Today, I read an article in The Wall Street Journal about a Disney employee whose life was destroyed because he didn’t have two-factor authentication (2FA) turned on in his password manager. I thought, “What an idiot! He certainly was not a DCT reader! All DCT readers would have 2FA turned on for their password manager.” I then rethought this. Some DCT readers may not have 2FA turned on. Also, we have new DCT readers all the time. I decided to show how to turn on 2FA in two popular password managers, 1Password and Bitwarden, so something like this could not happen to a DCT reader.
Background
Matthew Van Andel was a Disney employee who decided to download an artificial intelligence program from GitHub to his home computer that would create AI images from text prompts. The AI program was malware that gave the hacker behind the program complete access to his computer. It also gave the hacker access to Van Andel’s password manager, 1Password. That’s the same password manager that I currently use!
Van Andel used 1Password to store passwords, sensitive information, and “session cookies” (digital files stored on his computer that allowed him to access online resources including Disney’s Slack channel). The hacker published online every 1Password login credential that Van Andel had stored.
In addition, the hacker used Van Andel’s Slack credentials to publish more than 44 million Disney messages online. The hacker also used Van Andel’s login credentials to steal from Disney. The hacker published private customer information, employee passport numbers, theme park and streaming revenue numbers in a huge data dump.
As Van Andel investigated his break-in, he realized that his 1Password account wasn’t protected by a second factor! He had not taken the extra step of turning on two-factor authentication.
Van Andel was fired from Disney after a forensic analysis of his work computer revealed that he had accessed pornographic material on the device (another stupid thing that he did).
Stupidity
Van Andel made a lot of dumb mistakes. First, Van Andel was an engineer for a Fortune 50 company. He knew he was a target for hackers and should have been careful. Second, he downloaded a piece of unknown software (this wasn’t a small app but a large application with nodes, libraries, wheels and executables). Third, the article didn’t say this, but my guess is that he loaded all this in an Admin account giving the malware complete control of his PC. Fourth, it took him five months to run a secondary antivirus (which found the malware immediately, by the way). If you are loading dangerous items like this, you need more than a single layer of protection. Fifth, he did not have 2FA turned on for his password manager. Sixth, he was visiting porn sites on his work computer.
Not Password Manager’s Fault
I use 1Password as my password manager. This was not the fault of 1Password. The hacker had unrestricted access to Van Andel’s computer for five months. The hacker did not get into 1Password’s servers, nor crack 1Password’s encryption.
Note: It is possible that with so much access to Van Andel’s PC, the hacker may have gotten into his 1Password account even if 2FA was turned on.
What Is Two-Factor Authentication?
Two-factor authentication (TFA) or (2FA), multi-factor authentication (MFA), and two-step verification (2SV), are all different names for essentially the same thing. Proving your identity via a second means. 2FA requires people to verify their identity based on two of the three factors that can confirm identity:
- Something you know (e.g., a password)
- Something you have (e.g., a phone)
- Something you are (e.g., a fingerprint or facial scan)
This is not new and DCT readers are not strangers to 2FA. I found an article on two-step verification back in 2014 in the DCT archives. And Jim Hillier wrote an article in 2021 and another in 2023.
Types Of Two-Factor Authentication
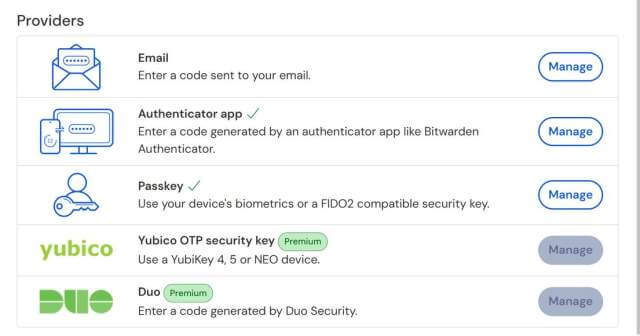
Common types of 2FA used in password managers ranked from weakest to strongest:
Email: A message sent to your email. Negatives are that there could be a delay in the arrival of the message, and it is only as secure as your email account.
SMS: A text message sent to your phone. Negatives are that it is susceptible to SIM card swapping, and messages could be intercepted.
