BotNets – What are they?
BotNet, short for Robot Network, is one of the scariest types of computer infection extant. We all know the internet is a dangerous place and many security measures must be adhered to in order to maintain some modicum of safety online.
Unfortunately, no matter what a person does in the way of installing firewalls and anti-virus/malware scanners, sometimes the bad guys still manage to get inside.
Before we get started I need to make something perfectly clear. The only sure-fire way to know that you have a clean, no-virus computer is to perform the unpleasant task of re-installing your operating system. Even worse, the only way to completely protect yourself from future infections is to never connect to the internet in the first place. Obviously, this is a totally unacceptable proposition for the majority of us.
Personally, when my internet connection goes “down” I am forced into a distasteful experience; I actually have to pick up a book. Can you imagine?!
A BotNet in its simplest form is quite basic. A bad guy manages to bypass all your security measures and places a bit of software on your computer without your knowledge. This software may watch all your keystrokes, like when you log into your bank account, or when you type in your Social Security Number, and everything else you type. As the key-logger accumulates this information it calls home to the BotMaster (the guy in charge) and sends him/her all this vital information. Of course, Bad Guy now has access to a lot of things you might want to keep very close to the cuff.
Another type of BotNet will use your computer to send SPAM. As the virus spreads, the number of infected computers grows into a huge network. It is estimated that over 3 million SPAM eMails are sent by BotNets every day. Think about that for a moment. It sure torques my engine. Consider the waste and cost of it all – and for what – the greed of a single lazy creature?
BotNets are not limited to non-life-threatening behavior, either. They have been known to attack government sites, infrastructure and other critical computer systems.
These are only a few examples but it surely gives you an inkling of how things work. The potential for damage is mind-boggling. The worst part is that your computer could be helping Bad Guy by contributing to his nefarious deeds and you’d never know it was happening.
Just like you do with your car, it is important to be sensitive to any changes in your computer’s behavior.
Are you part of a BotNet?
I’m sure you’d like to know if you have been compromised somehow. There is no sure-fire way to know, but there may be subtle indications that should make you suspicious and ever-vigilant. If you should discover that you have been infected it demonstrates the unsettling fact that your anti-virus solution has already let you down. It doesn’t matter how high a wall you build, Bad Guy will eventually figure out a way to scale it.
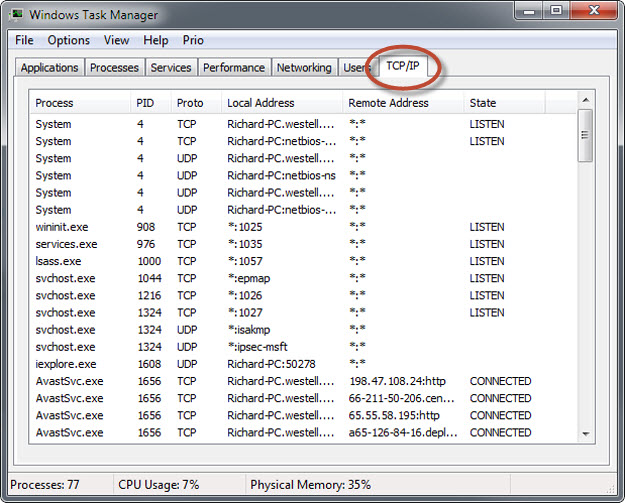
For BotNets to be useful to Bad Guy they have to “call home”. A good way to check your internet activity is by using Task Manager and watching the internet connections. You can quickly open the Task Manager with this keyboard shortcut: <CTRL>-<SHIFT>-<ESC>
A good Task Manager add-on is a utility called Prio that we have discussed before, here on DCT: How To Change CPU Priority – and why. Not only will it give you control over program priorities but it will add a new TCP/IP Tab to the Task Manager. This will show you a list of every active internet connection on your computer. I really like Prio and it’s free!
You can download Prio at this O&K PrintWatch site.
Checking your Internet Connections
Close every single program that has access to the internet:
- All your browsers
- eMail clients
- Windows Gadgets that access the internet
- Social network apps
- Anything else that you can think of
After this, if you see connections being made by unrecognized programs, a little research on your favorite search engine should let you know if these programs are recognized as malicious or safe. Generally, these searches will also explain how to remove the MalWare.
Be forewarned that many of these so-called solutions are nothing more than an attempt by more Bad Guys to lighten your wallet. Never pay for these “solutions”. Every valid method of virus removal can be found free of charge somewhere on the internet. You just have to hunt long enough.
A Free Scanner that Might Help
Microsoft Safety Scanner
This scanner does not require installation; just download it and run it. You will find the Safety Scanner at this download page. To specify a 32-bit or 64-bit download, click the Select Your Version link on the download page:
Conclusions
As I said at the beginning of this post, the only sure-fire way to know you have a clean machine is to do a clean install of your Operating System. That’s simply an unpleasant fact of internet life.
By keeping a close eye on how your computer works and its responsiveness or lack thereof, sluggish internet connections, hijacked browser home pages, pop-up advertising and any other strange behavior, you should have a pretty good idea of whether you have been compromised. It isn’t a perfect solution but it is a step in the right direction.
A good read on this subject is offered at this Prevx Page. It further answers some questions addressed in this article.
“Be careful out there…” ~ Hill Street Blues
Richard

Nice article, Richard. Thanx
Hi Aztony,
You’re welcome and thanks for the kind comment.
Richard