Links to all articles included in this series:
- The Beginning: Opening introduction to the series
- Browsers: What are they? How to make them a safer door to Web.
- Search Engines: The Good, Bad and Ugly. Understanding search results.
- Malware and Virus: What is Malware? – What is a Virus? What is the difference in their types? How to avoid them. How to know if you are infected. How to remove them. (you are here)
- Phishing: Signs of phishing, phishing emails, phishing sites
- Computer Optimization: Why is my computer slow? What can I do about it?
- Improving Your Email Experience
- Enjoying Your Computer: Social Media. Entertaining Activities. Educational Activities.
Whenever your computer is behaving a little slow, erratic, or something just does not feel right, it is easy to think you have a virus but before you  determine if you are infected, perhaps it is time to first understand all the things that can infect a computer.
determine if you are infected, perhaps it is time to first understand all the things that can infect a computer.
Viruses are just one of many malicious programs that can infect your computer. To paraphrase Sun Tzu in his book on the art of war, “Understanding your enemy makes you stronger.” That’s how I feel you should look at malicious software. Arming yourself with the wrong program can leave you exposed to other attacks. For example:
One of the first things my customers say after asking me to fix their infected computer is “How did this happen, I have an antivirus program installed“? Normally the answer is unfortunately, it was not a virus that infected you.
Just What Is A Virus?
Most people call everything that infects a computer a “virus” but as I mention above, that is not the case. Viruses can and do infect computers but criminals have managed to increase their arsenal of weapons to include all types of malicious software. Therefore, starting with Virus, let’s define each type of malicious software and we will conclude with what you can do to keep yourself safe.
![]() Viruses were initially given that name because they tend to spread and act very similar to their living counterparts “human virus.” It is a term used to describe a malicious piece of software that replicates itself by inserting copies into other computer programs and files. They may also reside in the boot sector of the hard drive or your computer’s memory.
Viruses were initially given that name because they tend to spread and act very similar to their living counterparts “human virus.” It is a term used to describe a malicious piece of software that replicates itself by inserting copies into other computer programs and files. They may also reside in the boot sector of the hard drive or your computer’s memory.
Computer viruses can be harmful, some are playfully malicious causing no permanent damage, but nonetheless, removing all viruses from your computer is a must. A computer virus may spread via email attachments, shared files from a USB flash drive, DVD, CD or even by clicking on an infected file while downloading it to your computer.
Viruses are not normally self-propagating, they normally don’t contain the internal code to spread themselves, but instead, rely on people to spread them to their circle of friends and co-workers.
The way many antivirus programs work is by obtaining a list of “all known” viruses and using that list to protect you. If any virus on that list tries to infect your computer, it will recognize it and stop it from doing any damage. However, viruses tend to mutate, that is they will change enough code to be unrecognizable to your AV program. Because these mutations can occur overnight, AV programs do not always prevent you from being infected but by downloading new AV definitions, it will allow you to (disinfect) your computer after the infection. That is one reason why you should have the program set to continually update the virus definitions to ensure full protection.
Malware
The word malware is short for malicious software. It may be defined as any software used to disrupt computer operations. Depending on the intention of the malware, the disruptions may be minor or very bad. Malware first gains access to your system where it is then capable of manipulating your programs to display ads, demand money, and gather private information. Malware is often defined by how they invade the system or the type of damage they are capable of doing. We will be covering each of those below.
Spyware
A software program that can gather information about you without your knowledge and may send that information to someone else. It is commonly used for tracking and storing your movements on the web and in some cases use that information to send pop-up ads to your monitor.
Spyware is also known for having key loggers which log all keyboard action and therefore can capture your passwords, bank ID numbers and other private information. Normally classified into four types, Spyware may be defined as Trojans, Adware, System Monitors, i.e. key loggers, and tracking cookies.