Authenticator: Uses a hash-based one-time password authentication standard. One-time codes are synchronously generated on both the client and server sides using a cryptographic algorithm.
Duo: An authenticator app for businesses.
Hardware Key (Yubikey): A physical hardware key that needs to be inserted into a USB slot to authenticate the user.
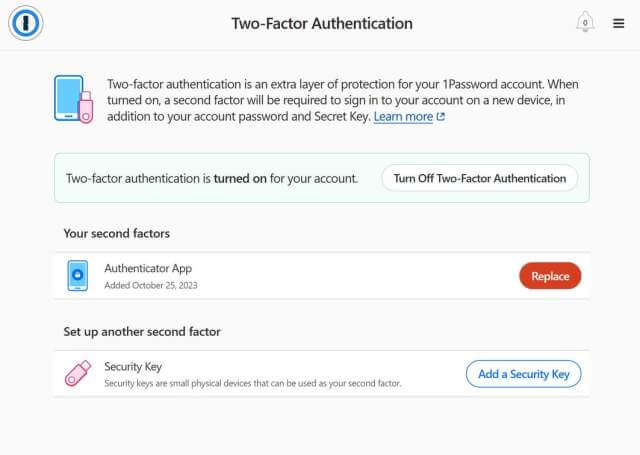
How To Set Two-Factor Authentication in 1Password
To set up 2FA in 1Password, you need to first log in to your 1Password vault on the web version of the vault, not a client.
Go to https://my.1password.com and log into your vault.
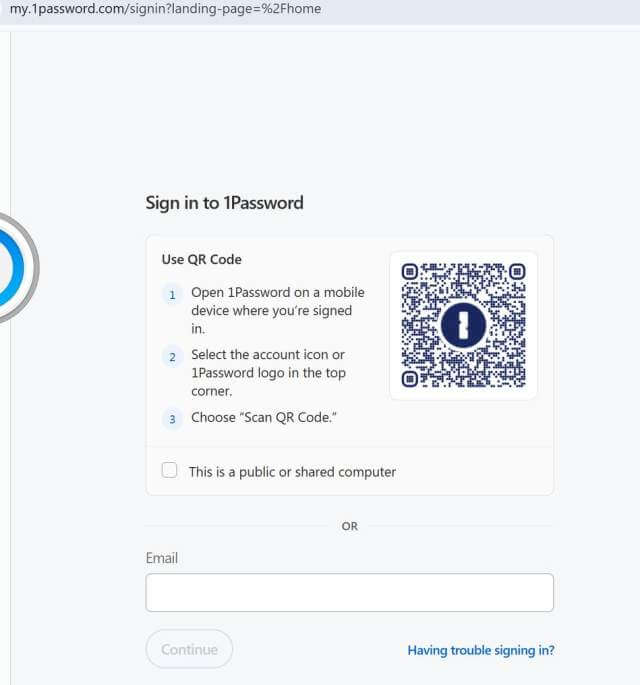
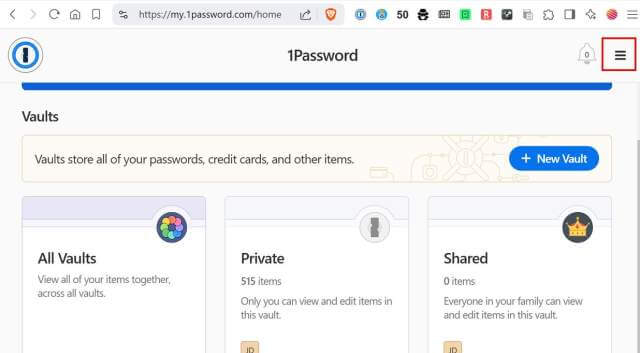
Once logged in, select the hamburger symbol in the upper corner.
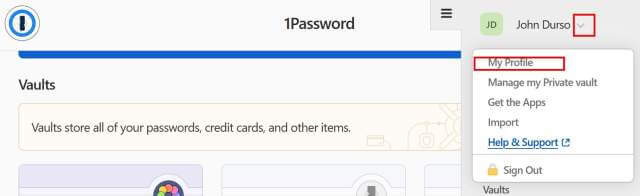
Click the drop down next to your name and select My Profile.
Select More Actions and then Manage Two-Factor Authentication.
