 What is Fileless Malware
What is Fileless Malware
There has certainly been a lot of misinformation concerning “fileless” malware starting with the notion that this is something new. The Concept of malicious code that only resides in memory and exists without an executable file on your computer came to our attention by Kaspersky Labs as early as 2001. In what was to be later named Code Red, the attack was actually a worm that existed in your system’s memory as opposed to the more common type of malware that usually produced a malicious file within your system.
So why is a type of malware that has been around for over 17 years such a hot topic today? Primarily because the average user was not the target. Fileless malware is sophisticated software that was used to attack major companies, particularly, financial institutions. With endpoint security being such a big issue, major AV companies have started to introduce a variety of detection methods known as New Generation AntiVirus (NGAV) to protect their clients. Companies that are prepared to fight these attacks now must promote not only the solution but make everyone aware of the problem.
Different Types of Detection Methods
Traditional Antivirus Software
Traditional Antivirus software uses a “Signature” approach to deal with malware. Every malware has a distinct hash (signature) that once discovered and filed into a database, can be recognized by traditional antimalware programs. AV programs check every new file being installed, along with current files on your computer, against a database of known bad files. If the new file matches any file in the database, it is blocked from running and targeted for deletion or quarantine.
Considering that there are about 390k of new malware signatures created every day AV programs have to update as often as every hour requiring internet access and computer resources, and it also increases the size of the database.
Machine Learning Anti-Malware
To improve their ability to detect malware, companies started using Artificial Intelligence (AI) to check new files being installed and those that are running on your computer. Through an analysis of each characteristic exhibited by a file, the program matches the historical behavior of known bad files and uses that to determine if a file is suspicious. If it determines that it is indeed suspicious, it will be blocked as potentially malicious. It uses the old idiom approach, “if it looks like a duck, and quacks like a duck, it is probably a duck”. The major drawbacks with this approach are finding false positives and bothering the user with “is this OK” popups.
New Generation Anti-Virus (NGAV)
The newest approach in detecting malicious behavior is the behavioral approach. It does not look for malware files but rather checks the behavior of files, processes, events, applications, and even TCP/IP connections to determine if they are acting as expected. If not, and it fits the profile of malicious behavior, it can block a single or stream of events from processing. This new generation approach can, therefore, block not only known malware but non-malware, zero-day attacks and even malware that has yet to be developed. One of the most vulnerable attack sites for fileless malware is endpoint devices.
Endpoint Device
An Endpoint Device is any device, usually mobile, outside of a corporate firewall. In most cases, this means a laptop, smartphone or tablet. These devices can be connected through TCP/IP or can be directly attached to a corporate system.
Endpoint Security
NGAV has proven effective all along a network and is particularly useful in securing endpoint intrusions. If an employee accidentally introduces malicious code through an endpoint device, and therefore into a major system, the intrusion can quickly be isolated because the NGAV is constantly analyzing the system for any behavioral changes.
What is Malware?
There are several known types of malware. In its simplest definition, it is a combination of two words, (malicious + software = malware). The name, however, covers all the different types of malicious code.
Each type of malware can affect our devices differently and each is recognized and handled differently. There are, however, common traits with all malware:
- They must first infect your system by tricking you (the user) or your system software into running it
- It must install itself on your system and use the programming commands built into the code to prevent detection and removal
- It must perform its preprogrammed operations required to achieve its goals
Malicious Code
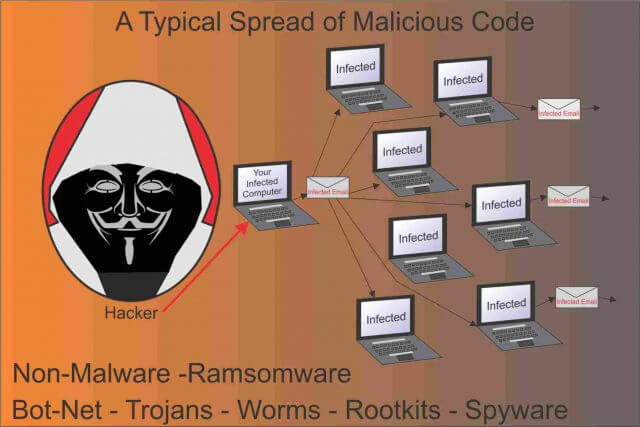
When we are discussing malware, we are describing any of these variations: Viruses, Worms, Trojans, Adware, Spyware, Rootkits, Botnets and Ransomware, and even non-malware.
While Microsoft operating systems are correctly presumed to receive more malware than other operating systems, the first virus was written for Apple. The Elk Cloner was created as a prank by a 15-year-old HS student in 1982. It attacked Apple’s DOS 3.3 OS.
However, greed, sabotage, politics, and simple revenge quickly became the underlying reason for bad code. Many people believe that malicious code is created by major AV companies just to sell AV programs. With the sheer number of legitimate threats created daily, there is no need.
Viruses
Viruses, the most common type, act like their biological counterpart. Their intent is to harm the target, they tend to self-propagate by latching onto healthy executable files and spread not only through your device, but they are capable of spreading through TCP/IP connections to infect other devices. They can steal hard disk space, access private information, corrupt data, send email to your contacts, contain keyloggers and some can completely disable systems. Detection relies primarily on knowing their signatures against a database of known viruses. Some attempt to hide their signatures by placing infected files inside zipped files. Because ZIP files are so large, they are often skipped by some AV programs. They are also delivered through browsers over TLS/SSL. Because SSL encrypts all transmissions including the virus code, it makes them harder to identify.
