Some background information
Once upon a time, in Computerland, there was a nasty villain named ‘Virus’ who delighted in inflicting damage and generally being a nuisance, so Computerland introduced ‘Anti Virus’ to aid in warding off the attacks. After a while Virus realized that merely creating havoc wasn’t really all that rewarding so he brought other kin into the fray, ‘Spyware’ and ‘Adware’. This was more like it, now the villains could spy on the population and force them to view unsolicited advertising too. Computerland retaliated by throwing ‘Anti Spyware’ and ‘Anti Adware’ back at them… I would like to be able to conclude the story on a happy note but, alas, the battle rages on.
These days we need to protect our computers and precious data against; viruses, spyware, adware, worms, trojan horses, crimeware and rootkits. These are collectively known as malware….a portmanteau of the words malicious and software.
What is HIPS?
A Host Intrusion Prevention System (HIPS) protects by constantly analyzing a computer’s behavior and monitoring for any key changes. Whenever malware attempts to make those changes the HIPS will block it and notify the user. Sometimes legitimate software will also need to access key areas and on those occasions, provided you recognize and trust the source, you can choose to ‘allow’ the change.
Definition based products (those with which we are most familiar) rely on their definition data bases to identify threats. The data bases are frequently updated to keep up with any new threats (also known as zero day threats). Because of the lag time involved between identifying new threats and applying updated definitions, HIPS is generally regarded as better at protecting against zero day attacks. This from the Threatfire site:
ThreatFire is dramatically different to traditional antivirus software. Normal antivirus products usually need to have first identified and seen a threat before they can provide adequate protection against it. The protection is then provided via a signature or fingerprint update, which must first be written by an antivirus researcher. This creates a large window of time where threats are undetected and can therefore infect your PC even when you have antivirus software installed.
Another great advantage of installing a HIPS based product is that it generally plays nice (does not create conflicts) with definition based software… So, it is a terrific adjunct to any existing definition based protection.
This from Wikipedia:
HIPS compliments traditional finger-print-based and heuristic antivirus detection methods, since it does not need continuous updates to stay ahead of new malware. As ill-intended code needs to modify the system or other software residing on the machine to achieve its evil aims, a HIPS system will notice some of the resulting changes and prevent the action by default or notify the user for permission.
You’ve probably heard it over and over; do not install more than one anti virus or anti spyware….well, with HIPS based Threatfire you can!
Keep in mind though that all running programs use valuable memory resources (RAM). If you install too many or your computer’s RAM is inadequate you may experience a general slowing down. (of your computer that is, not you personally). Some HIPS based programs can also be quite intrusive, engendering numerous popups requiring user input. I’m happy to report that Threatfire is not among them, it quietly goes about its business requiring virtually zero interaction.
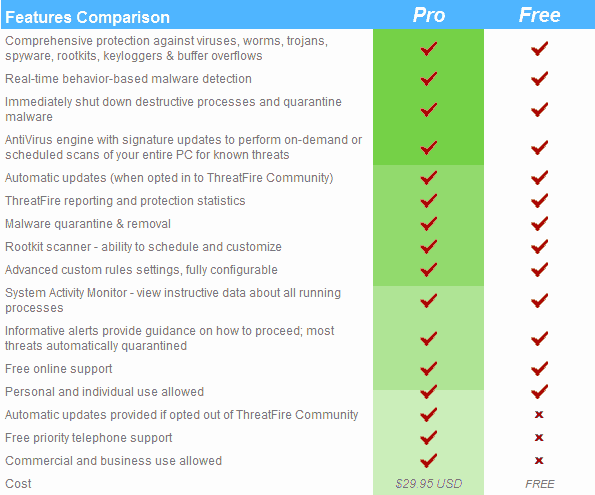
Threatfire is published by the reputable PC Tools who are responsible for numerous security applications including the highly regarded Spyware Doctor.Threatfire also has a paid version which includes free priority telephone support and can be used for commercial purposes; both versions offer the identical level of protection. This list of features and comparisons from the Threatfire site:
Threatfire – the program
Threatfire’s (version 4.0.0.8) initial execute/setup file is a 22.6mb download, installed program size (on my Vista machine) is 34.7mb. Installation is quick and easy with no hidden ‘extras’ or traps and all options are pre-selected to recommended settings…so Threatfire is all ready to go.
Threatfire protects against viruses, worms, trojans, rootkits, some spyware and includes a rootkit/threat scanner, which is a handy addition.
Let’s take a look
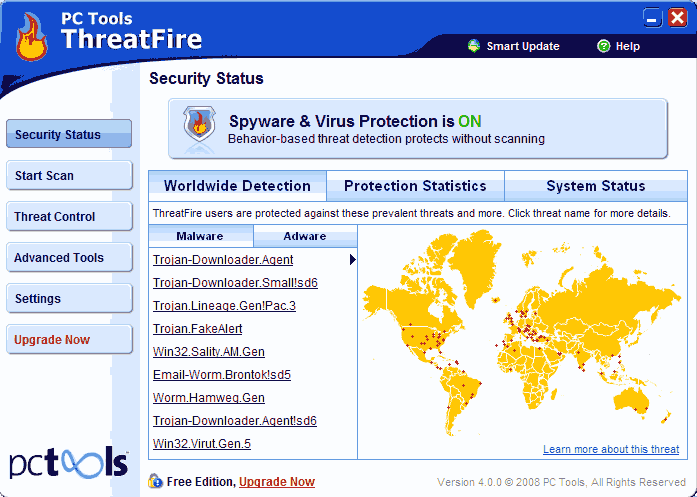
This is Threatfire’s main screen and interface. From here we can access all of its features.
