Apple’s operating system, Mac OS X, has long had the reputation of being invulnerable to viruses or any other malicious attacks. Then along came the Flashback attack that affected over a half million Macs.
According to an Apple press release, Apple released a Java update on April 3rd that fixes the Java security flaw for systems running OS X v10.7 (Lion) and Mac OS X v10.6 (Snow Leopard). In addition, Apple is developing software that will detect and remove the Flashback malware.
If you don’t want to wait until Apple provides the software to do so, it’s pretty easy to find out if you have the Flashback malware on your own, according to Topher Kessler’s article on CNET’s website.
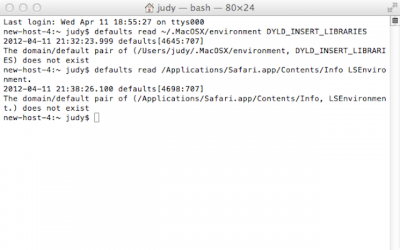
First, open Terminal. It can be found in your /Applications/Utilities folder.

Next, enter the command:
defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES.
If you do not have the Flashback trojan, you should receive a message that this pair does not exist.

The second command that you need to enter is:
defaults read /Applications/Safari.app/Contents/Info LSEnvironment.
Again, you should receive a message that this pair does not exist.
Lastly, enter the command:
defaults read /Applications/Firefox.app/Contents/Info LSEnvironment
Again, you should receive a message that this pair does not exist.

If these pairs are present, these commands will output a path that points to the malware file, which you should see in the Terminal window.
It is possible that prior variants of this trojan are on your Mac. To check for this, enter the command:
ls -la ~/../Shared/.*.so
If no variants exist, you will receive a message that there is no such file or directory.

If you find that you are unfortunate enough to have the Flashback malware, you can find step-by-step instructions here.