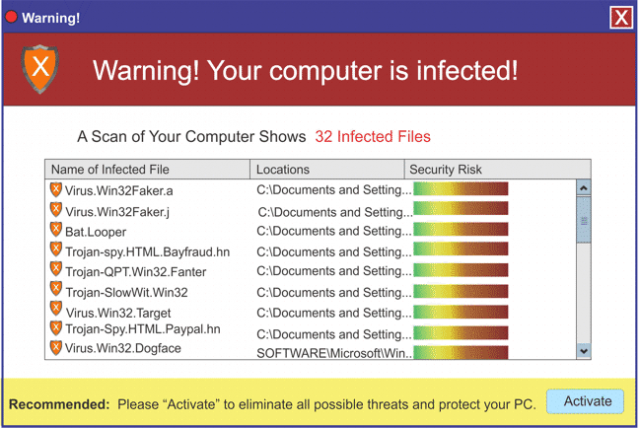
Scareware
This is malware that uses a computer users fears into believing they have a serious problem on their computer. In many cases, the user will initially download what they believe to be a free optimizer or other free but helpful software. The program will then scan the computer and produce what appears to be a ridiculous number of “errors” that they can fix for $19.95 or some other amount. You may actually have one or more of the viruses listed or none but it is trying to scare you into buying it to fix your machine.
In reality what may be happening is:
- They manufacturer a program that detects issues on your computer and then offer to clean some of them but if you want all of them cleaned you just need to purchase their program.
- To increase the scare, they might list every occurrence of an issue on your computer as an error but in actuality is not an error. For example if you have 3018 items in your recycle bin that just needed to be deleted or 2010 items in your “Temporary Internet Files Folder” it would list it at 5028 errors. Don’t fall for scareware. Remove it from your system and try one of the many free alternatives available to you to fix these types of issues. See the list at the end of this article.
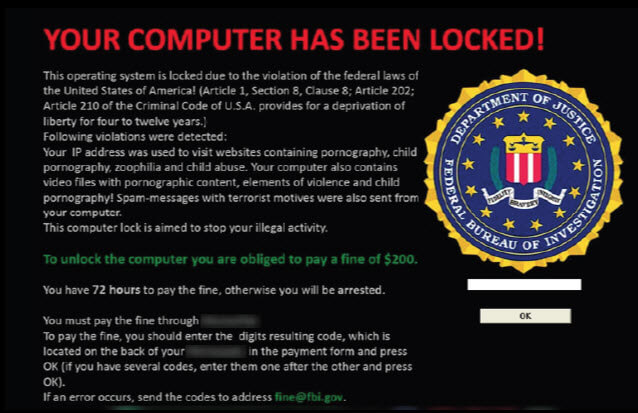
Ransomware
 This is a type of malware that is very similar in look to the above ScareWare. The difference is that it locks you out of your computer until you pay a ransom. No matter what you do, it will continually flash “Danger” messages and keep the disruptive behavior going until you feel you have to agree to its demands. In many cases, paying the ransom will still not release the computer. It is always best to aggressively remove any Ransomware from your computer.
This is a type of malware that is very similar in look to the above ScareWare. The difference is that it locks you out of your computer until you pay a ransom. No matter what you do, it will continually flash “Danger” messages and keep the disruptive behavior going until you feel you have to agree to its demands. In many cases, paying the ransom will still not release the computer. It is always best to aggressively remove any Ransomware from your computer.
RansomWare, unlike the the ScareWare above, is actually demanding money before you may proceed. This type of Warning Notice is meant to frighten individuals into paying to get their computer back.
Rootkit Virus
This is a type of virus that is designed to hide the fact that you have been compromised. They very often replace your system files with infected files that are very difficult for your antivirus program to detect. One of their biggest advantages is placing themselves in an area so they will be activated before the operating system boots up. This makes them very difficult to detect. They are not the actual danger, the rootkit hides malicious code like Trojans, Worms and other malware. The name rootkit comes from combining the Unix term for the administrator account called “root” and the software pieces “kits” that implement the tool. There are special programs designed to detect (not defend) rootkits and most of the major companies offer them for free. Programs like Rkill, TDSSKiller, Malwarebytes Anti-Rootkit are some examples.
Worm
A computer worm is a program that replicates itself and attempts to spread to other computers most commonly through a network. Unlike a virus, a worm does not need to attach itself to another program on your computer. They are best known for what is call “service attacks” where they spread themselves so much and so fast that they bog the bandwidth of networks and can be used to target certain IPA’s.
