A new vulnerability known as “Logjam” which allows the exploitation of secure TLS connections has been uncovered and it affects most popular browsers. Here’s how Weakdh.org describes it:
The Logjam attack allows a man-in-the-middle attacker to downgrade vulnerable TLS connections to 512-bit export-grade cryptography. This allows the attacker to read and modify any data passed over the connection. The attack is reminiscent of the FREAK attack, but is due to a flaw in the TLS protocol rather than an implementation vulnerability, and attacks a Diffie-Hellman key exchange rather than an RSA key exchange. The attack affects any server that supports DHE_EXPORT ciphers, and affects all modern web browsers.
Browser developers are supposedly in the process of preparing updates but, at the time of writing this article, I checked the three major browsers I have installed and both Firefox (38.0.1) and Chrome (43.0.2357.81 m) were both reported as vulnerable. Somewhat surprisingly, Internet Explorer (11.0.9600.17801) was the only one of the three given a clean bill of health.
How to Check Your Browser for the Logjam Vulnerability
There are currently two sites you can visit to automatically check your browser for the Logjam vulnerability:
- https://weakdh.org/ – if you visit this site and receive the following message, then your browser is vulnerable:
- https://www.ssllabs.com/ssltest/viewMyClient.html – similarly, this site will display the following message if your browser is vulnerable:
How to Fix the Logjam Vulnerability in Firefox
According to reports, the Logjam vulnerability won’t be patched in Firefox until the release of version 39. However, a temporary fix has been published on the Mozilla forum for Firefox users which involves accessing “about:config” and disabling the ssl3 protocol:
- In a new tab, type or paste about:config in the address bar and press Enter. Click the button promising to be careful.
- In the search box above the list, type or paste ssl3 and pause while the list is filtered
- Double-click the security.ssl3.dhe_rsa_aes_128_sha preference to switch it from true to false (this usually would be the first item on the list)
- Double-click the security.ssl3.dhe_rsa_aes_256_sha preference to switch it from true to false (this usually would be the second item on the list)
- Restart Firefox
I applied both changes myself and visited the two aforementioned sites again, both reported a clean bill of health.
For any browsers that are being reported as vulnerable, I strongly suggest users keep a close eye out for updates and apply same as soon as they become available.
More information here: The Logjam (and Another) Vulnerability against Diffie-Hellman Key Exchange – (security expert Bruce Schneier reports that the vulnerability may have been exploited by the NSA)


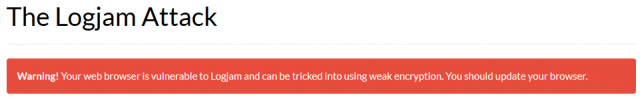
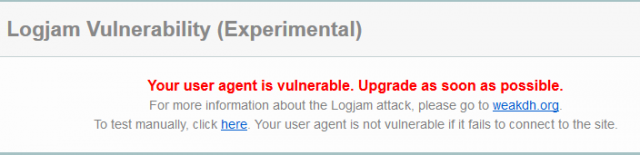
“developers are supposedly in the process of preparing updates but, at the time of writing this article, I checked the three major browsers I have installed and both Firefox (38.0.1) and Chrome (43.0.2357.81 m) were both reported as vulnerable. Somewhat surprisingly, Internet Explorer (11.0.9600.17801) was the only one of the three given a clean bill of health.”
This is because IE is no longer the lack luster browser it used to be, out of the three major browsers IE is now probably the best protected as far as vulnerabilities goes now. Chrome pretty much ignores theirs and Firefox well ….. is just Firefiox (honestly I haven’t used a 32bit browser in years as Firefox openly refuses to build one) .
Now with Windows 10 with Edge on the verge of being released there really will be no reason to even install Chrome or Firefox on it …… Edge is that good.
Reset my two ssl3 security values as advised.
Jim. IE 11 might be clear of logjam, but here’s what I got using the latest IE11 and your link “https://www.ssllabs.com/ssltest/viewMyClient.html”
“Protocol Support
Your user agent doesn’t support TLS 1.2. You should upgrade.
The protocols supported by your user agent are old and have known vulnerabilities. You should upgrade as soon as possible. The latest versions of Chrome, Firefox, and IE are all good choices. If you can’t upgrade IE to version 11, we recommend that you try Chrome or Firefox on your platform”, Mindblower!
Just checked the latest IE version on that site again MB. All clear on TLS 1.2 BUT it is now warning me that IE is vulnerable to Logjam. ????
Seems the tests on that site may not be terribly reliable.
Re-checking IE on the first site mentioned (https://weakdh.org/) is still displaying a NOT vulnerable message.
My IE11 checked good on both sites, I just don’t use IE11 that much.
Thanks Jim, I always read you articles and find them really useful.
This was no exception, I applied the fix for Firefox.
Carried out the Logjam mods as advised and am now ok, Thanks Jim.