If you’re a Gmail and/or Google account holder, your account is set for a major change.
Google announced earlier this year that it would be forcing millions of account holders to start using 2-Step Verification (aka 2FA), a more secure way of logging in.
- Please read: What Is 2FA & Why You Need It
Google will soon require account holders to use a new 2-step Verification system with some accounts being updated as early as November 9. Two-factor authentication — which Google calls “two-step verification” — requires you to use something in addition to your password to log in to an account. Usually, this “something” is a verification code or confirmation prompt from a smartphone. A username and password will no longer be sufficient.
There’s no official word from Google about when all users will be required to switch over to 2-Step Verification with the company simply saying that individual users will be informed seven days before the change is enforced. Google did confirm last month, however, that it wants more users to have this additional security by the end of 2021:
By the end of 2021, we plan to auto-enroll an additional 150 million Google users in 2SV ~ source
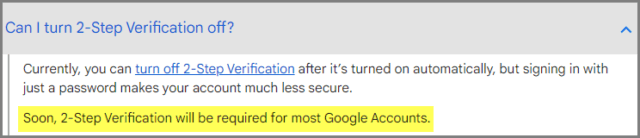
For the time being, 2SV can be turned off via account settings. However, Google has confirmed that this will not remain an option with the timeline for enforcement stated only as “soon“.
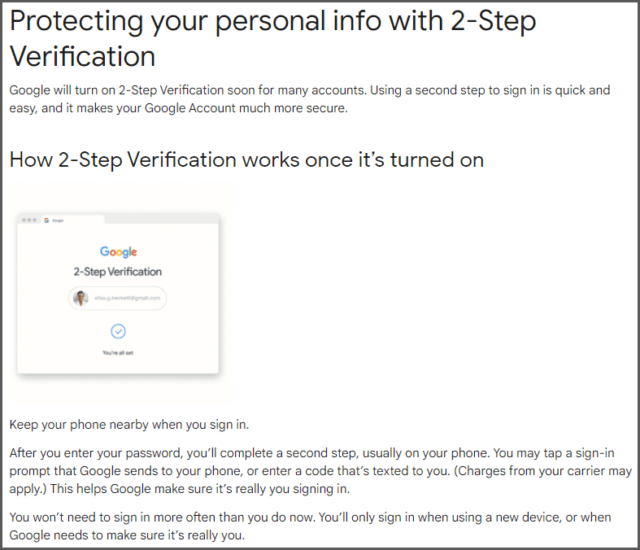
It’s important to note that, under normal circumstances, 2SV will only kick in when there is some doubt over the identity of the person signing in to an account — e.g. when signing in from an unrecognized device and/or browser :
You won’t need to sign in more often than you do now. You’ll only sign in when using a new device, or when Google needs to make sure it’s really you ~ source
BOTTOM LINE:
While I appreciate and understand that 2FA/2SV can be inconvenient for some it does, nonetheless, seriously strengthen account security and I, for one, see this as a positive move by Google.
—
I wonder how they’ll handle users without a cellphone. Like my 95 year young mother who uses a Chromebook and Gmail but not a cellphone. Even calling her landline wouldn’t work because she’s very hard of hearing and wouldn’t get the number right.
Hey Bruce,
I believe Google has plans to release a verification app to cater for folk who don’t own a smartphone. Users can install the app and then use it to verify their identity.
An app? On what device? The computer you are logging-in from?
How secure is that if they are supposedly trying to prevent unauthorized access to ‘personal information’?
I think you’re confusing me with Google.
I don’t really know how it will work but bear in mind that 2SV will not be required when signing in from a recognized device, only when signing in from a different device than normal. Plus, there may well be some sort of security mechanism built-in to the app. As I said, I am not Google so am only conjecturing.
I suggest you read through Google’s announcement, as linked to in the article, for a clearer understanding: https://blog.google/technology/safety-security/making-sign-safer-and-more-convenient/
The whole app concept is typically associated with mobile phone usage, so where will granny install this verification app?
Hey Tony,
Apps are not necessarily specific to mobile devices. Windows 10 includes multiple built-in apps with many more available to download and install.
Besides, according to Bruce’s original comment, ‘granny’ is running a Chromebook, which is essentially all apps
Anyway, as I have already mentioned, I am not Google, if you want to debate the situation, I suggest you contact Google.
2FA is just another way to harvest yet more information from users.
Another way to poke advertising at you and track you wherever you might be.