Trojans
Trojans are another type of Malware. Named after the story of the Trojan Horse, they infect your computer by acting as useful items like a program or an attachment to an email. Trojans normally do not infect other files like a virus or make copies of themselves like Worms. Their best offense is to remain unknown to the user. Trojans contain malicious code that carries out certain actions that may cause system harm or steal private information from the user. Trojans are usually very malicious to you and your system.
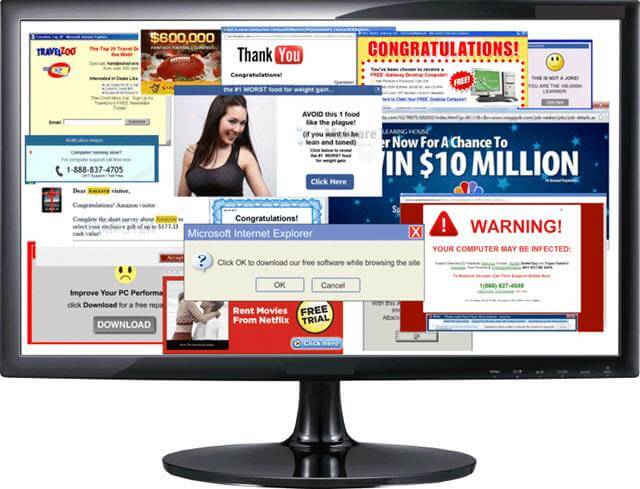
Adware
A lesser form of malware* in the sense that it normally does not try to exploit sensitive data from the user. Some adware is seen in legitimate software as a way to cut development costs. Many computers come loaded with adware. They attempt to generate revenue by offering up ads on your computer screen or while surfing the Web. Each time you click on one of the ads or purchase a product after clicking the ad they receive revenue from that vendor. Some “free software” or apps for phones are heavily loaded with adware to offset the cost of the “free.” If you do not mind a few advertisements popping up, the freeware may be worth it to you. In this case, adware is just the price paid.
*Some adware is indeed malicious. It is capable of introducing you to other forms of malware like Trojans, Viruses and Worms. Unless you know the cause and are okay with it DELETE IT. Don’t let your adware take over what you see on the web.
Bloatware
 This is a slang name used for programs that have excessive features that takes up a lot of disk space and or memory. They might not do actual damage to your computer or steal information but they can take up valuable resources both on your hard drive and memory.
This is a slang name used for programs that have excessive features that takes up a lot of disk space and or memory. They might not do actual damage to your computer or steal information but they can take up valuable resources both on your hard drive and memory.
Some bloatware, loads a lot of sub programs. Printer software is a prime example in this category. Just loading one printer program might load small programs to notify you of the printer’s status, notify the user of constant updates, load OCR readers, photo changing apps, organization apps and a host of others when all you wanted was the printer to print. Some PC manufacturers are also in this category. All too often, they allow third party software to be loaded on your computer.
To give you an example of how bloatware can get out of hand, look at this potential scenario. If your black and white laser printer, your color inkjet printer, your computer manufacturer and a graphic editor program all decide to “Give” you a free copy of a photo organizer, you may have four different versions of a program you might not even use. Give your computer a diet and use a system optimizer to rid yourself o these useless programs.
Tracking Cookies
![]() Tracking cookies are very similar to cookies but they are intended to create revenue for the individuals that create them. They are not put on your computer by normal websites but by third party entities. They tend to track your total usage across all websites. This is usually not desirable, because it keeps track of everywhere you go and everything you do and buy. While most tracking cookies may be classified as, not good to have on your computer, some are very dangerous by sending the information they track to individuals you would not want having that information.
Tracking cookies are very similar to cookies but they are intended to create revenue for the individuals that create them. They are not put on your computer by normal websites but by third party entities. They tend to track your total usage across all websites. This is usually not desirable, because it keeps track of everywhere you go and everything you do and buy. While most tracking cookies may be classified as, not good to have on your computer, some are very dangerous by sending the information they track to individuals you would not want having that information.
PUPs
This is an acronym for “Potentially Unwanted Programs.” This does not mean that there is an infection on your computer just that the program that discovered it cannot tell. Even if the program is not really infected with a virus or malware, it is certainly not needed to operate your computer effectively. The suggestion would be to delete all unknown PUPs. It would be great if websites posted a warning like the one below, but I am afraid they don’t. You must always assume that if they can inject PUPs into your download they will.
