarchical trust. The PGP system is different. It’s based on a “web of trust”, which I will describe when I talk about PGP another time.
Let’s have a look at what’s been happening in the Certificate Store. Bring up the Certificate Manager again, and navigate to Certificates – Current User | Personal | Certificates. You should see your e-mail certificate in there, with its expiry date, purpose, and friendly name. Double-click on it, and you’ll see its description, details, and certification path. Now click OK, and select Action | Refresh to bring Certificate Manager up to date. Go down to Other People | Certificates, and you will see the public certificates for those who have contacted you; your own public key will also be there.
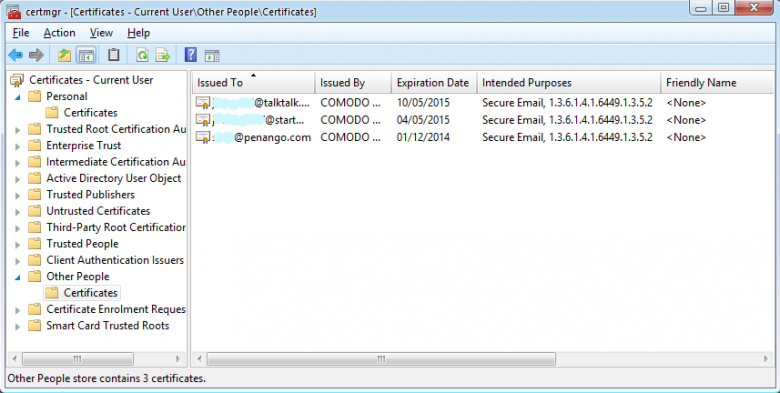
That’s because, when you send a message, it is of course copied to your Sent Messages folder, but for security you want it to be encrypted. However, you can’t make a straight copy of the message you are sending, because you don’t have the corresponding private key. Therefore your saved sent message is encrypted using the copy of your own public key in the Other People store, so that you can decrypt it with your own private key when you want to look at it.
Encrypting Messages in Outlook
 This is similar to Mail. Outlook will pick up the relevant certificate for your e-mail account from the certificate store. You should check this by navigating as follows: File | Options | Trust Center | Trust Center Settings… | E-mail Security. (I told you Microsoft didn’t make this easy). Have a look under “Encrypted e-mail” at Default Setting. It should show your e-mail address as “My S/MIME Settings”. If not, select Settings…, then Choose, for both Signing Certificate and Encryption Certificate, under Certificates and Algorithms. In each case you should be able to select your certificate from the Certificate Store.
This is similar to Mail. Outlook will pick up the relevant certificate for your e-mail account from the certificate store. You should check this by navigating as follows: File | Options | Trust Center | Trust Center Settings… | E-mail Security. (I told you Microsoft didn’t make this easy). Have a look under “Encrypted e-mail” at Default Setting. It should show your e-mail address as “My S/MIME Settings”. If not, select Settings…, then Choose, for both Signing Certificate and Encryption Certificate, under Certificates and Algorithms. In each case you should be able to select your certificate from the Certificate Store.
Note that the Encryption Algorithm is specified here as AES (256-bit) by default – that’s better! OK your way back to the main Outlook window.
Note that your certificate store may only pick up your correspondent’s public certificate (digital ID) if you create a contact for them directly from an e-mail containing their public certificate. This is the same warning I gave towards the end of the Mail description, above.
When you compose an e-mail and specify the contact, Encrypt and Sign buttons will appear on the message Options tab. (They will be missing if certificates are not available).
Now you can send and receive encrypted messages just as for Mail.
Conclusion
As I hope you have found, after obtaining your certificate and negotiating a rather tricky set up procedure, it’s pretty well plain sailing. You just need to remember to press the buttons in Options before you send a message; in fact the security dialogs give you the option to sign and encrypt messages by default, if you wish. Do please encrypt your messages if possible, whether you think you need to or not – it really irritates those nosy intelligence agencies. The more we get used to doing this routinely, the safer we will be.