No-one gets my mobile number (cell phone) unless I want them to have it.
And yesterday I watched how easy it was for your private details to end up in an advertising and tracking system whether you want that to happen or not and completely without your permission.
I was in my local Post Office in Australia. The man was sending a parcel to a child for Xmas. The lady serving him asked if there was a contact detail for the recipient. Now this was a child, underaged, in parental care. Obviously an address is no longer sufficient for sending a parcel. The person has to be notified every few hours that the mail item is proceeding through the system. Who needs this crap infiltrating their lives?
The sender said “Yes she has her own mobile” and proceeded to give the Post Office her private mobile number. How is that good for this small child?
What right did the man have to give out her number? The lady serving him should have said “do you have permission to give me her private number? Maybe her parent’s number would be better.”
But no, the PO is so bent on harvesting people’s personal phone numbers, it has no scruples. It wants to spam everyone with advertising and also send tracking devices(cookies).
It’s these tracking devices that are becoming so popular now that advertising suppliers want access to.
The internet most certainly has become an unsafe place. It’s now full of users and creeps.
Will this still work with an e-mail client (I use Thunderbird) that already has the log-in credentials for G-Mail “remembered” in the password manager? Where would you enter a code, if sent? Am I missing something?
Hey Dave,
Sure will. Even with 2SV set up, if you’re using the same email client on the same device, it should never come into play. As I have said, 2SV generally only kicks in when signing in from a device that is not recognized.
I recently experienced 2SV when dealing with the Canadian government. Tax related matters. The system supposedly sent verification codes to my cell phone several times, but I received nothing. It offered no alternative. For now I am effectively prevented from signing into my account, seeing file details and taxes, pensions, communicating with them, etc. My only option, at present, is to work through the office of my elected member of parliament, which means delays and red tape galore.
I empathise with you Bill. As I read your post I wondered what issues might cause the code to be sent and not received. New phone number was the thing that came to mind. Its new number not yet notified to google.
I assume you have to notify google of a change of phone number from an existing logged-in device. Because if you didn’t there wouldn’t be any point in using this new system. Anyone could log-in to your account and change the number that the code gets sent to.
Then a scenario came to me:-
Say there is an emergency, a catastrophic event ie major bushfires as have been in several places around the world in recent years. Everyone looses everything. People try to keep their few precious belongings with them but often they loose the lot anyway. Which includes their computer, tablet, spare mobile (cell phone) or even their main mobile.
What now? How do they log in? They didn’t get the chance to use an existing device to change where to send the code, ie to a new mobile number because they didn’t know it.
But they are forced to use a community phone or a friends phone once they are at a muster point.
So they try to log-in on these new/strange devices but of course google wants to do the 2SV thing so the code goes to a phone or device which google has in its personal settings, but that’s been burnt.
What happens now?
If you can just change the number willy nilly why can’t crimes do that too?
In each case I was asked to what number I wanted the code to be sent. In the case of the government problem (logging in was really the only problem) I tried over several days. The system would not allow me to change the number to which the code would be sent as it remembered the first number I entered. I did not make an entry mistake, but if I had the system would not allow me to change it. None of these systems allow for contingencies. And there are always contingencies.
Clissa,
The scenario you outlined here is my biggest worry. And there have always been people experiencing this heartache with 2SV even while it wasn’t compulsory.
Agreed, this is a huge problem with 2SV/2FA, one that I have encountered myself. However, this problem is created purely by the ignorance of the account provider.
All 2SV/2FA account providers should include further options for verification purposes, and many do, including a secondary email address. To rely solely on a smartphone number is simply not viable.
I, for one, do not Google, but the way I see it from the bank where I do my online backing, using a desktop computer, they are aware when I use a different computer, or when I upgrade the computer, because the IP address changes, and prior to accessing the accounts, I must answer the security questions I set up years ago. This is their way of making sure the 2-step verification process is enforced. In the past, they phoned me with a verification key, since they did not have my email listed. So most likely Google might follow this path since not everyone uses those Smartphones (an oxymoron), Mindblower!
Yes Mindblower, my banks are easy to deal with, compared to Google’s fortress-like security system. I almost told one the process looked insecure after they reopened my locked account.
Google no longer uses Security Questions, and if you have an account old enough to have those questions on it, they will still ask for secondary verification after you correctly answer the question.
Also note that in the Google world, a 2SV account is harder to recover than a regular account, so when it ceases to be optional you’ll need to be absolutely sure you’re really on top of your game.