SPAM
Spam is not necessarily malware, in its basic form it is defined as unsolicited email or sometime referred to as junk mail. It is however, difficult to tell some spam from infected email so I have decided to list it here with malware. Bot-nets distribute about 80% of all spam. Most spam is exactly that, junk mail. Your email address may be captured from chat-rooms, customer lists, websites and viruses that harvest your email address and sell it to other spammers. Source for percentage: Wikipedia Email Spam

Protection
Protection comes in many forms, make sure you download or purchase a program that will actually protect your computer. An Antivirus program may not remove spyware, adware etc. An adware program will not remove a virus. If an antivirus program does not make claims of total security, or that it can also remove Malware, it probably cannot. A good idea is to have an antivirus and an anti-malware program on your computer. If you do have an Antivirus program that does function as a multiple defender, you must be careful about also using an Anti-malware program with it. They may clash. In addition, optimization programs have their purpose but they are not Anti-malware programs.
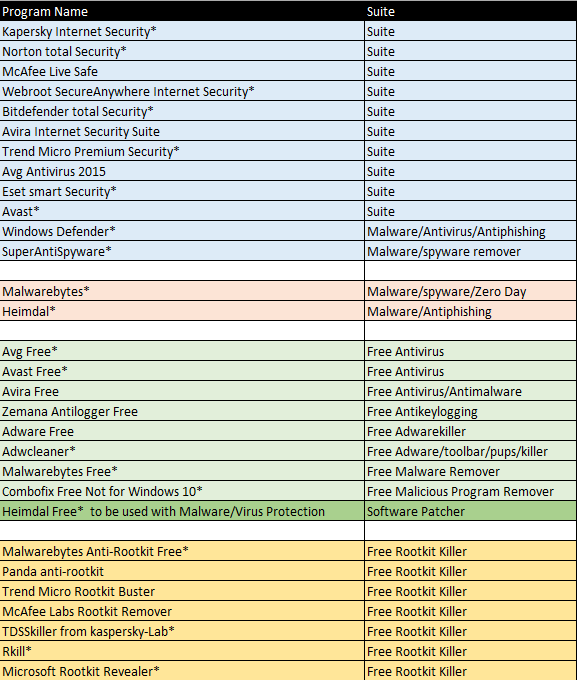
 The following list is not a recommendation for a particular software, but rather a list of programs and what they claim to do. It is important to remember that many of the vendors that sell these programs sell multiple versions of them. So buying McAfee Antivirus is certainly not buying McAfee LiveSafe. The end user (you) is responsible in making sure that the anti-malware software or combination of programs you purchase will work in protecting you from all infections.
The following list is not a recommendation for a particular software, but rather a list of programs and what they claim to do. It is important to remember that many of the vendors that sell these programs sell multiple versions of them. So buying McAfee Antivirus is certainly not buying McAfee LiveSafe. The end user (you) is responsible in making sure that the anti-malware software or combination of programs you purchase will work in protecting you from all infections.
Some companies are known for their Antivirus programs and have learned to add features like anti-malware security, identity theft protection, anti-spam, in their security suites, some companies focus on trying to be the best Anti-malware protection like Malwarebytes, and finally some focus on all types of Spyware. The choices are yours.
Best Known Antivirus Programs
In all of the programs mentioned below, I would recommend that you review the details carefully. Don’t confuse this with a website listing “The 10 best Antivirus Programs.” I am not gaining by pushing one over another and have no gain in your choice. I have put an * for each program that I have personally tested and know to work as advertised
I have listed what I believe to be all reputable companies, for the major brands in Blue. I have only listed the Full “All-In-One” versions. Just about all of them sell their products at prices very much reduced from the price on their site. I really encourage you to try their full version free trial. If it is what you are looking for you may then purchase it. Just make sure to review the different versions from each. I have listed primarly Anti-Malware Programs in Orange. The “Free” versions from these and other companies are shown in the Green and finally the RootKit Killers, which are all free are listed in Gold. Remember, many of the free versions do not have all the protection that a full featured paid version has. I did not give links to each of the sites because I want you to select the program best suited to your own needs. In addition, I have listed Heimdal in dark green, while it is free, it is not a stand-alone product. It alerts you to updates for vulnerable software that some of the free antivirus programs don’t.
