What is CryptoLocker?
CryptoLocker is a relatively new type of ransomware, and one which is particularly pernicious. For those of you who may not be aware; “ransomware” is the term used to describe malicious software which locks down the system or personal data, often via encryption, and demands a ransom (payment) in order for the user to regain access.
Wikipedia describes ransomware thus:
Ransomware comprises a class of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator of the malware in order for the restriction to be removed. Some forms of ransomware encrypt files on the system’s hard drive (cryptoviral extortion), while some may simply lock the system and display messages intended to coax the user into paying.
CryptoLocker, as the name may suggest, is ransomware which utilizes the more serious encryption method. It is a particularly nasty infection because it encrypts a user’s files on all connected drives and even over computers connected to a network via mapped drives and shares, which makes it very difficult to remove and overcome. There are no specialist cleanup tools available as yet and no known way to undo the encryption… other than to rely on paying the ransom, which is obviously a last resort and not generally recommended. What’s more, antivirus software is unlikely to prevent the CryptoLocker infection, even when totally up-to-date.
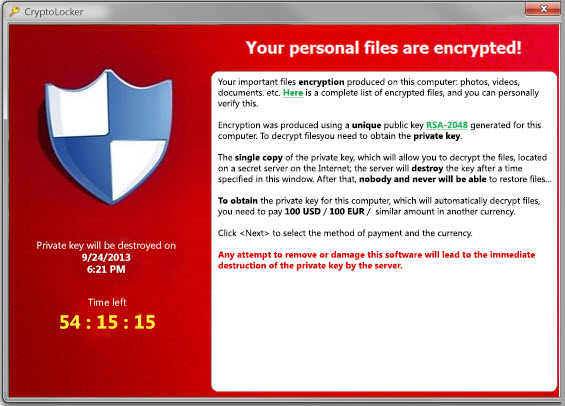
Victims of the CryptoLocker infection will see a banner informing them that their files are now encrypted and a payment will be required in order to unlock them:
How does a system become infected with CryptoLocker?
CryptoLocker generally requires some kind of user interaction to initiate the infection – clicking on a malicious email attachment for example, or downloading a malicious file. It may also take advantage of vulnerabilities in programs such as Java to deliver its malicious payload, you really should consider uninstalling Java in all but the most necessary of situations… read more on that here: You should junk your Java!
Lawrence Abrams at Bleeping Computer.com has compiled and published a reference guide to CryptoLocker here: CryptoLocker Ransomware Information Guide and FAQ. It is the most complete and informative guide I have seen on the topic, recommended reading.
Avoiding the CryptoLocker Threat
Windows Professional and above users can manually create software restriction policies to block CryptoLocker via the Local Security Policy editor. Lawrence Abrams guide, linked to above, includes precise instructions on how to do accomplish this.
For all other Windows users, who do not have access to Local Security Policy, and for those not savvy enough to manually create the restrictions themselves, FoolishIT has released a great little tool called CryptoPrevent. CryptoPrevent is portable, completely free, and very easy to implement.
CryptoPrevent – The software
Usage of the Group Policy Editor is available only in Professional versions of Windows, and is a time consuming manual task. CryptoPrevent seeks to alleviate these issues in allowing protection on ALL Windows OSes, while being easy enough for the average Joe to do, and optionally providing silent automation options for system admins and those who need to immunize a lot of computers automatically.
CryptoPrevent artificially implants group policy objects into the registry in order to block certain executables in certain locations from running. Note that because the group policy objects are artificially created, they will not display in the Group Policy Editor on a Professional version of Windows — but rest assured they are still there.
CryptoPrevent – Download and usage
CryptoPrevent is a mere 310KB zip download extracting to 906KB (Windows 7 Home Premium). To run the tool, simply double click the extracted executable.
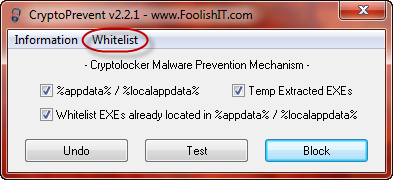
As you can see from the screenshot, the user interface is simplicity personified. Note the option to automatically Whitelist executables already located in CryptoPrevent’s areas of protection. This will allow for known pre-existing executables to be run as per normal and not be blocked by the software.
