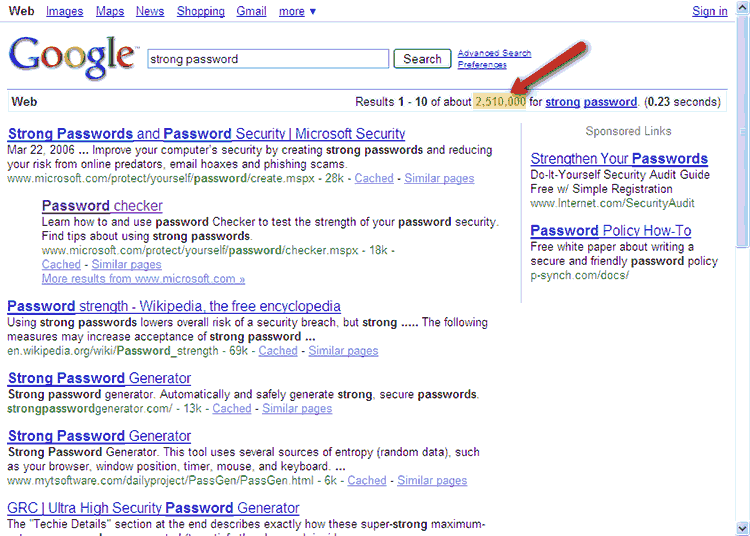
Do a search on “strong password” and you’ll get a couple of million hits, everything from definitions to tools and websites with password generators. You’ll even see some sponsored ads for people trying to sell password strength-related services.
It’s a hot topic and opinions vary widely. You’re told time and again that your password should be a long string of random characters, the
longer the better. My articles on how
to create unguessable passwords serve as a good example of current thinking on the subject. Maybe, like me, you tend to create strong passwords for everything (truth is, I sometimes use weak passwords–more about that later). Is it really necessary to have passwords that would take a few quadrillion years to crack and use those for everything, or can you get away with weaker ones for some things? And what about those sites—even some credit card and banking sites—that force you to use only upper and lower case letters and numbers? Are those passwords strong enough? The answers may surprise you.
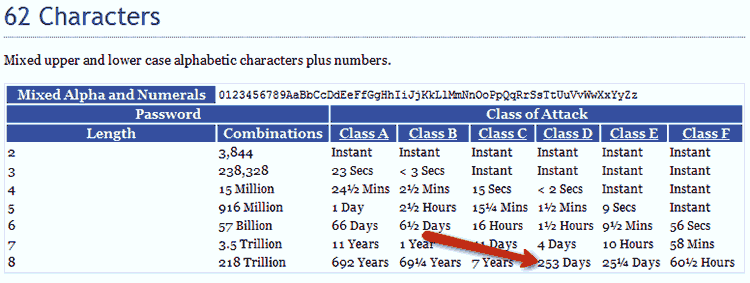
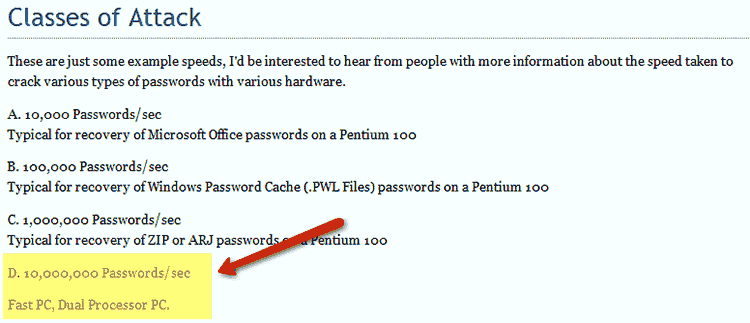
First of all, it’s not necessary to have passwords that require half an eternity to crack, no matter what the experts say. If your password is complex enough that it’s unlikely it can be cracked before you change it, chances are that’s strong enough. Let’s say the password for your on-line banking site is MyPass21; a brute force attack against your account would take around 253 days–call this the password recovery window (PRW) – if an attacker was using a fast, dual processor PC (see charts – the complete set of them is available on the Password Recovery Speeds website). If you change your password every six months, it’s highly unlikely that anyone would be able to compromise your account using brute force.
What about on-line magazine sites, photo sharing sites, and the like? These often require “registration,” mainly so they can
legally send you email solicitations. They ask for your first name, maybe an email address, and want you to create a password. There’s no
danger that any personal identity or financial information is going to be revealed if someone hacks your account, so who cares? In this
case, a weak password is strong enough. I call these things “nuisance passwords” and I always use the simplest, most easy-to-remember
password I can get away with, usually the same as my login name. For example, my login for one site is ken and my password is kenh.
It’s up to you to evaluate the importance of the information you’re protecting with your passwords, so I won’t presume to tell you the ideas I present here are absolute. However, I can say with absolute certainty that a 20-character password using mixed upper and lower case alphabet plus numbers and common symbols (96 characters), subjected to a class D attack (10,000,000 guesses per second) could take up to 14,015,805,234,633,679,975,229,169 years to crack. I’d say that’s strong enough.
I can’t wait for the rest of the story.