I would like to finish up with a couple of thoughts, first, there is no software that can claim to be 100% effective because there are just too many variables.
Next, each of the programs listed here can protect your computer or remove malicious threats, once detected but there is a lot more to measure than just being able to remove a malicious piece of software. That is of course our number one concern but let’s break that down. In the first group, some protect you while surfing better than others do, some protect your identity better than others and unfortunately, some do it at a cost of resources far greater than others.
Finally, of those that I have used in the first group, Webroot, is the smallest in size and the fastest in scanning than any I have come across. Norton has always done a good job at protections but it is very resource hungry. These are just things to consider. Many of the programs listed are reviewed right on this site by the authors on DCT. Give them a read to get a better feel. In closing, I would love to hear which protection software you do use and how effective you believe it to be.
Terminology
Resource Hungry Some programs operate by taking over many of the computer's resources. Memory and storage are two biggest issues. If you have an Antivirus program that makes working on the computer impossible while it is scanning it is eating up all your system's resources. You may have to schedule the scans when you do not expect to work on the computer.
Bandwidth This is the transmission capacity of the computers communications device or system as well as your Internet Provider. If you are the only person on the IP's bandwidth, technically, you would have the full width of the transmission band and therefore have the best speed. If you were one of thousands, you would have the share the same bandwidth.
OCR An acronym for Optical Character Recognition. Software that will scan and covert hard copy text into electronic text.
Temporary Internet Files (Folder) The is a folder on Windows which holds the browser caches. Each browser may have it's own cache. Each time you visit a website using a browser, images, script, and html code is saved to the TIF folder. The next time you visit that page, the website will only download data that has changed making your browsing faster. The downside is this can quickly fill up your computer with a lot of junk files. I recommend setting your browser to delete it's history every time you close the browser or use a program like CCleaner to remove them occasionally,
Service Attacks Often referred to as "DOS" or Denial of Service attack is when a user or organization is prevented from being to use the services of a resource they would normally expect to have. These attacks do not take personal information from your computer but can block you or any other user by flooding it with more traffic than it is designed to accept. Hackers attack computer users and then use their victim's machine to send out email, or large data packets to a single IP address. Some major companies like Amazon, Ebay, and others have been attacked.



I do not use any anti-this or anti-that ..they simply do not work effectively all the time.
I believe the most effective protection is a sandbox ..simple to use and it trusts no program or trickster.
Whatever you do on line protected by a sandbox is not installed on your hard drive or operating system. It even protects from infected email attachments.
A sandbox does not need constant updating because it treats everything as a potential risk and trusts nothing or no one.
I use ”Sandboxie” which is free but does have a 5 second buy message after one month of free usage, however it still works normally if you do not want to buy.
I often test this program buy deliberately exposing my computer to infected downloads …the infection remains contained within the sandbox and is deleted either automatically or you can set to delete periodically.
It works and it works well. I recommend it to the old guys at the Men’s shed.
http://www.sandboxie.com/
John in giving your reply a second thought, I think it would be a good topic to post on the site. As soon as I finish this series for novices, I will address it. It may help to have more people knowledgeable about using a sandbox app.
You’re preaching to the converted John. We’ve already published articles recommending isolation techniques for security, and Sandboxie in particular: http://www.davescomputertips.com/sandboxie-why-everyone-should-be-using-it/
John, I use sandbox myself. Along with virtual desktops, they are valuable tools to keep a user save. I do however believe they are less effective than zero hour protection and the reason is because; telling people not to use antivirus software is like telling people not to use sunblock because staying out of the sun is much better protection. In theory both are correct but in reality, they are not, people are going to go in the sun and download virus without first running it in a sandbox. That is just life. Also, my article is aimed at the novice and includes optimization as well as protection against malware. Having the tools to remove an infection don’t guarantee safety it just adds a layer of safety. While I applaud your diligence and think it wise, I don’t think it is common. Thanks for you comment. Jim