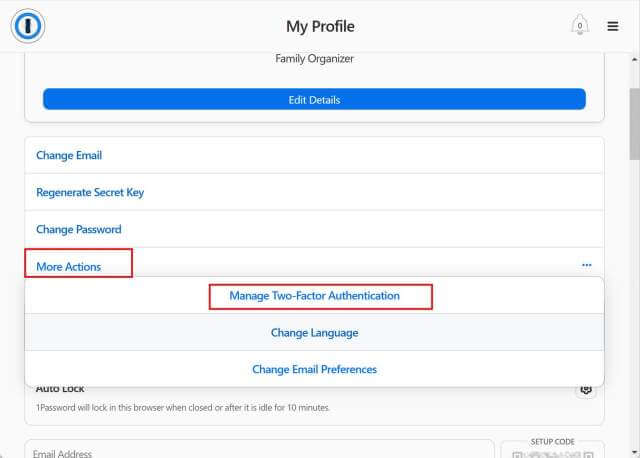
Turn on two-factor authentication(s) if it is not already on.
How To Set Two-Factor Authentication In Bitwarden
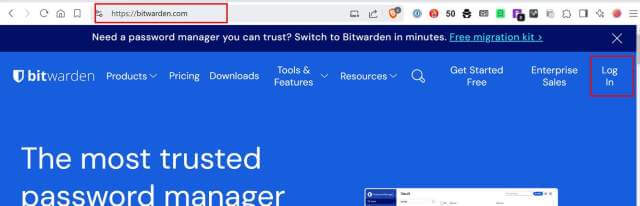
To set up 2FA in Bitwarden, you need to first log in to your Bitwarden vault on the web version of the vault, not a client.
Goto https://bitwarden.com and select Log In in the upper right corner. Now, log in to your vault.
On the left side menu, select Security.
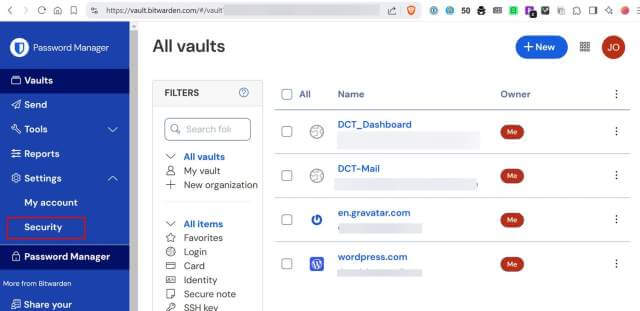
Now, select Two-step login from the top menu and page down to the bottom of the page.
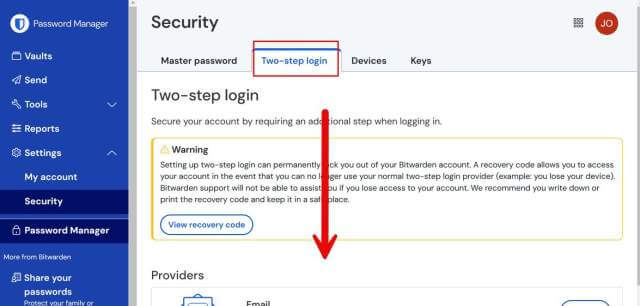
Turn on two-factor authentication(s) if it is not already on.
The Bottom Line
I can not stress enough how important it is to set up two-factor authentication for your password manager. Your password manager is the key to your digital kingdom. Protect it. Don’t make the mistake that Matthew Van Andel did.
—
What happens if a person loses or misplaces the physical hardware key?
Hi Robert,
If using physical hardware keys, you need to buy at least two. And have one as a backup in case you lose one. You need to keep both of then current. I.e. when setting up a new 2fa, you need to do it for both keys.
I have some web sites that refuse to work with their own two factor authorization. They fail to send the Txt, and if you don’t know this, they don’t tell you that you will then need to go directly to e-mail verification, making this very clumsy.
Hi Charless,
The article is about setting 2FA on for Password Managers. But, concerning 2FA on websites, I always choose an authenticator app if it is available. It is more secure, plus you do not need to receive anything from the site. It is not an issue if something is blocking email or txt (or the site is having issues sending out the second factor).
On a Windows10 machine, using Edge and/or DuckDuckGo, is there a procedure to enable 2FA? I’m using the Windows Security PIN, is that enough?