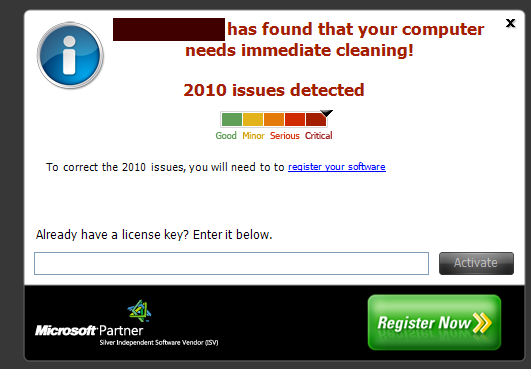
Is that the year 2010? Nooooooo. Believe it or not (and most novices DO believe it), the message says that my computer has . . . drum roll . . . 2,010 CRITICAL issues on a registry scan.
Do you actually think my computer WOULD EVEN BOOT if it had as many as . . . 2,010 CRITICAL issues in the registry?
And notice the urgency: “immediate” cleaning, like if I don’t drop everything and do it right now, my world’s going to explode!
These marketers know their business.
This article is a three-part series about rogues . . . not about any specific one but rather how to identify them and then we’ll take a look at how these beasts are distributed, what some of the detections REALLY mean, and what to do if you’re duped by one of these things.
Throughout Part 1 here, I’m going to bombard you with screen shots of these ridiculous warnings, and by the time you read through this first part, you’ll be more than familiar with this scare tactic. (These screen shots are of older versions ON PURPOSE . . . outdated versions disguise the title more . . . see “Legal Threats” below)
And, by the way, I know a lot of these things are much more sensitive than CCleaner and such, but calling tracking cookies and “missing entries” (more on that in another part) as “critical” or “severe” errors is a bit over the top, isn’t it? I mean, c’mon, these are trivial errors at best and calling them critical only serves to get the novice to bring out the wallet to pay for these things to be removed (which is the whole purpose of this scheme. . . as I said, these marketers know their business) when FREE software does the job just fine anyway.
First, though, we need to establish a definition so that we are all on the same page.
It would be nice if everything in this world were black and white and there were no blurred lines. The truth, in many cases, lies somewhere between the two extremes.
The term “rogue” is a good example.
Relative to the term “rogue” . . . there is a technical definition and a “common usage” definition. Very often the two are different. What is meaningful is what YOU take as the definition, which is often the “common usage” type.
While sticklers/computer nerds may insist that the technical definition is the “right” one, “rogue” in common usage is generally taken to be ANY piece of software that renders a detection result (most often on a scan of the windows registry, but things like “optimizers” supposedly scan other areas, like start up programs) that scares the bejesus out of novices with numbers like the message above displays and then offers to remove the nasties IF YOU PAY.
The terms “scareware”, “hostageware”, and “crapware” (there are a few others that I probably missed) are perhaps more descriptive, but the common usage term for all of these is “rogue”.
Time for another dose of scary numbers:
OK, I’ve beat this one to death. If you don’t know by now, you SHOULD: This article is directed more to novices, i.e. those people who speak plain English, rather than to geeks.
I want to point out here that DCT is NOT hiding anything. Blocked out/blacked out areas cosmetically make it look like the document is the result of a Freedom of Information Act query or it is otherwise a cloak and dagger effort to hide information (my cloak is dirty and my dagger’s rusty.) Clearly it’s not the case here that DCT is hiding pertinent information and acting fraudulently, and I don’t want anybody to get that impression.
My redactions are to protect DCT from any potential legal action . . . which is a very REAL possibility as you’ll see below.
And another display of those scary numbers:
LEGAL THREATS:
You may be wondering, “What in the heck does ‘Legal Threats’ have to do with identifying a rogue and what does it have to do with dealing with rogue scan results and why is he even bringing this up?”
Well, there’s two big reasons I bring it up here and mention it early on.
First, I myself have been threatened:
Now on the letter itself, note that last paragraph. That is the classic legal threat.
Coupla’ other things about this threatening letter too.
You’ll notice that in the second paragraph the mouthpieces claim their “client” is a “proud member of organizations such as . . . blah, blah, blah.” “Microsoft” is one of the “organizations” . . . though curiously they don’t state WHICH Microsoft organization, leaving the reader to speculate that somehow these guys are endorsed by the 500 pound gorilla on the block.
This is a common scare tactic of rogues. Frequently you’ll see this “seal” on the site:
Now on this “legal threat”, I was prepared to articulate all my facts in an open court and meet these clowns head on.
So I didn’t respond, and essentially said “bring it on”. And the blog owner didn’t respond either. Haven’t heard from them since I received that threat (and that was three years ago) nor has the blog owner.
Was it a risk? Yes. Would I do it again? Not sure . . . I dodged a bullet there and I called their bluff that time and got lucky, but I have since cooled down and a cooler mind prevails. At the time I was a little too cocky, a little too big for my britches, and intoxicated by my “evidence”. More on this “legal threat” stuff in Part 2.

Wow! The first part of your ‘Part 1’ is setting out what I and most other reasonable ‘noob?’ already suspected, but the part about the ‘Suits’ coming after you is something I hadn’t reckoned with. I got fired up about McAfee two years ago (sorry) and shared my extreme annoyance in a few blogs. (I did have an email trail that backed up my case.)
I will save this page and reread it every so often. Can’t wait for Part 2!
Thank you for taking the time to post.
jayesstee
them screens remind me of windows anti virus 20-XX. I have had a few people with things like that i think the worst i came across was where someone paid them but they took more than the amount they stated. I think with them putting Microsoft on they could of used a sticker it would look better. I seen a program on a while back about it as well it was on something called click its the BBCs program for technology and they basicly got that on your computer or laptop and you became a host for the program for everyone else quite scary really. I think what i think is are they going to do the same on smart phones or Ipohones as they get ever more popular have not seen it yet but i bet it is coming. i have never seen it in legal form on a pice of paper.
Hey Guys – Thanks for your comments. I’m responding on behalf of Bob who is laid up at the moment. Hopefully he’ll soon be on the mend and back with part 2.
Cheers… Jim