Worms
Worms are actually in the same class as viruses but have the ability to self-propagate. Meaning they don’t need human intervention to spread. Nor do they need an executable host file to do so. Because they can self-propagate, they can use your email to send out hundreds or thousands of replications to other users.
Trojans
Just like their name suggests, they infect your system by hiding the malicious code in seemingly innocent files. They can attack systems through email, phishing attacks, and fake websites or files. They can completely destroy a system, spy on users and steal any data through keyloggers. Trojans work by gaining the user’s trust by acting like a useful program. Without you, Trojans can’t work.
Adware
While malicious, it’s main focus is to direct you to purchase products through ads, typically through misdirection and pop-ups. Adware can be very tenacious and hard to remove.
Spyware
More than 50% of all malware attacks have some aspect of spyware capabilities. It is called spyware because like a spy, it does everything it can to navigate your system to avoid detection and removal.
Rootkits
These are one of the most tenacious malware types because they dig deep into the root of your system and once established, opens a backdoor that allows access by hackers. They are infamous for blocking AV programs from running, making it difficult to delete them from your system. They give hackers access to introduce additional malware. Some require special rootkit removal programs.
Botnets
This malware is used to make Distributed Denial of Service attacks. Most victims infected with a botnet may unwittingly participate in a DDoS attack as the botnet uses their device to overwhelm sites by flooding them with hits to a specific IP address. Normally, botnets must receive instructions to know where or when to attack. This process is known as “phoning home”.
Ransomware
This malware can be extremely malicious as demonstrated in the attacks on hospitals, banks and even home users since 2017. Once they infect a system they can block access to all the data contained within the system. They typically offer the end user a chance to pay a ransom that would unlock their data. Failure to do so, and in some cases attempts to remove the ransomware, would render your computer data useless.
Fileless or (non-malware)
A higher frequency of attacks and new approaches in defeating it has made non-malware appear in recent headlines, particularly in business environments. Because this type of infection does not place actual files on a system it is very difficult for traditional AV programs to discover the infection. It has evolved over the years, making it the first choice of attack for hackers because it basically outsmarts all traditional forms of antivirus and anti-malware programs.
How Does Fileless Malware Work
Like any standard malware, it still must first enter your system. Likely methods are scripts like fake Java, Flash or Silverlight updates. One attack, the fileless trojan Kovter, posed as a Firefox update. In addition, traditional methods are also used to infect systems with fileless malware– Spam email, downloading bundled software, Torrent downloads, etc. One of the most common methods is when users quickly press OK on an AV’s pop-up warning thereby letting the malware into their system.
Fileless exploits stay in your system by becoming part of an existing process like Windows PowerShell, the Registry, or WMI. This gives the malware the ability to remain undetected on a system. Undetected means it can remain in your system and attack at the hackers bidding. It has the ability to gain administrator access while still remaining hidden, which of course means it can do whatever it wants to gather data from a user’s computer and use that information to lock a user out of their system, sell the information to other hackers and use your system to exploit other systems within or outside your network. It is important to note that fileless malware can and often does work in conjunction with traditional malware.
Last year at this time, an endpoint protection firm, “Barkly”, published a report stating that 29% of all attacks in 2017 were fileless attacks and suggested that percentage would increase to 35% in 2018. It also suggested that fileless assaults were 10 times more likely to succeed compared to other types of malware.
Not Only Windows Anymore
Without a doubt, the Windows-based OS is targeted and infected with the greatest frequency by all malware. The reason should be obvious when you consider that Windows comprises 88.28% of the market.
Hackers, trying to maximize their profit, are less likely to attack a Mac Operating System that totals only 9.13% of the market and fewer still are going to target Linux systems that hold just a 1.52% share. All other operating systems including the Chrome OS total just 1.16%. When we talk about an OS we are normally talking about computer-based systems. However, that just might change. With the millions of iPhone and Apple OS devices being used as endpoints, a hacker’s attention is drawn to these attractive and desirable targets.
Endpoints are becoming the most common way to compute and communicate with a fixed machine. The old saying, “a chain is only as strong as the weakest link”, comes to mind because an endpoint is a fixed machine’s weakest link. An attacker does not care who they have to infect if the end result of the attack is profitable.
Summary
Yes, right now fileless malware appears to target larger systems simply because that is where the money is. Don’t think for even a second that PCs aren’t next. The more effective non-malware is, the more likely it will be used and adapted to PCs.
Right now, NGAV is looking like our best long-term tool in keeping systems free from all forms of malware. But PC users can still benefit from using the best-known ways to prevent infections:
- First and foremost, keep your Operating System updated by making sure you have automatic updates enabled. Older Operating Systems are the easiest to infect
- Make sure you have an antivirus and malware removal program installed and working
- Don’t ignore the warnings by your protection programs. They are asking for a reason
- Use a browser with a built-in Ad-blocker or install an add-on to your existing browser. Pop-ups and Ads are excellent avenues for infections
- Be wary of free downloads or bundled downloads. Many extra programs are introduced through bundled downloads and it is easy to hide malicious code in any of them
—



Extremely thorough detailed article Jim. A five star rating is not high enough. Happy you mentioned Kaspersky as I did my own research years ago when I switched protection software. No regrets in putting my faith in software products made outside North America, Mindblower!
Thanks, Mindblower, I like Kaspersky myself, I find them to be aggressive in the war on malware, I like that.
Very interesting reading Mr. Jim.
Thank You
Agree !
Thank you for this comprehensive article which has been so helpful. I’ve had my own battles with malware. Your explanation of the different types of malware is beneficial to all website owners. As cybercriminals continue their malicious activities, it is critical for all of us to be vigilant to protect our sites from infestation. I found the summary tips to be very informative.
Awesome!