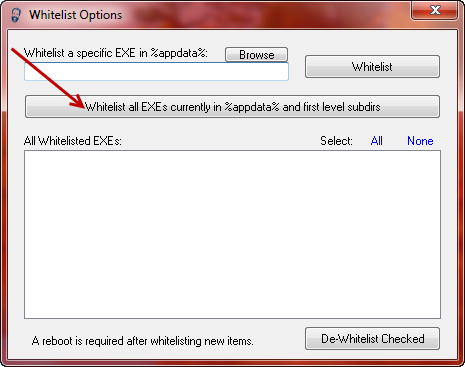
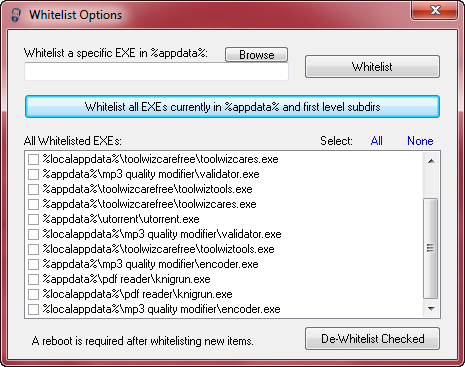
There are a handful of legitimate executables that developers have poorly decided to put in these locations, and the most popular seems to be ‘Spotify’ though there also there are a few remote support applications as well that can run from these locations. Due to this CryptoPrevent v2 comes with a whitelist editor and capabilities. From here you can view whitelisted items and add your own manually or via browse button, and also you may choose to automatically whitelist all items currently located in %appdata% / %localappdata% and their first level subdirectories.
When you are finished whitelisting, simply click the Block button and CryptoPrevent will do its thing (requires a reboot to complete the process).
- View more information about CryptoPrevent and download direct from the developer here: http://www.foolishit.com/vb6-projects/cryptoprevent/ (scroll down to the bottom of the page for download links).
Final Word
When it comes to mitigating the threat presented by CryptLocker and similar ransomware there is no substitute for the advice commonly and regularly afforded by security experts everywhere. But, even if those dictates are followed rigorously, there is still the chance that the system may become infected. If or when the cybercriminals may alter their approach in order to bypass CryptoPrevent’s current areas of protection is anyone’s guess but, right now, I think it is a terrific little tool and wholeheartedly commend the developer.
In any event, the onset of ransomware such as CryptoLocker emphasizes DCT’s mantra to… Backup, Backup, Backup!!

Hi Jim,
Thanks for another great segment of information which was also in a reliable ‘techie’ newsletter I received yesterday. Accordingly, the information indicated that Emsisoft Anti-Malware, I use the Pro version which I run daily, was the only anti-malware program with the capabability of blocking CryptoLocker, but I was thinking of installing CryptoPrevent as a primary/secondary defence, even though Emsisoft on the Web show, with in-depth technical information, how CryptoLocker is subversively installed, and their program can prevent the installation, link below.
http://blog.emsisoft.com/#sthash.PbU8ofpb.dpbs
Your advice in the matter will be greatly appreciated.
Regards,
Jonno
Hey Jonno – If I am reading the Emsisoft article on CryptLocker correctly, they are saying that Emsisoft Anti-Malware is proven to block CryptLocker when it is delivered via email attachment. However, there is no mention of other possible methods of delivery, which suggests to me that the system may still be vulnerable to a CryptLocker attack under certain circumstances.
Bottom line; there is nothing to lose by also utilizing CryptoPrevent and likely something to be gained.
Cheers mate… Jim
Well, I downloaded and installed CryptoPrevent, opened the WhiteList options and left it at WhiteList all Exe’s currently in…. and clicked block then restarted my PC. But when I went back to check, there were no executables at all in my list, like there are in your list above! So I can’t see how that is going to do anything on my PC?!!!
Sheri, trusted executables would not normally reside in the locations under CryptoPrevent’s protection, but this is where the malware CrytpLocker typically places its executables. If the whitelist is remaining blank, that’s a good thing, nothing to worry about.
Cheers… Jim
Update: I am able to run all the currently installed programs that I have just tried without them being blocked by CryptoPrevent, even though my Whitelist is showing as empty. So the only way I’m going to know if it’s doing anything to protect me is to install a new program and try to run it. If CryptoPrevent blocks it, I will know it’s working. If it doesn’t, I will know it isn’t working! Will post back results.
Sheri – CrytoPrevent should not prevent normal (trusted) applications from running, provided the executables are in their normal location. Sometimes, even trusted applications will place executables in other folders such as AppData or Temp. These are the areas under CryptoPrevent’s protection because this is also where the malware CryptoLocker typically places its executables.