You can find more explanations of S/MIME, and also PGP, encryption in the GPG4Win (Gnu Privacy Guard for Windows) Compendium, available as a free PDF download here:
http://www.gpg4win.org/documentation.html
It starts right at the elementary level, and I thoroughly recommend it. Another excellent read is the Enigmail manual by Daniele Raffo, available as a free PDF here:
https://www.enigmail.net/documentation/handbook.php
This deals principally with PGP encryption, but has an excellent introduction, and is worth skimming through to get more insight into public and private keys and their use.
You might want to investigate the free security certificates available from CAcert (http://www.cacert.org). It is a little tricky to extract and manage the certificates that they set up for you in your account, but eventually you get the hang of it.
Finally, if you really can’t get your head around all this, you could always go for the latest thing in advanced information transfer technology, illustrated below. Unfortunately the NSA has access to drones now…
Next time: PGP and Thunderbird Enigmail.


Thanks for an excellent and informative article. Gmail, the client I use, is said to provide automatic encryption for users and although most of what I post isn’t sensitive, it’s handy to know that it’s not legible to others who may intercept it.
On my laptop/desktop I use Folder Lock and Doc Lock software to ensure my client files are secured. Both programs seem to work okay.
Hi Robin,
I’m glad you enjoyed the piece, and thanks for your comment, although it worries me slightly. Correct me if I have misunderstood, but – I think Gmail is your e-mail provider, not your client. The client is what you use to send and receive e-mails, i.e. Windows Mail, Outlook, or your web browser if you are using Gmail directly (webmail). It is true that Google, and most other providers, now encrypt e-mail in transit between your client and their servers, using SSL (Secure Sockets Layer) encryption. However, once it comes to rest on their servers, they decrypt it, and can examine it and store it with the object of providing targeted advertising before they re-encrypt it to send it on to the recipient. They may also be required to provide it to law enforcement, and of course a rogue employee could also get hold of it. It is therefore not secure.
With Gmail, it gets worse. If you compose an e-mail in a Gmail web window, Gmail will start saving the text as soon as you start typing – this is supposed to make sure that you don’t accidentally lose it if you make a mistake or your computer fails. So if you compose a message in the window and then encrypt the text with some other tool, they will still have a copy of the original plaintext. Also if you write something embarrassing, then change your mind and remove it, they will still have a copy of the incriminating text, which may be kept indefinitely. People have written addons like Mailvelope to get around this. Google might have changed this recently, but I doubt it.
The only way to be absolutely sure that your e-mails are secure is to encrypt them yourself before they leave your PC, and for your recipient to decrypt them on theirs.
Thank you for mentioning Folder Lock, it’s new to me, and looks fine – they have a lot of users and claim to use AES-256 for encryption. DocLock similarly claims to use a variety of good encryption algorithms including Rijndael, which is AES by another name.
Just to add to the SSL comment. SSL only encrypts the email while in transit until it reaches your email provider. After this it’s stored and sent in plain text to your recipient which means it’s usually sent in plan text through other servers to get to the destination.
Fair point, except the last hop between the final server and the recipient is usually SSL encrypted – both IMAP and POP3 provision generally offer the option even if it’s not enforced. (One of my providers, TalkTalk, doesn’t, perhaps because TalkTalk is also my ISP, and Thunderbird protests vociferously when first connecting – makes you swear on your grandmother’s grave that you know what you’re doing). What happens between mail-servers is a different matter, but then I can’t imagine who would ever want or be able to intercept traffic over a fibre-optic trunk route(?).
Thank you for a well written and clear explanation of a procedure that would be difficult for even an experienced computer user to work out.
I hope to find a similar explanation for secure email using Thunderbird on a Linux system.
