When Criminals Take Over Your PC
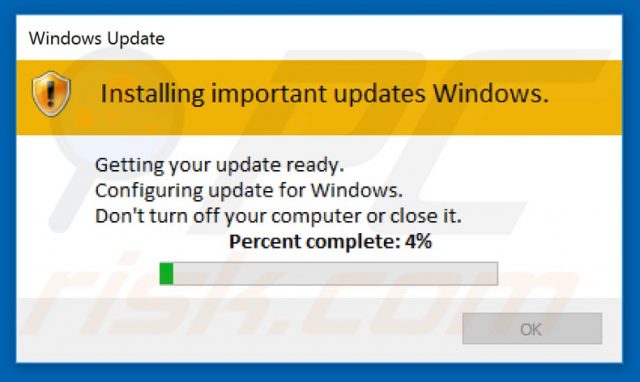
A couple of days before New Year’s Eve, I received a very anxious phone call from a customer saying that he could no longer open any of his files. Windows 10 had suddenly changed and he could no longer turn off the machine. I then asked what was currently taking place and he told me that a Windows Update pop-up was showing in the bottom-right corner of his screen which he couldn’t get rid of. I then asked him to tell me what the update message was saying and what it looked like. He described the pop-up as yellow and white and it was at that point that I asked him to physically unplug the computer and bring it over.
Once I had the PC in my workshop, I disconnected all the hard drives apart from the boot drive, switched on, but the PC failed to boot, showing a Windows message saying that the computer needed to be repaired. At this point# I had no idea what had occurred but had to assume that a serious virus had taken over his machine and before any further action was taken, it needed to be eradicated. Discussing the situation with the customer, he assured me that he had backups, both on an external drive and with Google Drive and OneDrive. However, he couldn’t remember if everything had been backed up. I might also add that this was a gaming machine with huge amounts of data spread over five different hard drives.
All Your Files Belong To Us
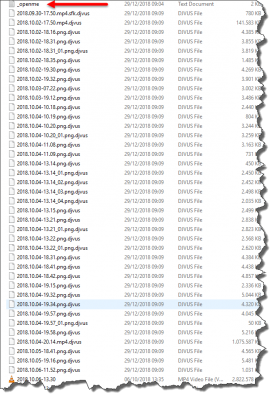
I then booted the PC to an emergency Win10PESE pen drive in order to see exactly what had happened, but I wasn’t really prepared for what was to come if I’m honest. A quick glance at the Documents folder was enough to know that a serious infection had taken place since every single file of every type or description had been appended with the .djvus extension, thus rendering the files totally useless. For example, a file named myvideo.mp4 had become myvideo.mp4.djvus. At this point, I wasn’t entirely sure whether the virus (or whatever it was) was active outside a true Windows environment, so I fired up Malwarebytes and Eset anti-virus scanners one after the other and after some time, both programs identified eight threats. If I remember correctly, two of those were trojans. As it happens, I was a little concerned about taking screenshots at the time, but suffice to say that both programs removed the threats. However, the damage was already done, as you can see in this screenshot.
Ransomware had arrived.
I then Googled the term .djvus and discovered that it’s a variant of Stop Ransomware, that first made its appearance in December 2017, where the criminals use a data-locker. The malware uses a combination of AES and RSA to encrypt data and adds a ransom note to every folder that contains the hijacked files, viz:
The note says pretty much everything we need to know– all the files are locked unless you pay to unlock them. Neither of us was prepared to give money to criminals so we both agreed that the best way forward was damage limitation. As an aside, I edited one or two files in a rather naive act of desperation, by removing the .djvus extensions just to see if they would open up, but clearly, they wouldn’t since they were now heavily encrypted and we didn’t have the key.
Limiting The .djvus Damage
Subsequent research into this particular ransomware told me that it has surfaced only recently, and to date, no decryption method has so far been released. My first port of call was the No More Ransom Project, an initiative by the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, and McAfee, with the goal of helping victims of ransomware retrieve their encrypted data without having to pay the criminals. They have a database of decryption tools developed by anti-virus specialists which are available for download free of charge but unfortunately, my customer’s particular ransomware has not yet been cracked so no tool is yet available. I then submitted samples of encrypted files to Bleeping Computer and a number of other specialists so they could be examined with a view to aiding in a decryption tool being compiled for this particular ransomware. I’m currently waiting for some good news, but in the meantime, we needed to decide how my customer would be best suited to move forward. Fortunately, the customer is well versed in computer technology and he was able to tell me about the symptoms presented when he first realised he had a problem. Windows Task Manager had been disabled (greyed out), Windows Defender, which he had temporarily disabled (**I’ll get to that later) had been completely nobbled, all his programs had become unusable due to every extension being modified (including the registry) and all Windows’ vital boot files had been compromised, resulting in a destroyed operating system.
Satisfied that the threat had been removed from the boot drive and that whatever important files he had kept there were synced to the cloud prior to the infection, I moved whatever data we hoped could be decrypted at a later date, over to another drive. This is important since the actual files may be encrypted but they are not infected in themselves by the ransomware. I then carried out a very long and tedious scan of his other drives which revealed no major threats and then reinstalled Windows 10 on his newly formatted boot drive. I have to add that this entire process took a couple of days and once the other drives were reconnected, I ran another scan with Windows Defender and no further threats were detected.
**He had temporarily disabled Windows Defender’s real-time protection in order to download a cracked copy of a program he wanted to use from The Pirate Bay— enough said.
The end result of this nasty episode is that the encrypted files have been isolated to a specific folder, all his programs have been reinstalled, including the downloading of hundreds of gigabytes of games (all these had also been encrypted) and Windows Defender is now permanently ON.
I later beefed up his Windows Defender protection to include Controlled Folder Access, the details of which can be found in Richard Pedersen’s excellent article Windows 10 Quick Tips – Ransomware Protection. I also installed Malwarebytes’ free trial, so it’s up to him whether he subscribes to it or not. In the meantime, I’ve asked him to keep a lookout for email with possible decryption tools for the .djvus ransomware, as I will also do myself. It’s also worth noting that numerous articles have been written at Dave’s Computer Tips on the subject of ransomware and a quick search, as per this screenshot, should bring up several very useful tips.
This entire experience is a salutary lesson about the wickedness that abounds throughout the Internet and whilst tech writers and anti-virus specialists cannot hope to, or even pretend to police what people do with their computers, the old mantra remains true– if it looks suspicious, it probably is.
—






An interesting story indeed. Excellent lesson – one should NEVER disable protection to receive files, even “so-called” system-up-date files. But playing with torrents, the not so common “common sense” should slap (wack) the persons head if the only way to download a torrent is to disable protection. Downloading a cracked program is asking for problems (actually begging for pain). Glad you were able to assist him and wonder if he learned for this experience, Mindblower!
Hi Marc,
Thanks for the story.
To disable protection, and, download a cracked copy from Pirate Bay (a cracked copy from anywhere) is surprising from someone who is ‘well versed in computer technology’.
Hopefully this article will jolt some people and remind them how important it is to keep their security running at all times.
JoninOz
If wanting to download any app etc that requires shutting off virus protection you should use a dedicated clunker pc that is sacrificial and you do not compromise you files
Dave,
There are several methods of ‘playing safe’, Sandboxes, Virtual Box, BufferZone and more.
Cheers,
JD