In most cases, normal programs will run fine. Occasionally, if a trusted application has placed an executable in a location under CryptoPrevent’s protection, it will be blocked from running… that’s where the whitelist feature comes into play.
Cheers… Jim
CryptoPrevent is most welcome, but proving totally inscrutable to someone who is a very experienced computer user, but still apparently extremely ignorant. If I click on a test, I get the message “Prevention not applied or unsuccessful”. – Is that good or bad? – If I click Block, I’m told something’s been done and I should reboot. Should I have clicked Block? – Also, my Whitelist Options display shows none of the checkboxes shown in your discussion, nor do I have a clue as to which, if any, of them I’d be advised to check. — Hope this level of ignorance doesn’t discourage trying to help!
Hey Justine – The “Prevention not applied or unsuccessful” message means CryptoPrevent is NOT protecting the computer. Follow these steps:
1) Run CryptoPrevent (make sure all three boxes are ticked)
2) Click on the “Block” button
3) Restart the computer
4) Run CryptoPrevent
5) Click on the “Test” button and you should receive the message “Prevention successfully applied”
Step 3 – restart the computer – is an essential step. After the rebooot you should now see a list of executables included in the whitelist. If there are no exes whitelisted, which would be a tad unusual, it is a good thing, nothing to worry about.
Cheers… Jim
Thanks! All steps completed, apparently successfully. – Still didn’t get a list of executables in the Whitelist Options display, but figured/hoped that clicking on “Whitelist all EXEs currently in %appdata% and first level subdirs” might be worthwhile. – Now off to try to fill in a few ignorance holes.
Hello Jim, and otherreaders. This happens to be a very timely article with me. Just a few days ago I was hit by a cryptoware, or rather – a ‘ransomeware’ nasty. Just a year or so ago I also was hit by another ransomeware that brandished a pretty fancy construction of the CIA logo and a lot of inflated verbage that anyone actually familiar with Federalese language would be able to immediately recognize that it was not the real McCoy. Likewise with this most recent ‘hit’ that I mentioned above. This time the ransomeware brandished a simulated logo of the Homeland Security! The sentence structures and terminology, while intending to sound official, was NOT authentic enough, and again, anyone actually familiar with government writing would be able to instantly recognize that it was not real. BUT… with the little logos that they had “plegiarized” (recognize that word in the news lately … LoL!) those Federal logos of the Dept. of Homeland Security. Well, I knew what I had been hit with, but I didn’t have any tools to deal with it, so off to my local Best Buy’s Geek Squad counter. NOW I will happily add this new tool to my ‘puter, thanks to DCT’s generosity for sharing this info. Thanks to you, Dave and everyone there.
You are most welcome Dane. Hopefully, CryptoPrevent will help you avoid yet another instance of this type of nasty infection – twice bitten, thrice shy. 🙂
Cheers… Jim
What’s with this name “Foolshit”? I downloaded CryptoPrevent, installed it even paid and registered. My Son says it’s got to be a scam who would do business with a Co. called Foolish-IT. I hope it is not a scam because I sent this column and advice to my Boss he is always getting infected I have no idea where he browses but he has had every ransom-ware know to man in the last six months. I really hope this is not a joke!
Well here is an addition to my previous email just a few Min’s. ago, I thought I would try your internet speed test CryptoPrevent prevented this action, your application tried to Exe. in appdata this makes me feel better!
Yes, the name “FoolishIT” is certainly an unusual choice Carl. It may be meant as a bit of a joke but I can assure you that the man behind the name and his CryptoPrevent software are anything but. CryptoPrevent has been endorsed by people such as Lawrence Abrams at BleepingComputer and the highly respected security expert Brian Krebs… you can’t get much higher recommendations than that.
Is there a effective way or a decent antivirus could settle the problem of a already infected PC? Actually most anti-virus could prevent this kind of virus, but haven’t see any av could solve it.
Hi ive just downloaded cryptoprevent 4.3.0 after i got it on my pc luckily i’d just backed it up the previous day.Can anyone explain what the second app in the crypto folder does the TestCLI,and i use emisoft A.M free would the paid for version protect me fully from all forms of this ransomware,and many thanks for any info regarding this matter
It simply runs a test for the user to make sure that the protection has been applied. CryptoPrevent’s main interface includes a “Test” button, clicking on this button runs TestCLI.exe which lets the user know if the machine is protected or not.
I couldn’t say for sure Adrian. Your best best would be to contact Emsisoft support.
Hope that helps,
Cheers… Jim