Okay, now let’s view the screen for each section when selected down the left hand side of the main interface.
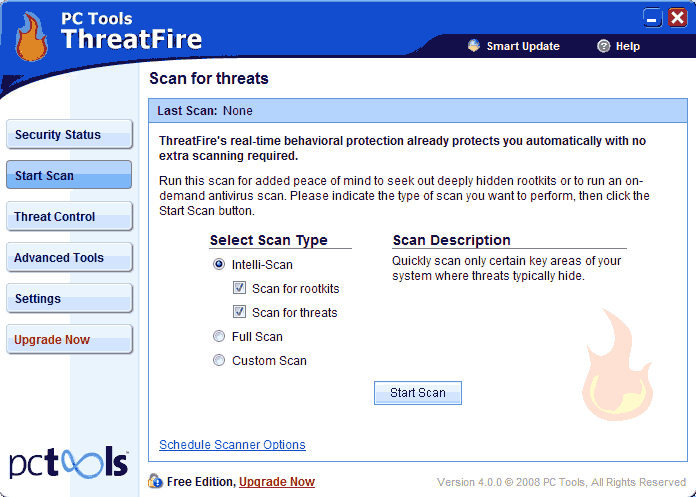
START SCAN: From here we can select scan options and run a scan.
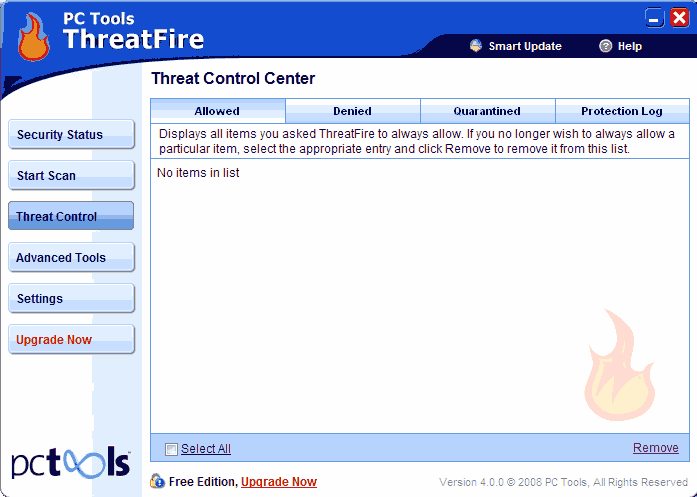
THREAT CONTROL:
Allowed/Denied: Displays all historical data relevant to threats reported, listed under the appropriate tab.
Quarantined: Allows for managing quarantined items. From here, items may be restored or permanently deleted.
Protection Log: Displays a log of all actions taken by Threatfire and all processes monitored or examined for signs of suspicious behavior.
ADVANCED TOOLS: The warning here is quite clear; do not mess with this section unless you are a very experienced user.
Advanced Rule Settings: The expert user can apply custom rules.
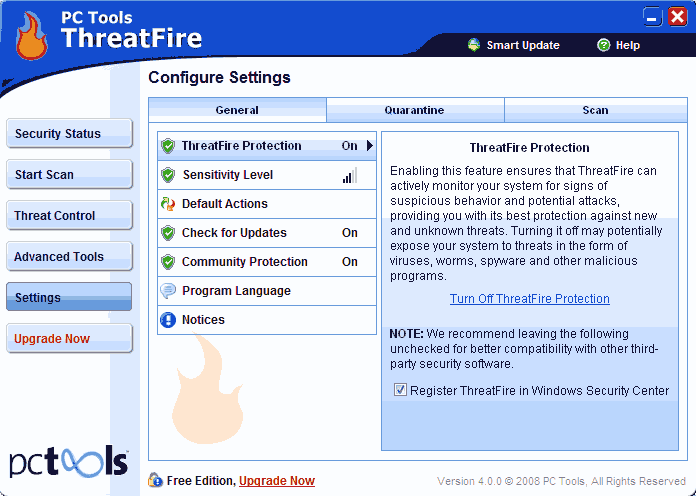
SETTINGS: Turn features on and off, set sensitivity level and access additional options.
Sensitivity Level: Can be set from one to five. Be aware that the highest level (level 5) will also display the most alerts. The default/recommended level (level 3) represents the perfect compromise (see next screen).
Quarantine: Option to enable automatic creation of system restore point prior to performing any quarantine actions.
Scan: Option to set scheduled scanning; daily, weekly or monthly.
Security sensitivity level.
You will notice the ‘Help’ icon displayed in the top right hand corner of each screen, although Threatfire is very easy to set up and use.
I like Threatfire a lot, it’s long been an integral part of my security setup and really increases the level of protection when used in conjunction with traditional security programs… Highly recommended! You can read more and download from here: http://www.threatfire.com/about/.