Norwel, thanks for your comment. Thunderbird handles S/MIME encryption with certificates installed via Tools | Account Settings | Security. However, it does not access the Windows certificate store; you have to select View Certificates, then Import…, and select the backed-up certificate, which will have either a .pfx or a .p12 extension, depending on whether it was backed up from the certificate store or from Firefox. Then you can Select… it, for digital signing and encryption. The procedure for sending messages is much like Mail. The certificate installation and related information can be found here: http://kb.mozillazine.org/Installing_an_SMIME_certificate ; see also: http://www.gpg4win.org/documentation.html, S/MIME sections.
There is an article in the pipeline on PGP encryption, which Thunderbird handles with the excellent Enigmail add-on. Again I don’t deal directly with the use of Enigmail, because that is covered well in the manual I referenced above: https://www.enigmail.net/documentation/handbook.php. Instead, I concentrate on the basic mechanisms of PGP; once they are understood, it’s not too difficult to work out how to use Enigmail from the manuals referenced in this article.
The only difference with Linux is that GPG is usually installed and running by default, because Linux uses it for various security-related tasks.
Excellent. Could not have been explained better. Long wondered what the heck public & private encryption keys where and how they where used.
Way back in the days of Windows 98 I tried to get friends and acquaintances to use PGP. Important when matters discussed are confidential. The problem I found was that others, who don’t see the importance or need or, more usually, are completely oblivious to the fact that emails are not a secure medium to transmit information. Confidential or otherwise. In many ways these articles are like preaching to the converted or at least those who have an interest and would like to be converted. The real problem is getting this information through to the every day user. There is only so much that can go into someone’s head. It is like trying to get my father in law to allow me to install Linux on his Windows XP machine. He isn’t computer literate, doesn’t use it much and so doesn’t see the potential for problems. And he might not get them if he uses the machine once or twice a month. But as he isn’t aware of how to look after a computer he might just find that at some point he will end up with some malware on the computer. Many have the same logic and approach to other security issues.
MacK: you are totally correct. I can’t get anyone with whom I exchange email, to use encryption. Maybe I shouldn’t have pinheads for friends?
CPA firms like mine can never get clients to use PGP. It’s hard for most people to understand PGP, let alone use it. So we simply password-protect outgoing email messages and file attachments. We use a software called AutoPW to automatically apply passwords to MS Office documents, which keeps the Excel, Word and PPT formats intact.
The article above deals with PKI (S/MIME) encryption, not PGP. I have covered PGP elsewhere (http://www.davescomputertips.com/pretty-good-e-mail-encryption-the-snowden-way/ ). S/MIME is used in corporate settings, healthcare institutions (like our NHS), legal firms, and so on. Once you have set up the certificate, encryption and signature are done simply by clicking buttons on the Outlook message Options tab. It’s automatic, also encrypts attachments (retaining their formats and other settings), and anyone can do it. AutoPW looks as though it improves a company’s workflow, from their webpage, but it costs money and isn’t necessary.
Thanks for the clarification, Martin. I’m curious, with S/MIME, do Excel file attachments remain encrypted once the recipient receives the email?
Hi Imtiaz,
The attachments are encrypted as long as they are part of the S/MIME message, but when you open it and save them to a folder they are no longer encrypted. However, if they were password-protected when attached, they will still be password-protected on decryption. It is of course possible to encrypt them before attaching them to the message, using File | Info | Protect Workbook/Document | Encrypt with Password in Word 2010. Of course your recipient then needs to know the password independently of the message.
As long as Outlook remains open you, or anyone using your computer, will be able to open the message and access the attachments after giving permission to access your certificate initially once, unless you set the strong access attribute on the certificate when you initially imported it, in which case you will need to give the passphrase. After you have closed Outlook down, when you subsequently restart it you will be asked to give permission to access the certificate again if you attempt to open the message. If you also set the Security Level to High when you did the initial importation, you will need to give the passphrase every time the application tries to access the message.